We Surveyed 600 U.S. Tech Workers: Here's What We Learned About The Impact of Access on Productivity

- Role-based, attribute-based, & just-in-time access to infrastructure
- Connect any person or service to any infrastructure, anywhere
- Logging like you've never seen

We surveyed a total of 600 IT, Security, and DevOps professionals from all over the United States, representing organizations of virtually every size to better understand how access impacts productivity and security.
We analyzed how the lack of access affects the output of technical teams and an organization’s security posture.
In this report, you’ll learn:
- How access issues affect employees’ productivity
- Why access is a security threat
- How organizations are dealing with access challenges
- How to bridge the access-productivity gap
Without further ado, take a look at what we discovered below.
Summary of Stats
- 64% of organizations have their productivity impacted on a daily or weekly basis due to access issues.
- 52% of development teams have missed deadlines due to issues with accessing infrastructure.
- 53% of teams report being held accountable for missed deadlines, even if caused by the inability to access the required infrastructure.
- 8% of organizations share access, essentially solving the access problem but at the expense of security, adding exceptional risk to their organizations.
- On a typical day, 73% of employees require 15 or more minutes to get access to infrastructure, with over 30% requiring more than 30 minutes.
- It takes 55% of organizations days or weeks to add new systems to existing access management tools, with an additional 6% taking months.
- 57% of organizations have an SLA that ranges in days or weeks for infrastructure access to be approved and granted.
- 10% of organizations do not have an SLA for access requests at all.
- 57% of organizations require days, weeks, or months to fully off-board technical employees.
- 55% of respondents have maintained backdoor access to systems.
- 53% of organizations have shared credentials across teams.
Let’s get into the detailed breakdown of our findings.
Infrastructure Access Impacts the Productivity of 64% of Organizations
Several organizations experience workflow interruptions and low productivity due to access issues.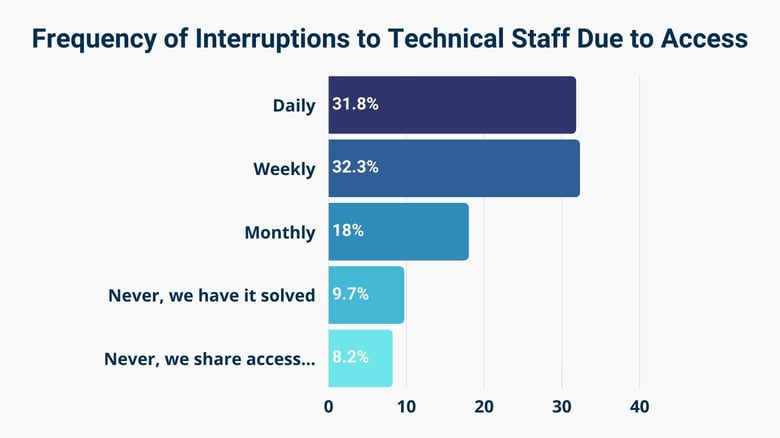
We found that the productivity of almost 32% of organizations is affected by access issues daily, more than 32% weekly, and up to 18% every month.
So, 84% say their employees have decreased productivity due to access challenges. Less than 10% of organizations reported that they resolve their access issues as soon as they arise without impacting employees’ workflows.
These numbers show that employees are impacted by access issues. When there are access challenges, the productivity of technical teams decreases, wait times for access approval go up, completing tasks is made more difficult, and workflows get more complicated.
Sometimes, employees opt for workarounds, creating more security risks.
Due to Lack of Access, 52% of Teams Miss Deadlines
Deadlines are vital in development and project management, and missing one can complicate the overall process.
According to our data, 52% of development teams have missed deadlines due to the lack of timely infrastructure access.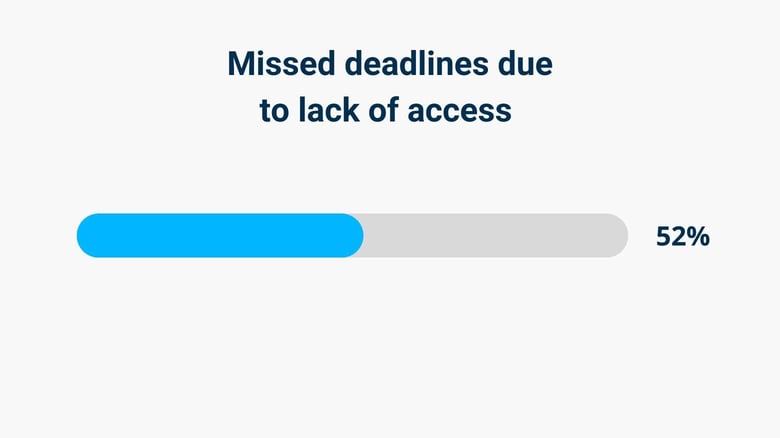
When technical employees need access to tools to do their jobs, they request access to these resources and then must wait for approval. Delayed approval means missed deadlines, which can be problematic for critical projects.
53% of Teams are Accountable for Missed Deadlines
Any technical employee that causes a delay in the completion and deployment of a project will likely be scrutinized.
According to our findings, 53% of teams are held accountable for missed deadlines, even when getting access to the required infrastructure was outside of their control.
When technical employees have to wait days, weeks, or even months before they get access to the tools they need, this leads to unnecessary project delays. And the impact of this accountability on job satisfaction can’t be overlooked.
8% of Organizations Share Access at the Expense of Their Security
Granting employees the access they need is important so they can do their jobs.
We found that 8% of companies share access. This “solves” the access problem but poses security risks to their organizations.
Workarounds like maintaining backdoor access, shadow IT, and shared credentials are sometimes used to grant employees access to the resources they need. However, these workarounds also open the door to potential security threats.
73% of Employees Access Infrastructure After More Than 15 Mins
Getting access to systems when required makes a huge difference in productivity level. 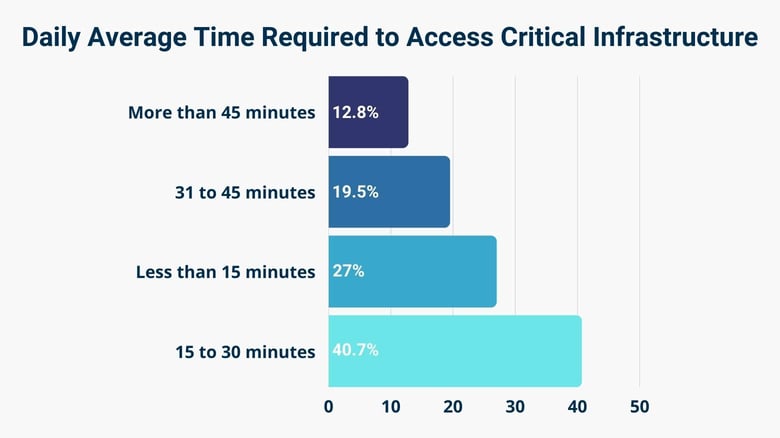
However, we found that 73% of employees require 15 minutes or more to access critical infrastructure. Only 27% of employees get access in less than 15 minutes.
Over 40% of employees wait 15 to 30 minutes, 19% require 31 to 45 minutes, and more than 12% wait longer than 45 minutes.
The more technical teams need to wait before getting access to the resources they need, the greater the delays to complete time-sensitive projects.
61% of Companies Experience Delays in Rolling Out New Tools
Organizations purchase new tools for better performance. But, how long does it take to get them ready for use? Any delays in integrating new tools to the existing tech stack will lead to inefficient operations, reduced productivity, and ultimately, poor ROI (return on investment).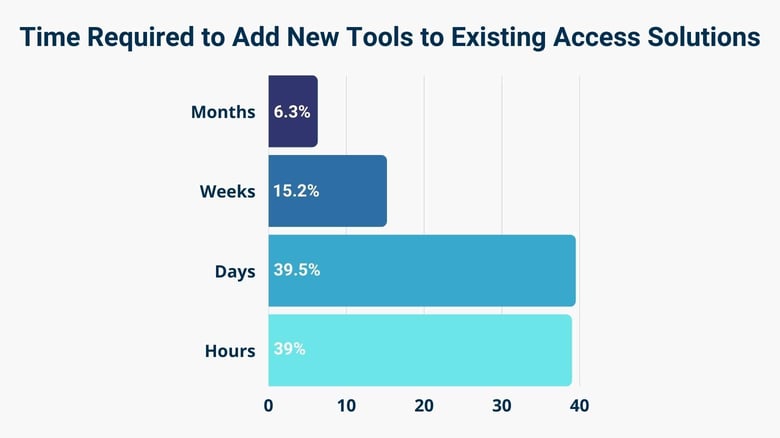
We found that it takes 55% of organizations days and sometimes weeks to add new systems to their existing access management tools. Over 6% of companies require months.
Although up to 61% of organizations suffer delays when adding new systems to existing access tools, 39% of companies resolve this within hours.
When new tools and systems are available without proper access management solutions, they are susceptible to being hijacked by malicious users. And the actions of such users could affect the security posture of an organization.
57% of Organizations Have SLAs of Days or Even Weeks
With SLAs, employees and end-users know when organizations will grant the required infrastructure access.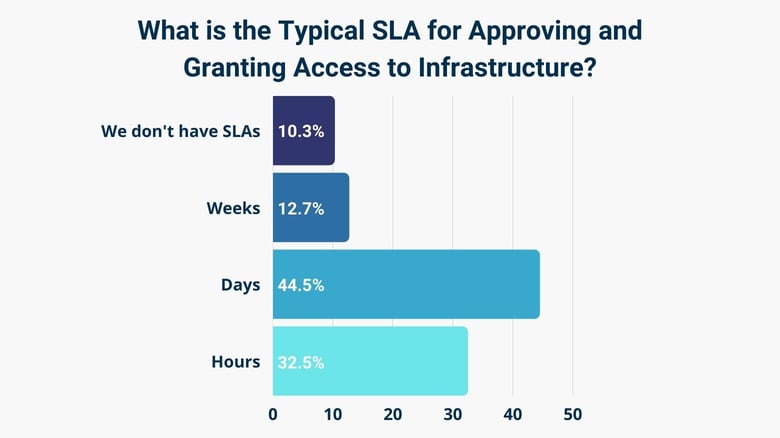
From our survey, 57% of organizations have an SLA of days or weeks to approve and grant access to infrastructure. This is a huge spike from the 32% that have an SLA granting access within hours.
It could be demoralizing when technical employees sit at their desks for days, sometimes weeks, waiting for access to the resources they need to do their jobs. Without SLAs, there's no commitment to employees and end-users with regard to how quickly the necessary infrastructure access will be granted.
10% of Organizations Don’t Have SLAs at All
Without SLAs, there's no commitment to employees and end-users with regard to how quickly the required access will be approved.
From our findings and the chart in stat #7 above, more than 10% of organizations do not have an SLA for access requests at all.
What this means is that employees who require access to specific resources won’t know when their requests will be approved.
57% of Organizations Need a Lot of Time to Properly Offboard
Now and then, employees are given the privileges they need to access required infrastructure - not just employees but also users and contractors. Once they’ve completed a project or perhaps left the company, it is necessary to offboard them quickly. 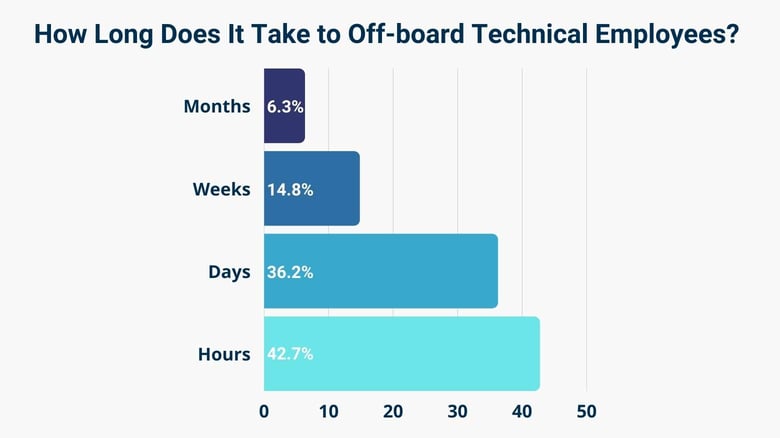
We found that 57% of organizations require days, weeks, and even months to fully off-board technical employees.
Specifically, 36% of organizations spend days offboarding technical contractors and employees, 15% take weeks, and 6% spend months doing this.
If an employee already has access to complete their tasks or do their jobs, it’s important to revoke this access once the task is completed or they have parted ways with the company. Delayed offboarding can open the door to security attacks on these zombie accounts.
55% of Respondents Have Maintained Backdoor Access to Systems
When technical teams can't access the systems they need, they sometimes resort to workarounds to solve their access challenges. One such workaround is utilizing backdoor access. 
We found that 55% of teams have maintained backdoor access to ensure they can carry out their job duties. These backdoors were initially created to get around the systems and procedures put in place to ensure security requirements are met.
However, these workarounds slow down developers who need timely access to their tools in order to complete their projects and create security risks such as stealing, manipulating, or destroying sensitive information.
53% Have Shared Credentials Across Teams
Just like “maintaining backdoor access,” shared credentials have their risks. Organizations and technical employees find workarounds like shared credentials to solve access challenges, which in turn could lead to serious security issues.
According to our survey, 53% of organizations have shared credentials across teams, and over 40% of teams embrace another type of workaround — shadow IT.
But, how are shared credentials a security threat?
If several employees have admin access or share password credentials across multiple systems and accounts, it makes it difficult to audit and manage privileged accounts. This could lead to mishandling, phishing, or brute force attacks through guessable passwords. This practice also goes against secuirty policies put in place for compliance.
Conclusion
The benefits of addressing the Access-Productivity Gap are tangible and include improving efficiency, streamlining access management workflows, and simplifying onboarding and offboarding. The research shows that it also has a tangible impact on security and compliance — enabling each organization to reduce risk, while also simplifying compliance and audit requests.
It’s important to focus on the People-First Access approach by providing technical staff with direct access to the infrastructure they need based on least-privilege access.
This Access-Productivity Gap report was produced by StrongDM and the survey was conducted by Pollfish.
If you'd like to learn more about how this survey was conducted or want full details of our findings, you can download the survey report here.
About the Author
Komron Rahmonbek, SEO Manager, has been managing SEO initiatives for companies and clients from different industries for more than five years. Evangelizing SEO within organizations and educating other team members on the best practices is his passion. Komron occasionally shares his expertise on various blogs and publications. To contact Komron, visit him on LinkedIn.

You May Also Like