MySQL
Last modified on April 2, 2025
To add MySQL or MySQL (mTLS) as a Datasource in the Admin UI, set the following configuration properties. For more information, see our main guide, Add a Datasource.
The mutual TLS (mTLS) version of this datasource Type is available if you need certificates to reach the MySQL port, rather than username and password. This is of particular importance with GCP-hosted MySQL, for which it is the default expected behavior.
Configuration Properties
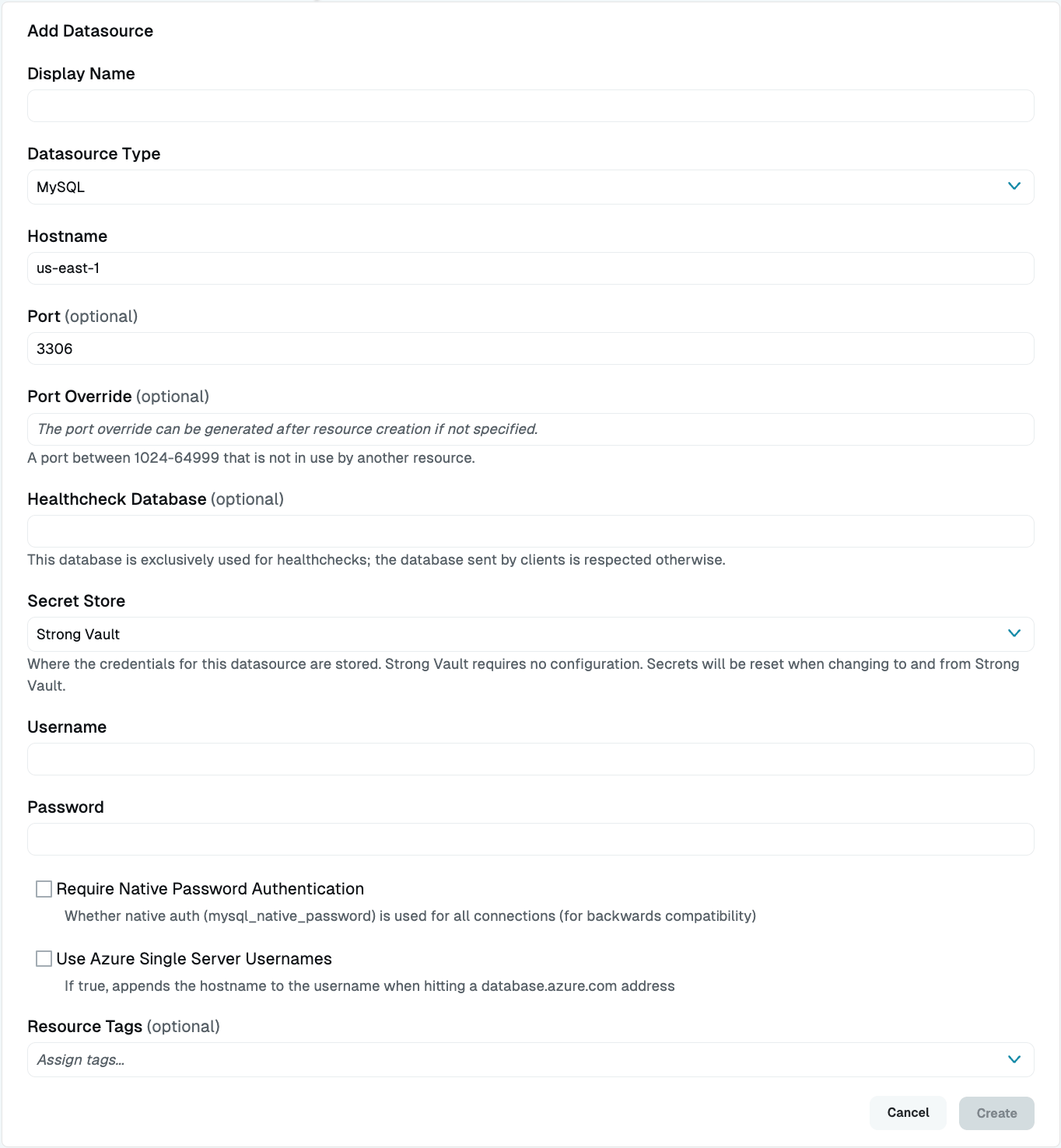
- Display Name (Required): Enter a meaningful name for this resource, such as “MySQL.” This name displays throughout StrongDM. Do not include special characters like quotes (") or angle brackets (< or >).
- Datasource Type (Required): Select MySQL.
- Proxy Cluster (Required): This option defaults to “None (use gateways)”. If you are using proxy clusters, select the appropriate cluster to proxy traffic to this resource.
- Hostname (Required): Enter the hostname. Note that it must be accessible to a gateway or relay.
- Port (Optional): Enter the port to connect to the resource (default: 3306).
- Port Override (Optional): After this datasource has been created, this field will be automatically filled with a port between 1024-59999 that is not in use by another datasource. You can optionally overwrite it with your own preferred port later in the Port Overrides settings.
- Database (Required): Enter the name of the database you will be connecting to with this datasource.
- Secret Store (Optional): This field lets you specify where the credentials for this resource are stored. The default Secret Store type is Strong Vault. Selecting any other Secret Store type causes properties unique to that secret store to appear, such as Username (path), Password (path), and so forth. For more detailed information about path to the secrets you have stored in a particular secret store, see the Secret Store integration configuration guide for the one you are using.
- Username (Required): This field is shown when Secret Store integration is not configured for your organization, or when it is and StrongDM is the selected Secret Store type. Enter the username of the user that will be used for this datasource.
- Username (path) (Required): If Secret Store integration is configured for your organization and you selected a Secret Store type that is not StrongDM, enter the path to the secret in your secret store (for example,
path/to/credential?key=optionalKeyName). The key argument is optional. - Password (Required): This field is shown when Secret Store integration is not configured for your organization, or when it is and StrongDM is the selected Secret Store type. Enter the password of the user that will be used for this datasource.
- Password (path) (Required): If Secret Store integration is configured for your organization and you selected a Secret Store type that is not StrongDM, enter the path to the secret in your Secret Store (for example,
path/to/credential?key=optionalKeyName). The key argument is optional. - Require Native Password Authentication (Optional): If the resource requires the use of
mysql_native_passwordfor all connections, enable this option. This option is available for backwards compatibility with prior MySQL versions. - Use Azure Single Server Usernames (Optional): If selected, the hostname will be appended to the username when interacting with a
database.azure.comaddress. - Resource Tags (Optional): Assign tags to the datasource by entering key-value pairs in the format
<KEY>=<VALUE>(for example,env=dev).
MySQL (mTLS) Configuration Properties
- Display Name (Required): Enter a meaningful name for this resource, such as “MySQL mTLS.” This name displays throughout StrongDM. Do not include special characters like quotes (") or angle brackets (< or >).
- Datasource Type (Required): Select MySQL (mTLS).
- Hostname (Required): Enter the hostname. Note that it must be accessible to a gateway or relay.
- Port (Optional): Enter the port to connect to the resource (default: 3306).
- Port Override (Optional): After this datasource has been created, this field will be automatically filled with a port between 1024-59999 that is not in use by another datasource. You can optionally overwrite it with your own preferred port later in the Port Overrides settings.
- Database (Required): Enter the name of the database you will be connecting to with this datasource.
- Secret Store: This field lets you specify where the credentials for this resource are stored. The default Secret Store type is Strong Vault. Selecting any other Secret Store type causes properties unique to that Secret Store to appear, such as Username (path), Password (path), and so forth. For more detailed information about path to the secrets you’ve stored in a particular Secret Store, see the Secret Store integration configuration guide for the one you are using.
- Username (Required): This field is shown when Secret Store integration is not configured for your organization, or when it is and StrongDM is the selected Secret Store type. Enter the username of the user that will be used for this datasource.
- Username (path) (Required): If Secret Store integration is configured for your organization and you selected a Secret Store type that is not StrongDM, enter the path to the secret in your Secret Store (for example,
path/to/credential?key=optionalKeyName). The key argument is optional. - Password (Required): This field is shown when Secret Store integration is not configured for your organization, or when it is and StrongDM is the selected Secret Store type. Enter the password of the user that will be used for this datasource.
- Password (path) (Required): If Secret Store integration is configured for your organization and you selected a Secret Store type that is not StrongDM, enter the path to the secret in your Secret Store (for example,
path/to/credential?key=optionalKeyName). The key argument is optional. - Server CA (Required): This field is shown when Secret Store integration is not configured for your organization, or when it is and StrongDM is the selected Secret Store type. Paste the server certificate (plaintext or Base64-encoded), or import a PEM file.
- Server CA (path) (Required): If Secret Store integration is configured for your organization and you selected a Secret Store type that is not StrongDM, enter the path to the secret in your Secret Store (for example,
path/to/credential?key=optionalKeyName). The key argument is optional. - Client Certificate (Required): This field is shown when Secret Store integration is not configured for your organization, or when it is and StrongDM is the selected Secret Store type. Paste the client certificate (plaintext or Base64-encoded), or import a PEM file.
- Client Certificate (path) (Required): If Secret Store integration is configured for your organization and you selected a Secret Store type that is not StrongDM, enter the path to the secret in your Secret Store (for example,
path/to/credential?key=optionalKeyName). The key argument is optional. - Client Key (Required): This field is shown when Secret Store integration is not configured for your organization, or when it is and StrongDM is the selected Secret Store type. Paste the client key (plaintext or Base64-encoded), or import a PEM file.
- Client Key (path) (Required): If Secret Store integration is configured for your organization and you selected a Secret Store type that is not StrongDM, enter the path to the secret in your Secret Store (for example,
path/to/credential?key=optionalKeyName). The key argument is optional. - Server Name (Required): Enter the server name. For GCP, for example, the server name is the connection name of your instance in GCP without the region (for example,
example-sandbox:my-instance-mtls-mysql). For non-GCP instances, the server name is the hostname/DNS name. - Require Native Password Authentication (Optional): Whether your resource uses
mysql_native_passwordfor all connections. This option is available for backwards compatibility with prior MySQL versions. - Use Azure Single Server Usernames (Optional): If selected, the hostname will be appended to the username when interacting with a
database.azure.comaddress. - Resource Tags (Optional): Assign tags to the datasource by entering key-value pairs in the format
<KEY>=<VALUE>(for example,env=dev).