Remote Identity for SSH
Last modified on March 28, 2024
You can use a Remote Identity, instead of a leased credential, with StrongDM to proxy authentication with your SSH resources. Actions are executed via the user’s account (that is, the Remote Identity) with the resource, while user-level auditing and monitoring occur on the resource side via native logging.
Utilizing a Remote Identity results in your native server logs identifying the particular user performing an action, rather than identifying all actions conducted via StrongDM connections as being performed by the single leased user account. The username employed is the user’s Remote Identity set in their StrongDM user account.
Set Up Remote Identities
Set up your server and user account
- Create your server if you do not have one already.
- Create or identify an account on the server that StrongDM can use to check its health. This user should have SSH access to the machine. Built-in accounts such as
ubuntuorec2-userare a good choice.
Add the resource in StrongDM
In the Admin UI, create the resource by going to Infrastructure > Servers and clicking Add server.
Select SSH (Certificate Based) server or SSH (Certificate Based with User Provisioning) as the server type.
Both server types use certificate authentication. The difference between the two is that the SSH (Certificate Based with User Provisioning) type provisions users and adds or updates their group membership to match the Remote Identity that is used to connect to the server.Set all required properties for the selected server type (SSH (Certificate Based) server or SSH (Certificate Based with User Provisioning)). Pay particular attention to the following:
- For Authentication, set Remote Identities.
- For Healthcheck Username, set the SSH user account name (for example,
ubuntu).
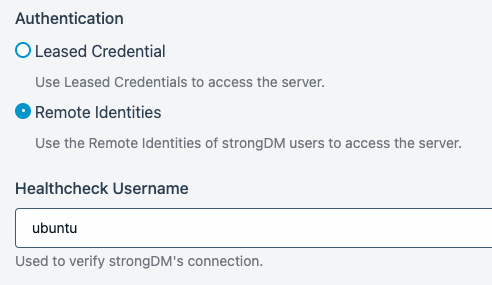
SSH Certificate Based Server Settings with Remote Identities as Authentication Type After you have set all the required properties, click Create to save the resource.
Add the Remote Identity to the user’s settings
In the Admin UI, go to Access > Users and select the user who is going to use a Remote Identity.
In that user’s settings, for Remote Identity > Username, enter the SSH user account name (for example,
ubuntu).For Remote Identity > Roles, optionally enter the name of the group that the user should be in.
If Remote Identities are configured on a resource, a Remote Identity also must be set for any user that is given access to that resource. If it is not, that user is unable to connect to the resource.Individual users must have their own accounts on the server. The account name must match the Remote Identity value specified in the user’s settings.
Configuration is now complete. You may now start using Remote Identities to authenticate with your SSH resource.