Logging Scenario - Send Local Logs to a Splunk Indexer
Last modified on March 24, 2023
On this page
Scenario: you want to save gateway/relay logs to a Splunk Indexer. This guide presents a simple method to send all gateway/relay logs to a Splunk Indexer.
As with all gateway/relay logs, the logs stored on the gateway/relay will not include Admin UI activities, which can be accessed via the
sdm audit activities command.Setting up the export
Enable relay logging in the Admin UI under Settings / Log Encryption & Storage. Ensure logging is set to FILE.
Configure your indexer to receive the date from the forwarder:
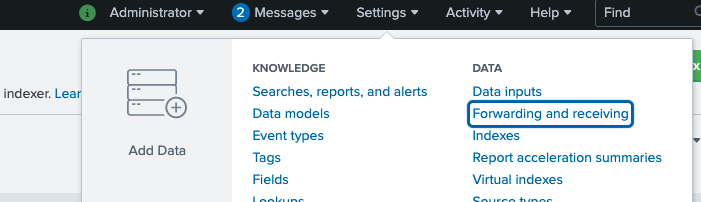
Configure Indexer 1 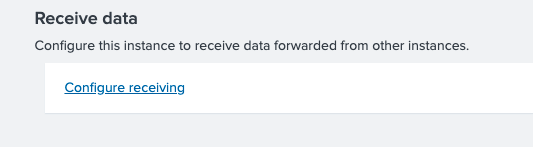
Configure Indexer 13 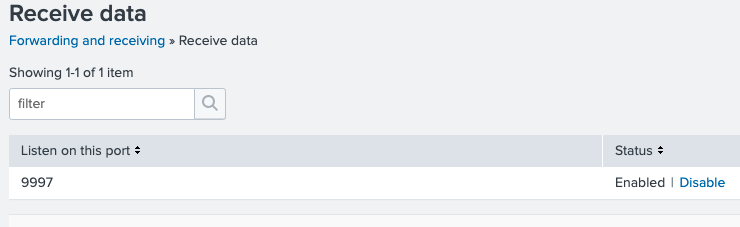
Configure Indexer 3 Create an index for StrongDM, called “sdm_index” in this example:
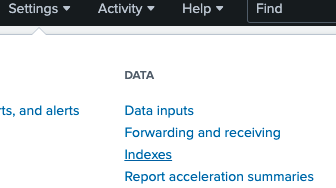
Create Index 1 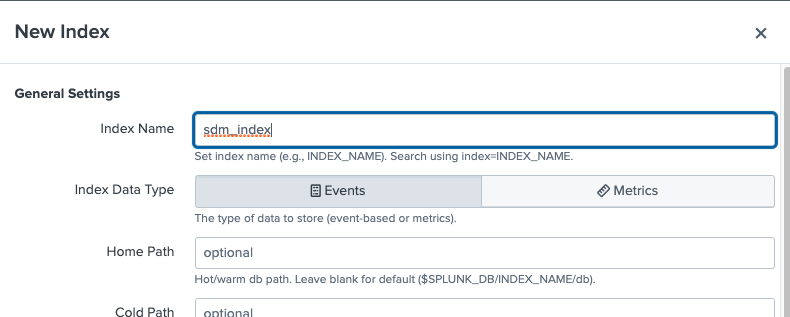
Create Index 2 
Create Index 3 Install the forwarder, then configure the monitor.
wget -O splunkforwarder-8.1.3-63079c59e632-linux-2.6-x86_64.rpm 'https://www.splunk.com/bin/splunk/DownloadActivityServlet?architecture=x86_64&platform=linux&version=8.1.3&product=universalforwarder&filename=splunkforwarder-8.1.3-63079c59e632-linux-2.6-x86_64.rpm&wget=true' sudo rpm -ihv splunkforwarder-8.1.3-63079c59e632-linux-2.6-x86_64.rpm export PATH=$PATH:/opt/splunkforwarder/bin splunk startYou’ll be asked to set the admin password on the first run ofsplunk start.splunk list forward-server Active forwards: ec2-34-210-43-66.us-west-2.compute.amazonaws.com:9997 Configured but inactive forwards: None splunk add monitor /home/ec2-user/.sdm/logs/ -index sdm_index -sourcetype sdm splunk list monitor [...] /home/ec2-user/.sdm/logs /home/ec2-user/.sdm/logs/relay.1616439304.0.log /home/ec2-user/.sdm/logs/relay.1616439311.0.log /home/ec2-user/.sdm/logs/relay.1616595755.0.log /home/ec2-user/.sdm/logs/relay.1616604787.0.log /home/ec2-user/.sdm/logs/relay.1616652500.0.log [...]You can search for “sdm_index” on the indexer’s search:
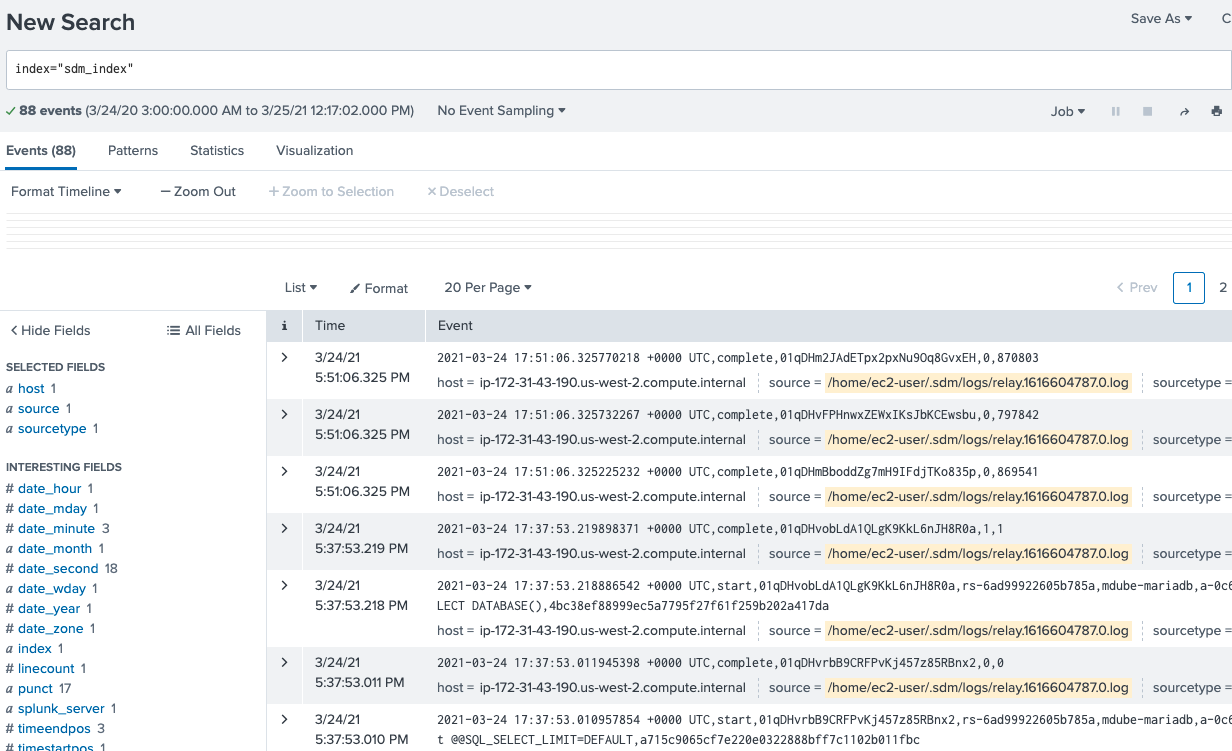
Indexer Search