All technical users use a single control plane for frictionless privileged access across a company’s entire stack, no matter how diverse. DevOps teams can finally implement infrastructure as code.
Elevate Your Security with
Continuous, Zero Trust Authorization



All technical users use a single control plane for frictionless privileged access across a company’s entire stack, no matter how diverse. DevOps teams can finally implement infrastructure as code.



All technical users use a single control plane for frictionless privileged access across a company’s entire stack, no matter how diverse. DevOps teams can finally implement infrastructure as code.



All technical users use a single control plane for frictionless privileged access across a company’s entire stack, no matter how diverse. DevOps teams can finally implement infrastructure as code.



All technical users use a single control plane for frictionless privileged access across a company’s entire stack, no matter how diverse. DevOps teams can finally implement infrastructure as code.





Meet StrongDM: Your Partner in Zero Trust Privileged Access
The digital world is constantly changing, and so are the threats that come with it. StrongDM takes on those challenges head-on with a straightforward approach to Zero Trust security. We make sure that the right people get access to the resources they need, exactly when they need them — no more, no less.
Strong Policy Engine
Our Cedar-based policy engine is at the heart of our Zero Trust approach, allowing you to create and enforce fine-grained access controls. Tailor who gets access, to what, and when — ensuring the right people have the right access at the right time.
Frustration-free Access
We believe security shouldn’t slow you down. That’s why StrongDM is designed for simplicity, enabling users to securely access the resources they need without frustration. It’s about making your day smoother, not more complicated.
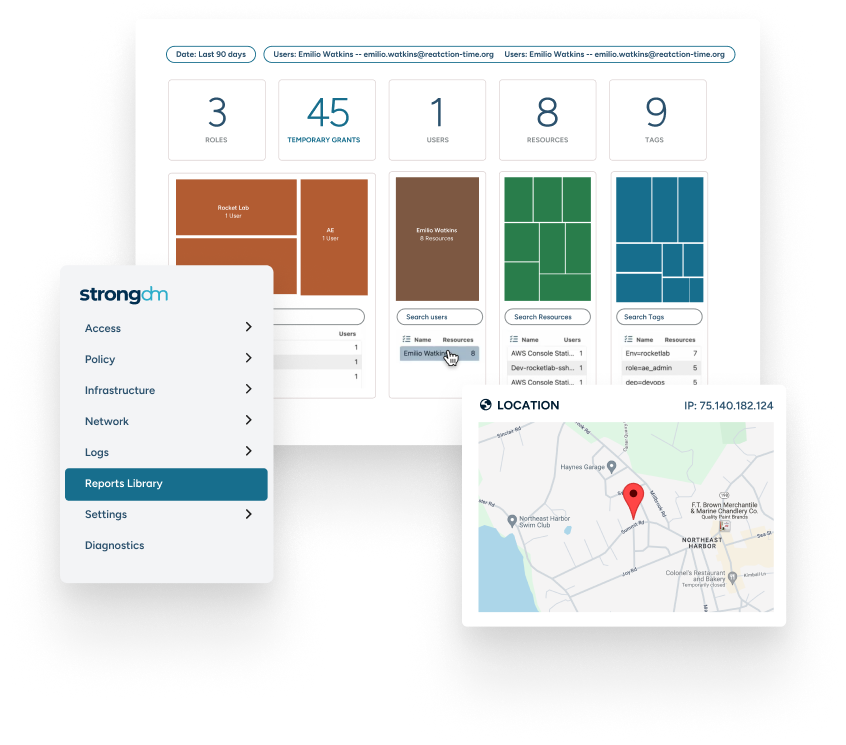
Complete Visibility
With StrongDM, you get a bird’s-eye view of your digital environment. Track who accessed what and when, ensuring transparency across your infrastructure. It’s the clarity you need to make informed security decisions.
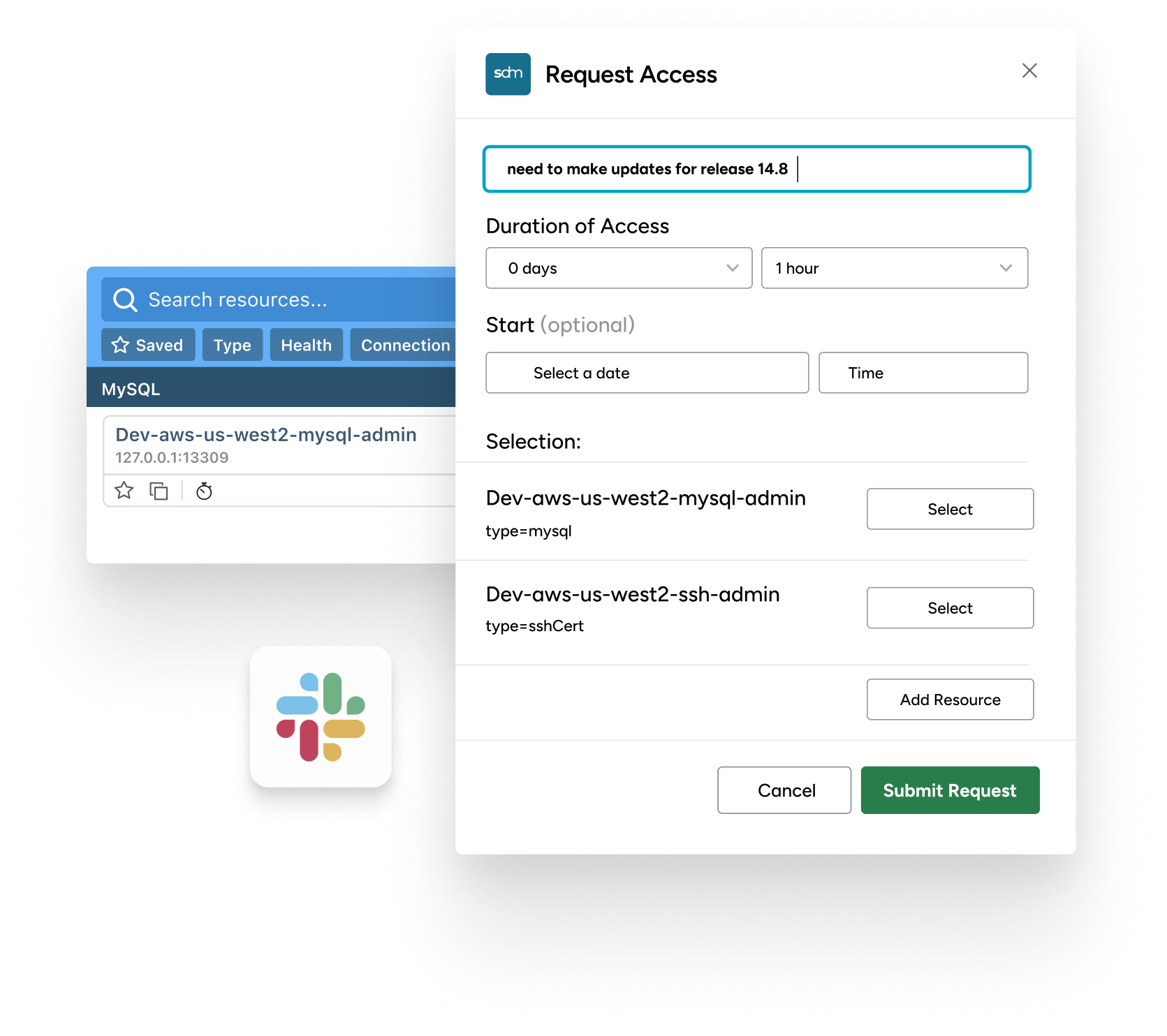
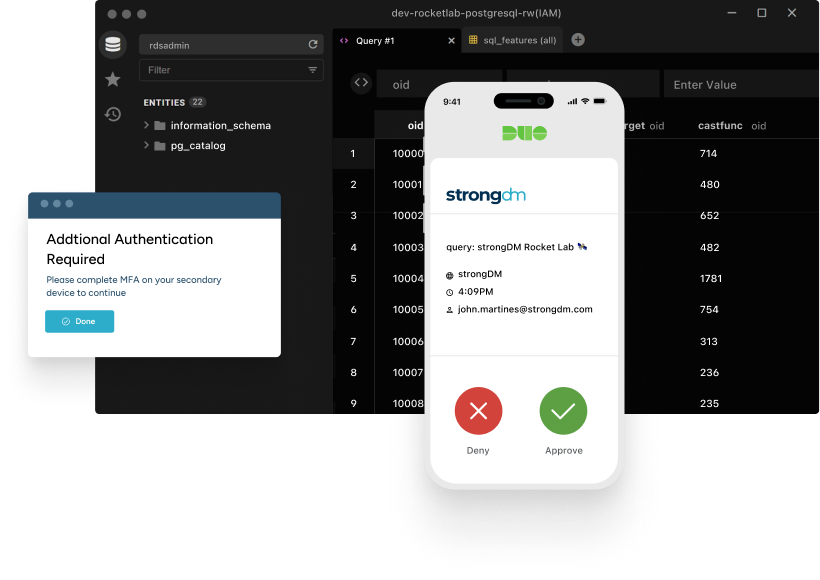
Workflows for Just-In-Time Access
Our workflows empower your team with just-in-time access, reducing the attack surface without hindering productivity. Access is granted when needed and pulled back when done, all automatically.

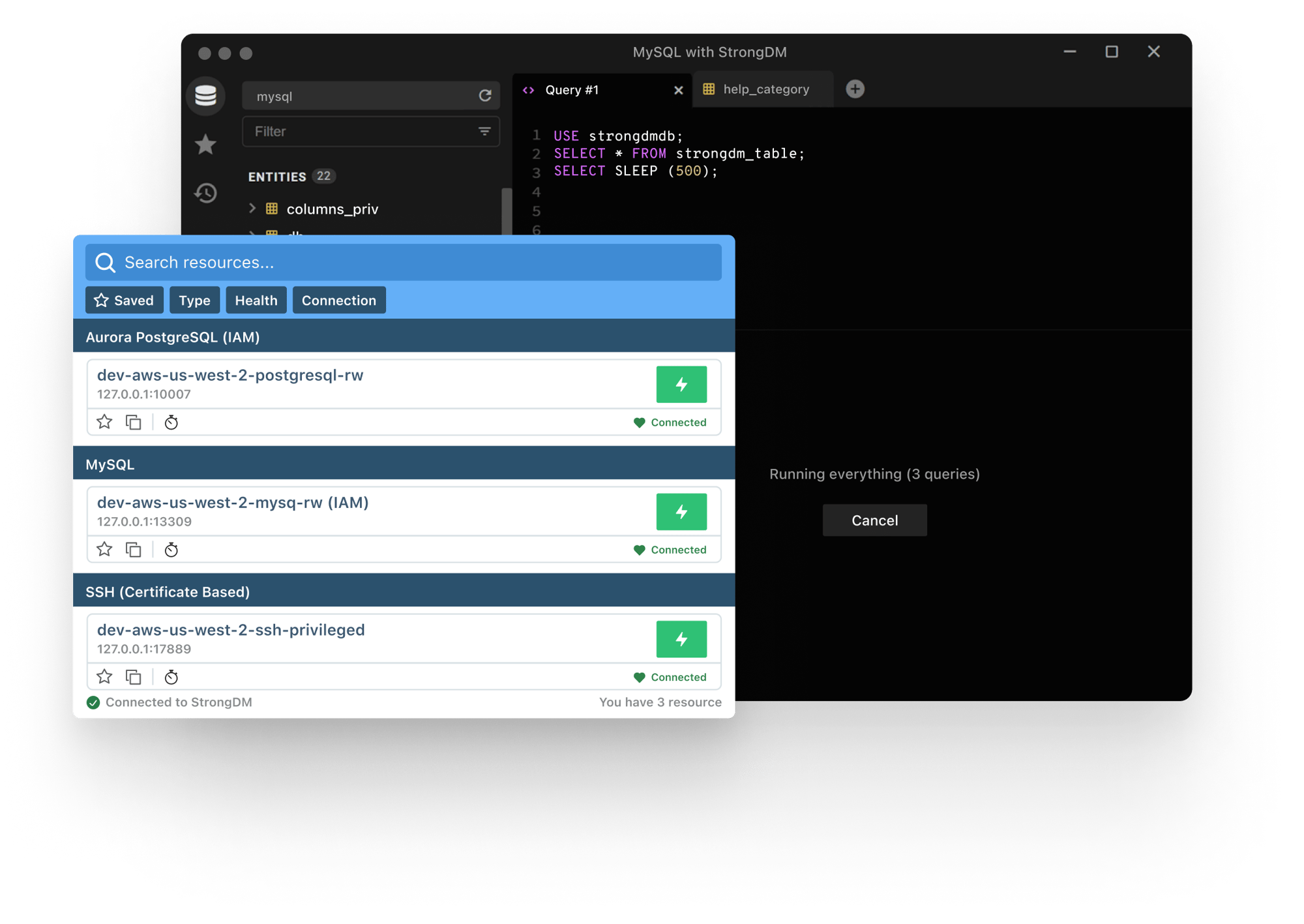
No Migration or Coding Needed
Want to keep using your existing vaults or secret stores? Go for it. StrongDM can be integrate with existing tools and the policies can be applied without requiring you to recode your apps or move your secrets.
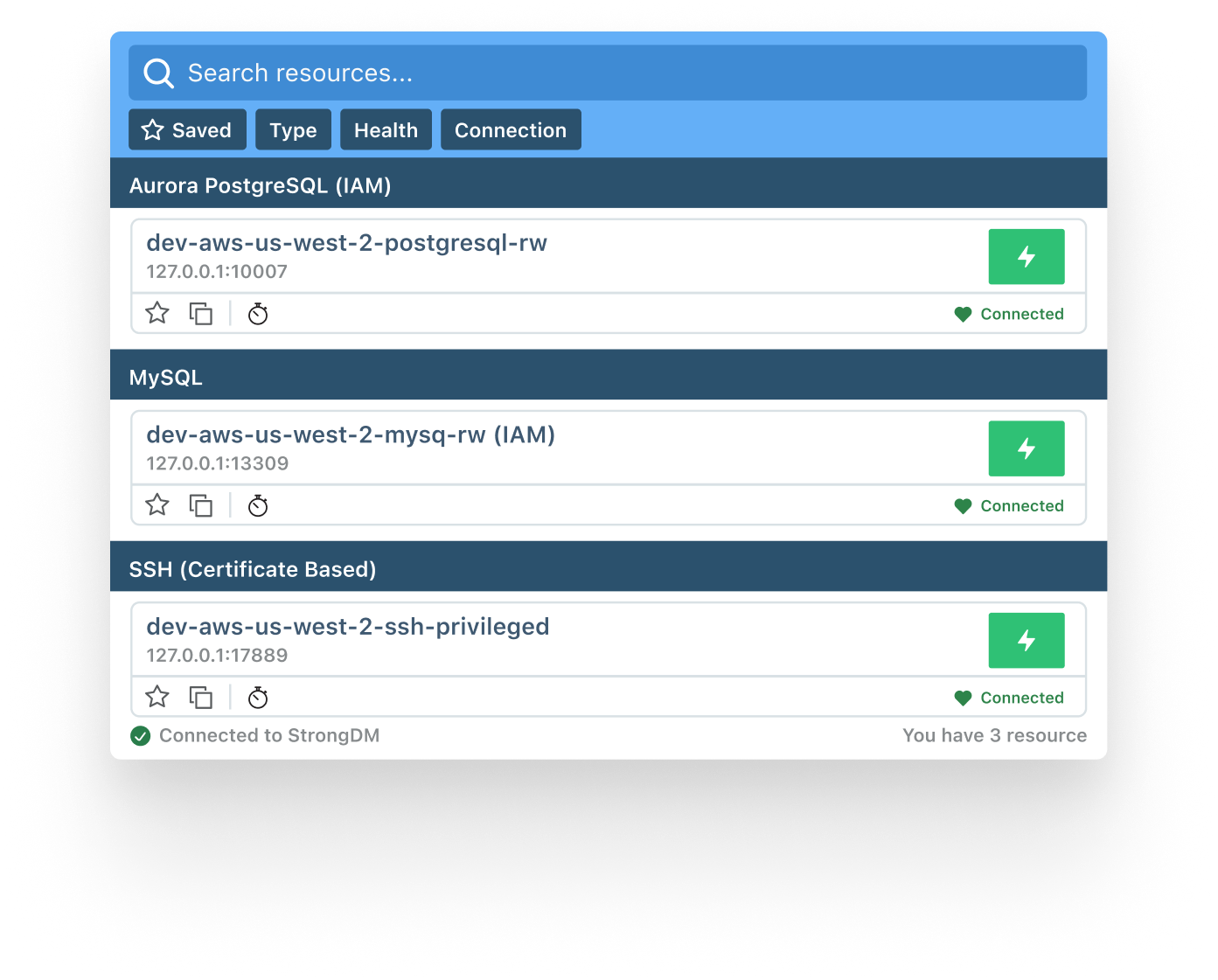
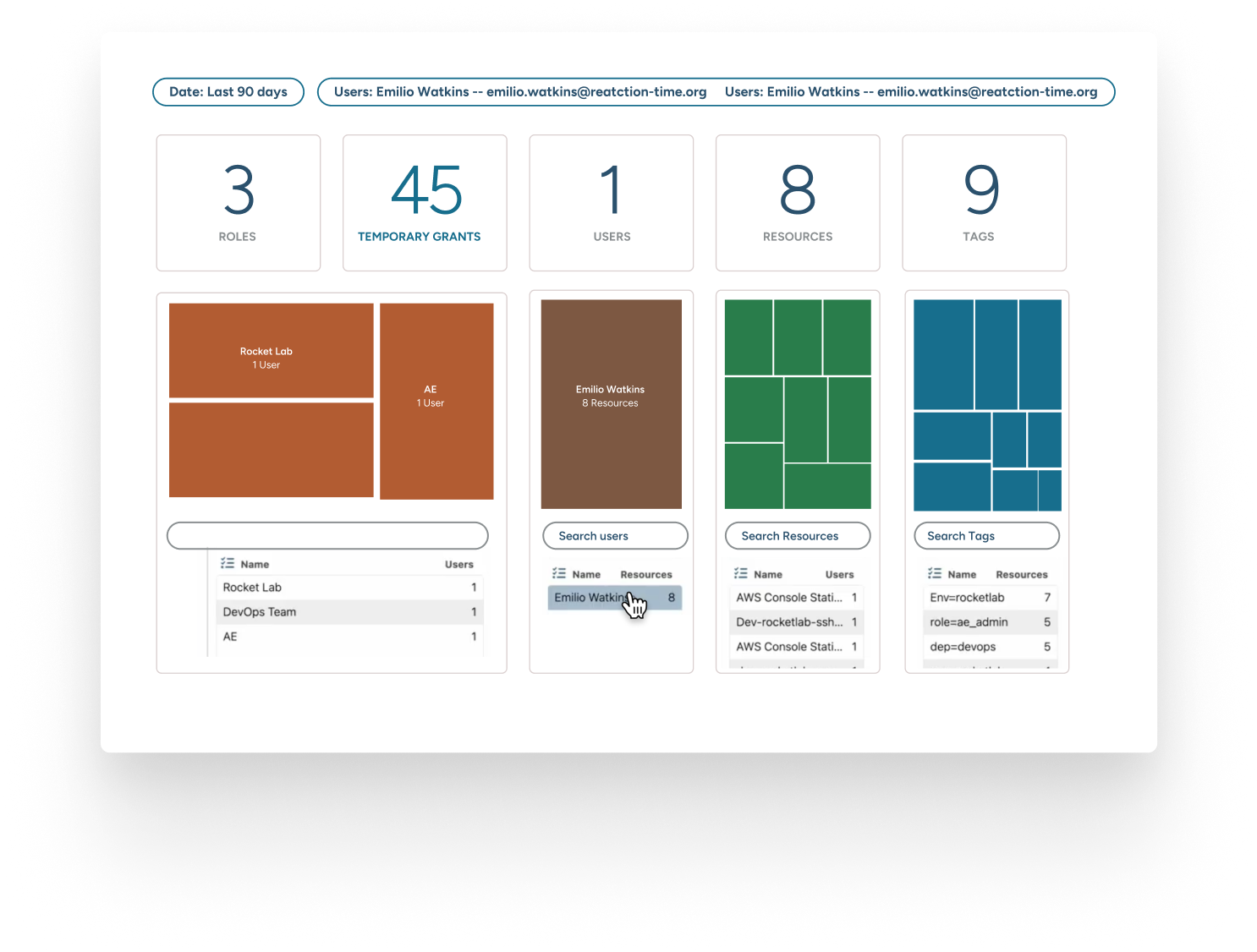

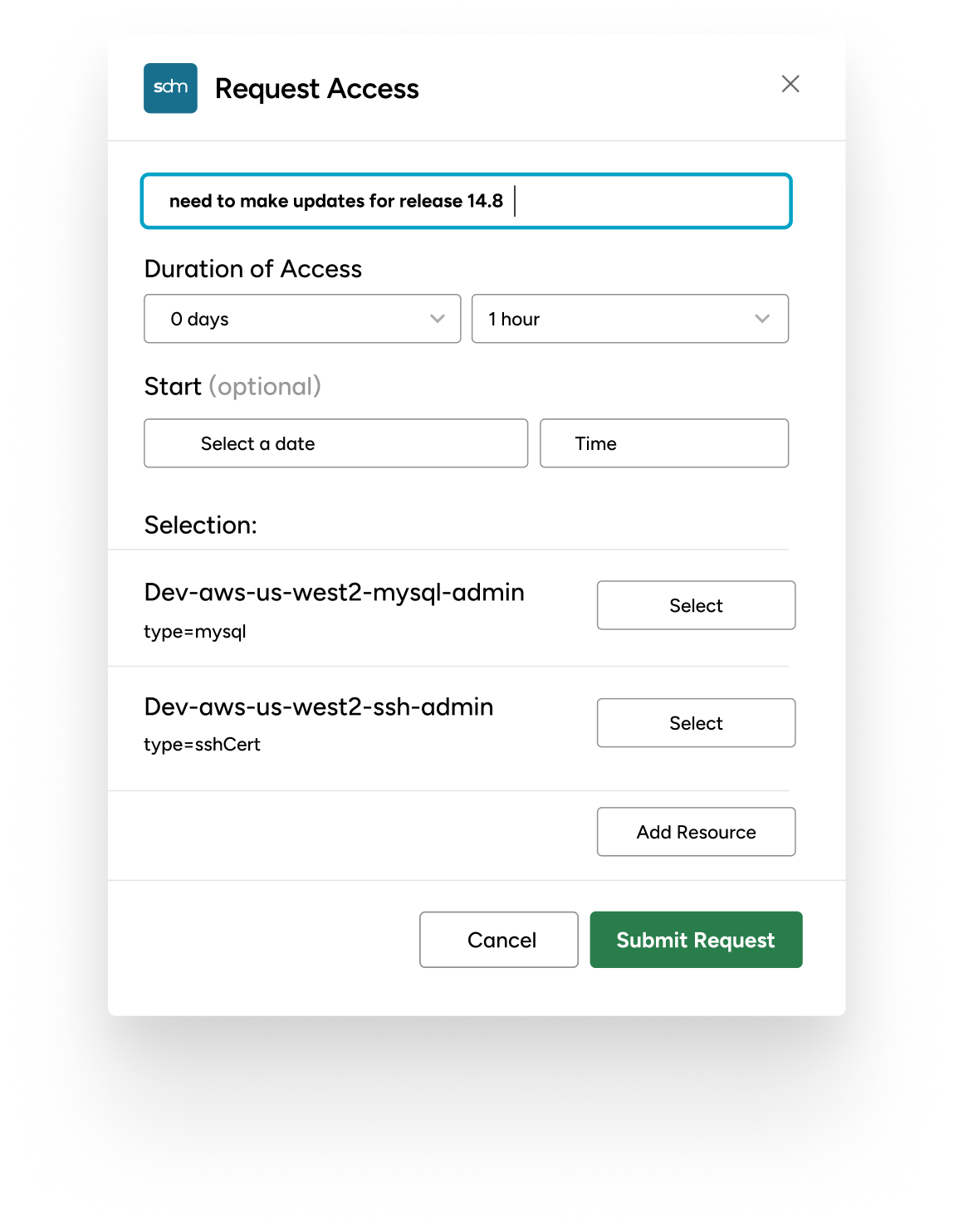
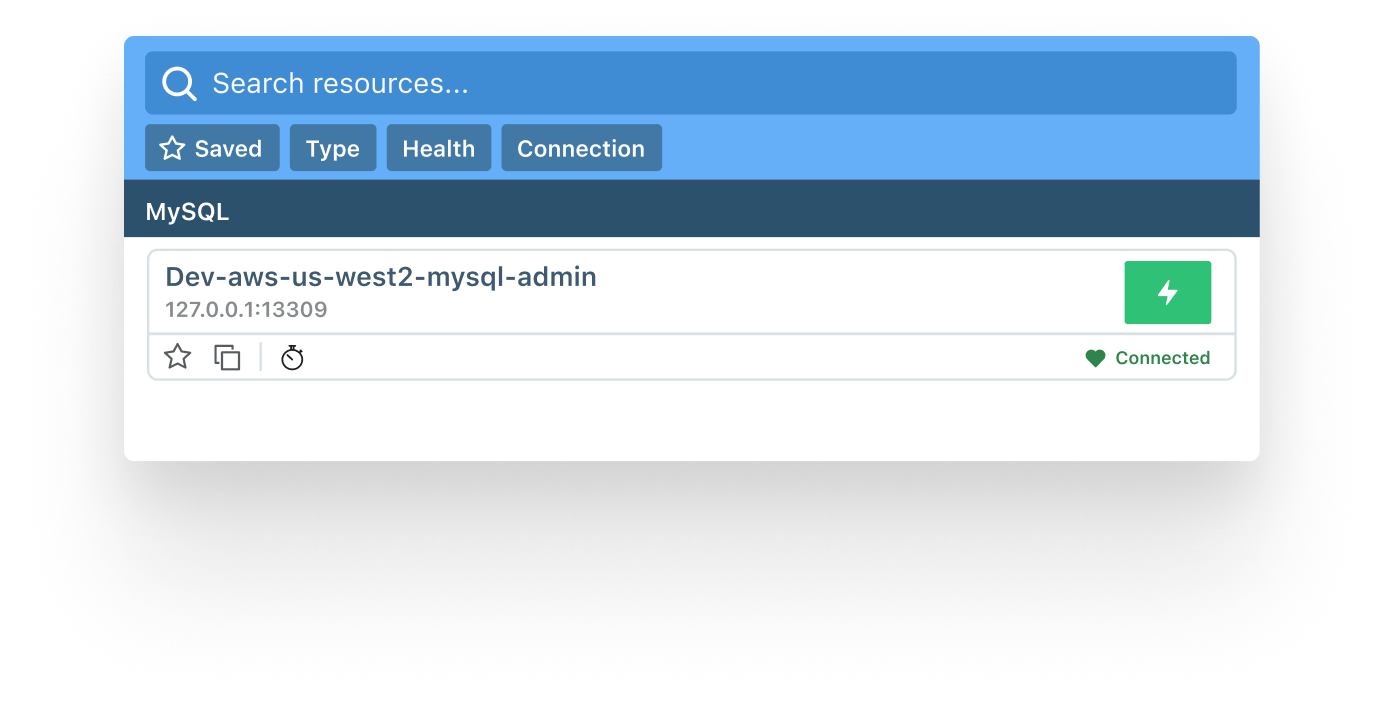







From Legacy Limitations to Strong Security
With Legacy PAM |
With StrongDM Zero Trust PAM |
|
Lack of visibility, control, and audit trail for access events across your full tech stack. |
Full visibility, integrated control, and comprehensive audit trails across everything. |
|
Current PAM solutions have poor user experience leading them to circumvent controls. |
Frustration-free access leads to high adoption rate improving security & productivity. |
|
Cumbersome access policy enforcement and management |
Simple, agile, and contextual access policy management and enforcement, enabling granular control. |
|
No control over what people do with their access |
Precise, dynamic privileged action control for any infrastructure or application. |

A Tailored Solution Just for Your Organization
Your technology stack is unique. Whether your infrastructure spans multiple clouds, utilizes diverse databases, or relies on critical applications, StrongDM seamlessly integrates with technologies you trust.
StrongDM is designed to fit your environment, not the other way around.





Backed by a world-class customer experience
“Security is a necessary part of day-to-day life. In terms of how we go forward, StrongDM will continue to be part of that story. It has all the mechanisms in place for database access control that we require, and I haven’t found a competitor yet that does the same thing.”
Wes Tanner
VP Engineering, ZEFR
“We chose StrongDM because the solution is the one solution to rule them all. You simply integrate all your data sources into StrongDM; you integrate all your servers into StrongDM; you integrate all your Kubernetes clusters into StrongDM. You give your developers one simple tool they need to connect using SSO, and they have access to what they own.”
Jean-Philippe Lachance
Team Lead - R&D Security Defence, Coveo
“Clearcover remains committed to the industry’s best security practices. StrongDM provides us with better insights to bolster our security posture.”
Nicholas Hobart
Senior Engineer, SRE Team, Clearcover
“I would urge all other CISOs to adopt StrongDM as their database proxy platform. It's been amazing for all of our users. When we first got StrongDM, we implemented within, I think a day. And within a week we saw more and more users requesting access to it, once they saw how easy it was to access databases.”
Ali Khan
CISO, Better
“With StrongDM, people don't have to maintain usernames and passwords for databases. With servers, they don't have to have keys. For websites, they don't have to have passwords. And so when you start eliminating the need for passwords and you start looking at things like Zero Trust, I believe that the attack surface is completely reduced.”
David Krutsko
Staff Infrastructure Engineer, StackAdapt



BLOG
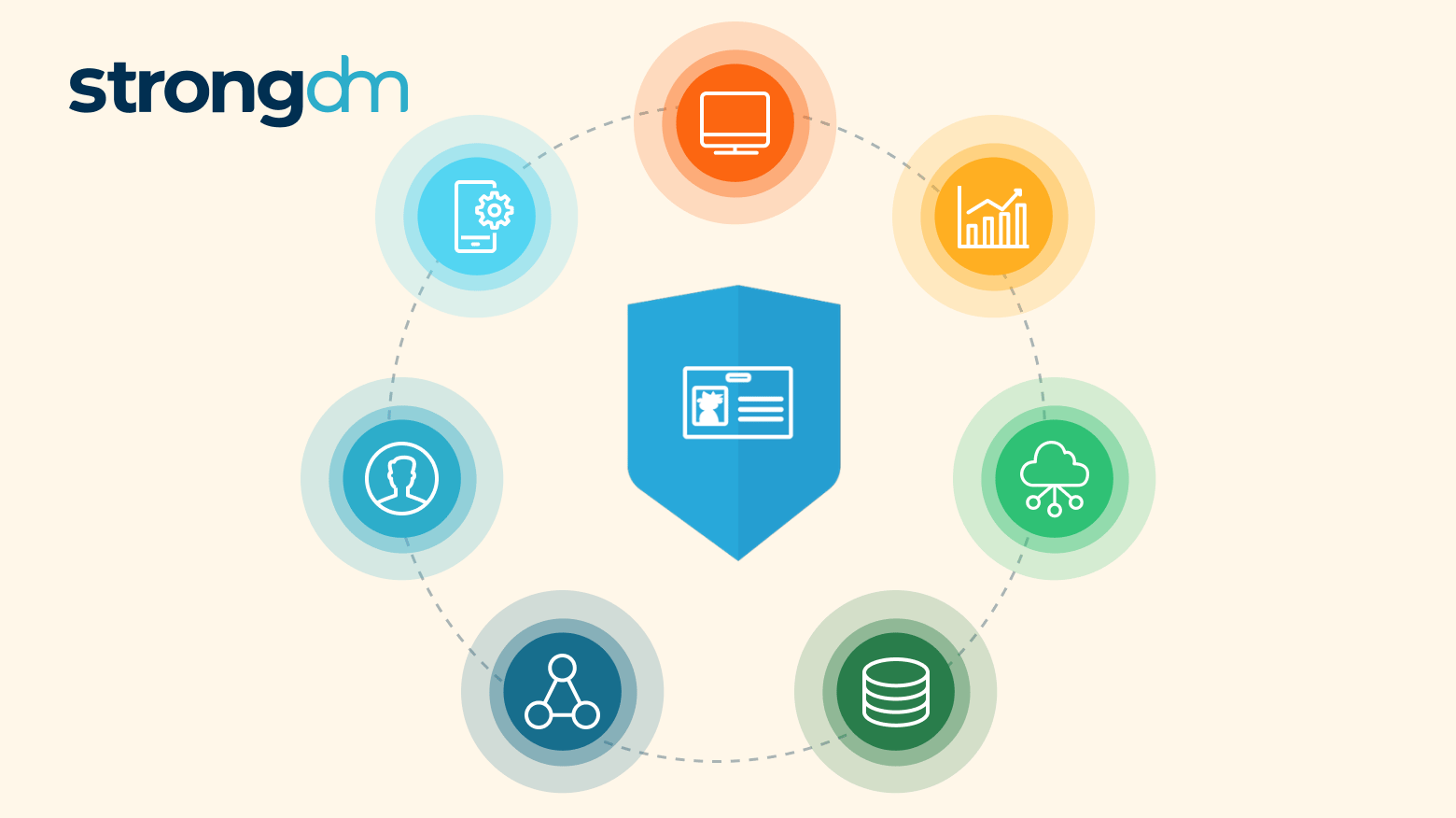
Unlocking Continuous Zero Trust Authorization

Amol Kabe
Chief Product Officer (CPO), StrongDM
Continuous Zero Trust Authorization is the real-time monitoring of access and operations across your infrastructure and the ability to enforce contextual access policies in real-time.

ARTICLE
ISO 27001 Compliance: Complete Guide

Andrew Magnusson
Customer Engineering Expert
ISO/IEC 27001 is the international standard that defines best practices for implementing and managing information security controls within an information management system (ISMS).
Ebook
Innovating PAM: Welcome to the Era of Dynamic Access

Maile McCarthy
Contributing Writer and Illustrator, StrongDM
Secure access shouldn't only be reserved for privileged credentials. Learn why the future of access is dynamic.
Connect your first server or database in 5 minutes. No kidding.
Free for 14 days. No credit card required.


