Leading global brands rely on StrongDM

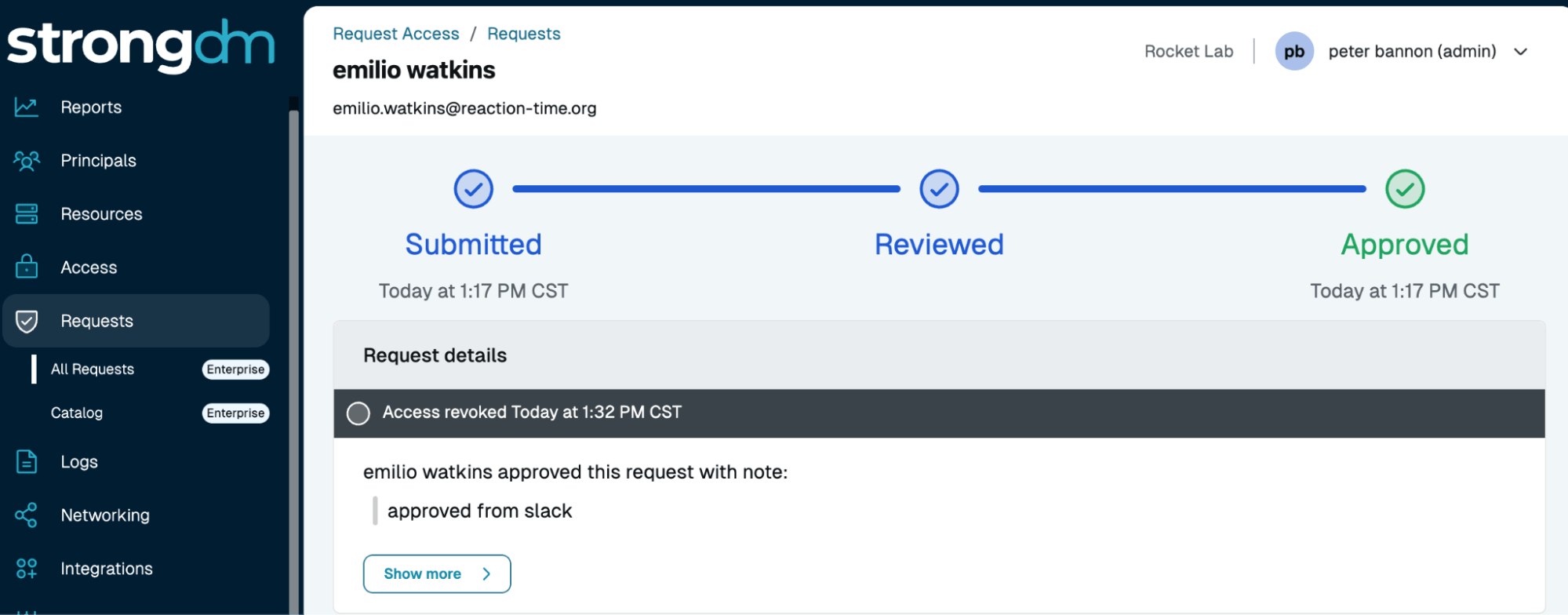
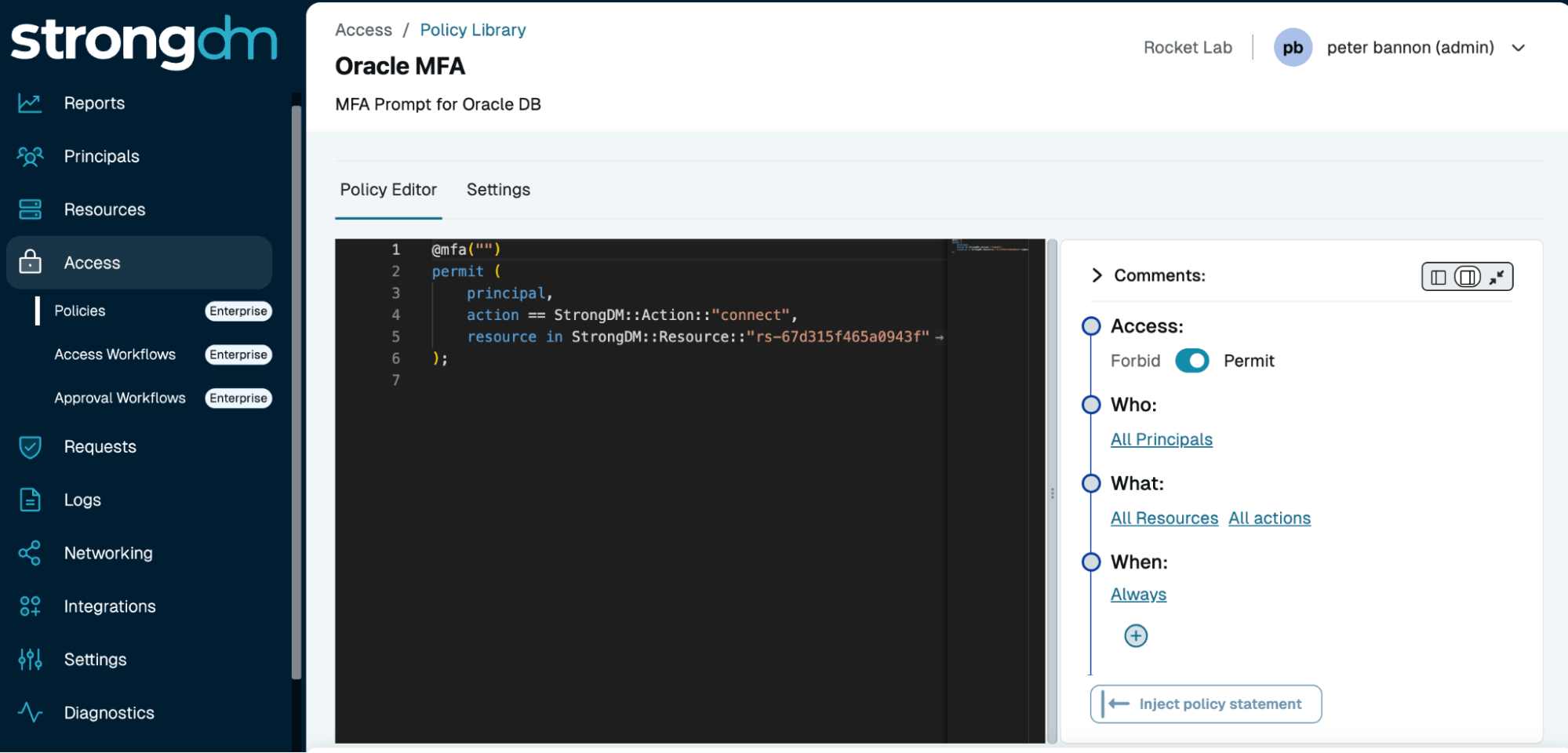
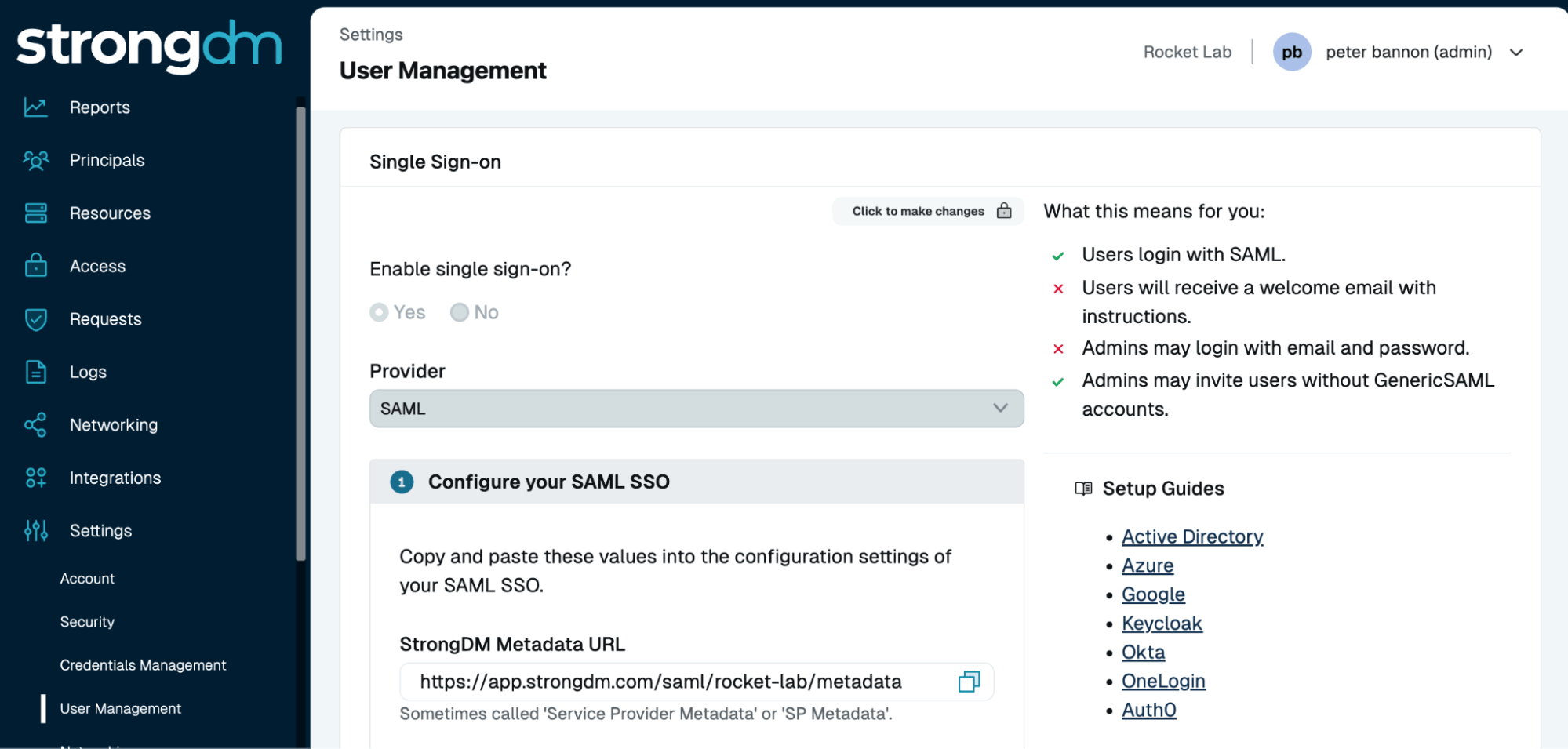
Traditional access management often relies on manual processes, leaving temporary permissions in place longer than needed. This delay results in unnecessary standing access, increasing the risk of misuse or breaches. StrongDM automates Just-In-Time (JIT) access, granting privileges only when needed and revoking them immediately after use.
Faster to gather evidence for audits
Reduction in number of engineers with admin rights
Reduced time to identify and respond to incidents
Shared credentials with credential-less access for your end users



_HighPerformer_Mid-Market_Americas_HighPerformer.png?width=155&height=178&name=IdentityandAccessManagement(IAM)_HighPerformer_Mid-Market_Americas_HighPerformer.png)
_HighPerformer_Americas_HighPerformer.png?width=155&height=178&name=IdentityandAccessManagement(IAM)_HighPerformer_Americas_HighPerformer.png)
_Leader_Leader.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_Leader_Leader.png)
_UsersMostLikelyToRecommend_Small-Business_Nps.png?width=155&height=179&name=PrivilegedAccessManagement(PAM)_UsersMostLikelyToRecommend_Small-Business_Nps.png)
_BestSupport_Small-Business_QualityOfSupport.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_BestSupport_Small-Business_QualityOfSupport.png)
_EasiestToUse_Small-Business_EaseOfUse.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_EasiestToUse_Small-Business_EaseOfUse.png)
_EasiestToDoBusinessWith_Small-Business_EaseOfDoingBusinessWith.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_EasiestToDoBusinessWith_Small-Business_EaseOfDoingBusinessWith.png)
_Leader_Mid-Market_Leader.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_Leader_Mid-Market_Leader.png)
