Welcome to Basecamp!
Identity-Based Access is the first step in the journey toward Zero Trust and Dynamic Access Management. How do you know if you’ve achieved Identity-Based Access?
Access is defined at the user level, and provisioned based on the needs of the individual.
You Are Here
You Need to Be Here
Shifting to a more dynamic access approach means your sensitive resources are better protected at scale.

Resources
If your organization has achieved Level 1, but has not yet implemented a PAM solution, it’s possible to jump directly to Level 3 or 4.
Here's how
Skipping Level 2: It’s possible to avoid a privileged access approach entirely by making the upfront decision that all technical access is potentially privileged.
That means accounting for ALL employees and their access by default. Save time and spare your team from headaches! Skip to Just-in-Time Access!
Download ebook
Privileged Access controls and monitors the activity of only privileged users.
You have implemented Privileged Access Management (PAM) which provides additional security for elevated credentials. It’s a start.
You Are Here
You Need To Be Here
Traditional PAM lacks critical functionalities for the modern environment. Many PAMs do not support all cloud resources, Kubernetes clusters, containers, and even certain databases. PAM's myopic focus on privileged users, and the gaps in the technologies they support, creates unnecessary risk in today’s environment.
JIT Access reduces the risk of unauthorized access by ensuring that users only have access to the resources they need to do their jobs–and for the minimum necessary time.
You Are Here
You Need To Be Here
The ascent from JIT Access to Dynamic Access Management is critical.
Congratulations! You have arrived.
Dynamic Access Management extends secure authentication, authorization, and auditing capabilities to all technical users. DAM provides JIT access to all users who need access to databases, clouds, servers, clusters, and other resources.
Living the DAM Dream
“Security is a necessary part of day-to-day life. In terms of how we go forward, StrongDM will continue to be part of that story. It has all the mechanisms in place for database access control that we require, and I haven’t found a competitor yet that does the same thing.”
“We chose StrongDM because the solution is the one solution to rule them all. You simply integrate all your data sources into StrongDM; you integrate all your servers into StrongDM; you integrate all your Kubernetes clusters into StrongDM. You give your developers one simple tool they need to connect using SSO, and they have access to what they own.”
“Clearcover remains committed to the industry’s best security practices. StrongDM provides us with better insights to bolster our security posture.”
“I would urge all other CISOs to adopt strongDM as their database proxy platform. It's been amazing for all of our users. When we first got strongDM, we implemented within, I think a day. And within a week we saw more and more users requesting access to it, once they saw how easy it was to access databases.”
“With StrongDM, people don't have to maintain usernames and passwords for databases. With servers, they don't have to have keys. For websites, they don't have to have passwords. And so when you start eliminating the need for passwords and you start looking at things like Zero Trust, I believe that the attack surface is completely reduced.”
“With StrongDM, people don't have to maintain usernames and passwords for databases. With servers, they don't have to have keys. For websites, they don't have to have passwords. And so when you start eliminating the need for passwords and you start looking at things like Zero Trust, I believe that the attack surface is completely reduced.”
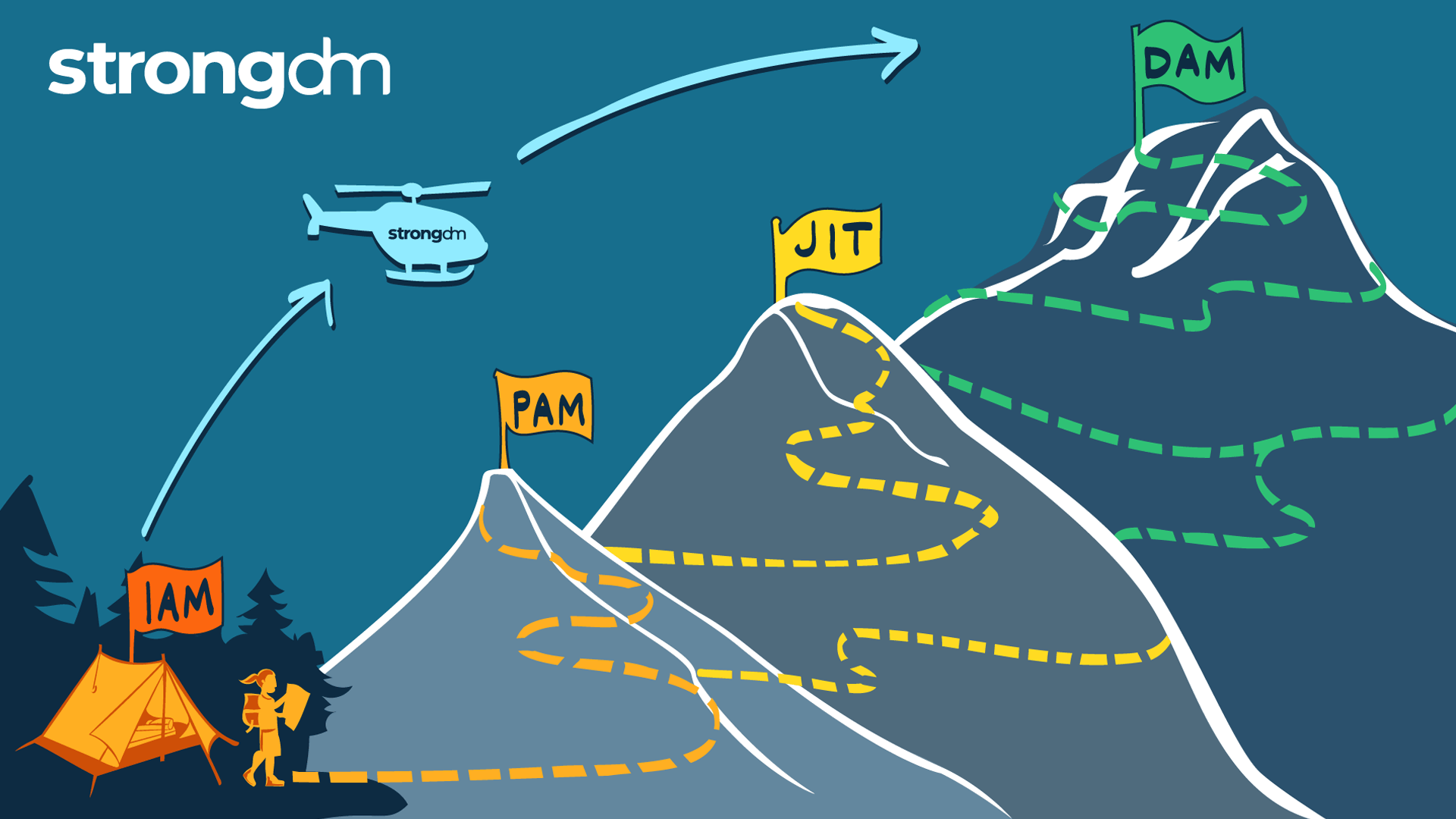

Upgrade Access Control: Journey from Identity-Based to Dynamic Access Management (DAM). Elevate security, efficiency, & compliance. Learn how here.


Learn how StrongDM enables you to extend the protections of PAM to all of your technical users, as well as to the cloud and to technologies that may otherwise not be supported.

So, you’ve decided to conduct an annual access audit. Now comes the obvious question: where do I start? Just like you wouldn’t embark on a mountain clim...