Dynamic Access Management (DAM) is the concept that credentials and access should only exist in the moments they are needed, and that access must be secure and auditable.
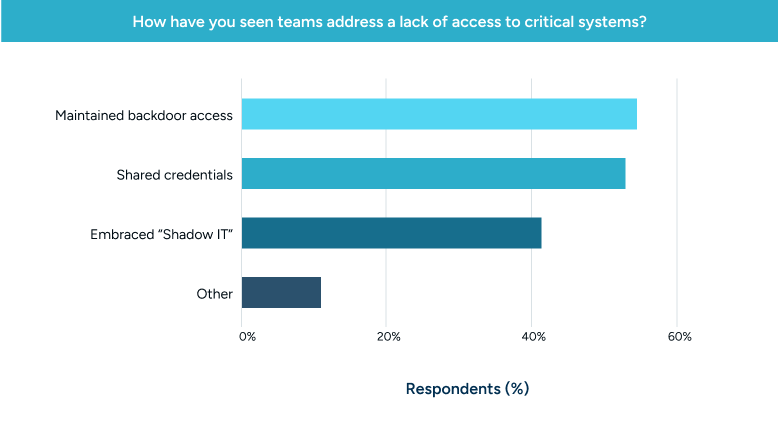
This approach essentially eliminates the risk posed by always-on credentials, including specific attacks like credential stuffing (if no credentials exist, what do you stuff?).
These security outcomes are driven via continuous verification and validation of identity, right-to-access, and observability. Furthermore, once someone is authenticated, the tools and policies of DAM ensure that their authorizations stay up to date in real-time, driving change in behavior or access dynamically.
DAM also provides intelligence around how, why, and when people are using infrastructure and delivers that back to the CISO and technology leaders to map against their business objectives.
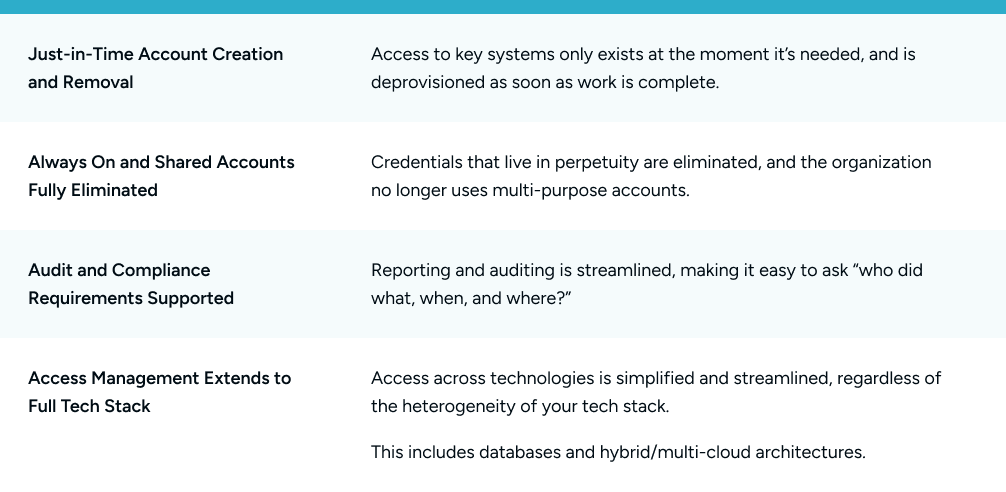
Dynamic access management is characterized by four key attributes:
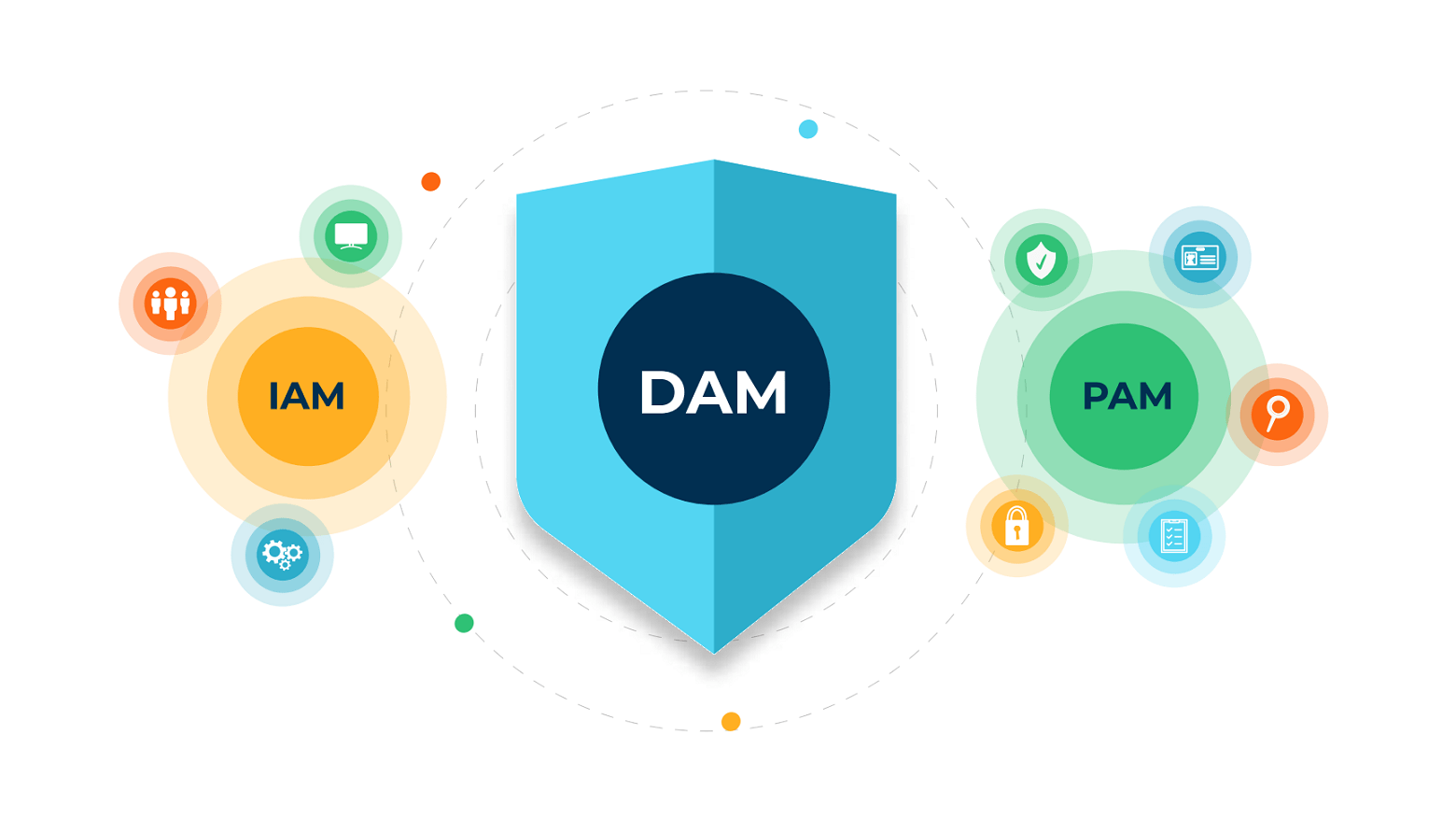
How is DAM different from PAM and IAM?
Privileged Access Management (PAM) is a subset of Identity and Access Management (IAM) that focuses specifically on managing and controlling access to privileged accounts and sensitive systems. PAM solutions include features such as real-time monitoring, session recording, password rotation, and multi-factor authentication to ensure that only authorized users are able to access privileged accounts and that their actions are auditable.
IAM is a broader concept that deals with managing and controlling access to all types of resources, including privileged accounts. While IAM is mainly focused on the user's identity and access to resources, PAM is mainly focused on controlling and monitoring access to privileged accounts, including administrator, root, and service accounts.
Dynamic Access Management (DAM) sits in between IAM and PAM. Where PAM is focused solely on privileged accounts, DAM extends the secure authentication, authorization, and auditing capabilities to all technical users. It also focuses on the overall user experience, making it possible to improve productivity for both users and administrators, even as it reduces the risk of security breaches.
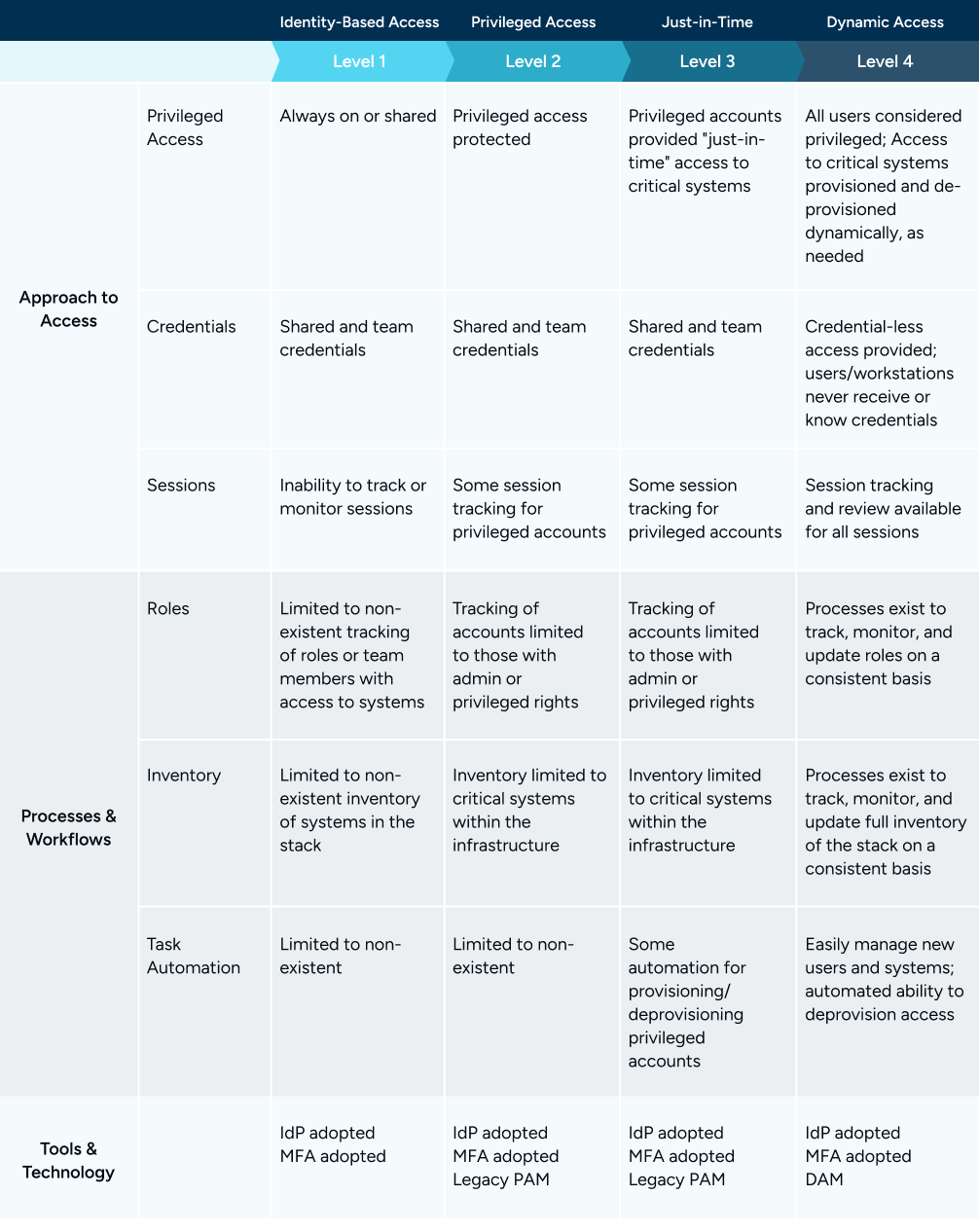
Achieving dynamic access requires a fundamental rethinking of how access to infrastructure should be provisioned and managed. It also represents a modern and sophisticated approach to access management that is agile enough to keep up with your organization. That’s why it’s the highest level possible to attain on the Secure Access Maturity Model.
What is the Secure Access Maturity Model?
The Secure Access Maturity Model helps you identify the strengths and limitations of your current access management practices. The following table will help you understand where your access security protocols are strongest and where they still need to improve.