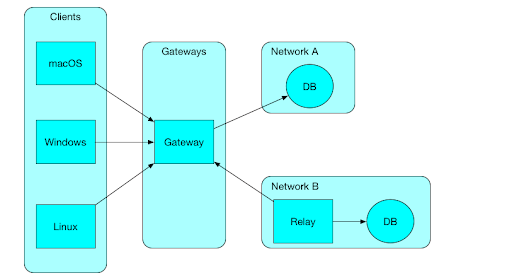
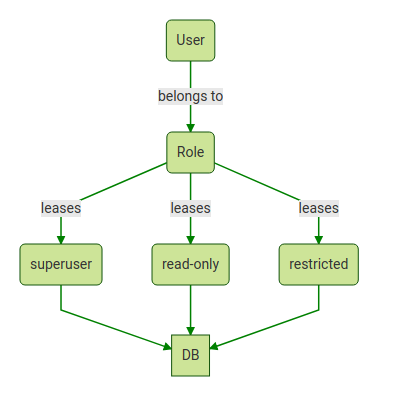
Making the shift to Zero Trust may seem like a lengthy, technically complex process, with risks of service interruption and security gaps along the way. However, significant progress can be made simply by choosing technologies with Zero Trust principles built in, like StrongDM’s Zero Trust Privileged Access Management (PAM) Platform with Continuous Zero Trust Authorization. The following customer stories show exactly how companies dealing with overly complex, inadequately secured access management transitioned smoothly to advanced Zero Trust access control with StrongDM.
Clarity AI Improves Visibility and Eliminates VPN
Clarity AI, a sustainability technology platform leveraging machine learning and big data, delivers environmental and social insights to investors, organizations, and consumers. Clarity AI’s platform analyzes over a million data points weekly from more than 49,000 companies, 220,000 funds, 198 countries, and 188 local governments. Clarity AI maintains offices in North America, Europe, and the Middle East, and a fully remote workforce spread across the globe.
Read the full Clarity AI case study here.
Over-Provisioning Access with VPNs Leads to Security Risk, Poor Visibility
Clarity AI relied on OpenVPN servers in AWS to manage developer access, leading to complexity and limited auditing capabilities. Users had to request temporary credentials via Slack and wait out a slow, manual approval process that burdened administrators. The OpenVPN setup also meant engineers had access to the entire infrastructure, an over-provisioning of access that brought security risks. As for auditing, it was only possible in broad strokes, with admins able to review who connected to the VPN, but not who connected to databases or what commands were issued. This setup was unsustainable and made Clarity AI a prime candidate for Zero Trust.
Clarity AI Secures Access with PoLP and Just-in-Time Access
Clarity AI’s IT and security manager, Luis Cuervo, researched various solutions and ultimately recommended StrongDM. The ease of implementation, flexible pricing structure, and exceptional customer support made StrongDM an easy choice over its Zero Trust competitors. StrongDM's tools and processes felt familiar, engineers didn’t need to overhaul scripts, and end users could access databases using their preferred clients. According to Cuervo, “It was flawless.”
With StrongDM, Clarity AI could eliminate its VPN, the central point of failure, and simplify access management. StrongDM's automated workflows and just-in-time privileged access streamlined the onboarding process and reduced administrative work. The comprehensive audit logs provided unprecedented visibility, allowing Clarity AI to track user activities and ensure compliance with security policies.
Key Benefits of StrongDM for Clarity AI:
- VPN Elimination: By deploying StrongDM, Clarity AI eliminated OpenVPN, reducing security risks and simplifying access management.
- Automated Onboarding and Offboarding: StrongDM's automation capabilities made onboarding and offboarding employees much easier, saving administrators’ time and labor.
- Just-in-Time Privileged Access: StrongDM's Slack integration allowed developers to request privileged access directly within chat, with automated approval processes, reducing delays.
- Detailed Audit Logs: StrongDM's detailed audit logs provide visibility into user activity, allowing Clarity AI to monitor every query and command, supporting compliance and security policy enforcement.
- Principle of Least Privilege (PoLP): StrongDM's dynamic access workflows enabled Clarity AI to implement PoLP, granting access only when needed and minimizing security risks from over-permissioning.
- Progress Toward Zero Trust: With StrongDM, Clarity AI has a powerful tool to pursue a full Zero Trust security model, with the flexibility to adapt as needed. It’s now on its way to achieving ISO 27001 compliance and other security goals.
Beekeeper Eliminates VPN Pain with Zero Trust Security
Beekeeper, a leading platform for connecting frontline teams, helps companies ditch paper and manual processes and improve employee engagement, retention, and performance. With fast growing adoption of its frontline success system, the company faced significant challenges in scaling its access management while maintaining security and efficiency.
Read the full Beekeeper case study here.
Multiple VPNs Lead to Complexity, Security Risks, and Delays
The company relied on numerous VPNs—one for each region in AWS and GCP—creating a complex and cumbersome system. Engineers had to juggle multiple VPNs, leading to slow, frustrating processes. Also, each engineer required credentials to access different endpoints within the network, complicating access management and expanding the attack surface.
Beekeeper's Head of DevOps, Daniel Solsona, knew there had to be a better way. After evaluating several solutions, including Teleport and HashiCorp Boundary, Beekeeper selected StrongDM for its simplicity and technical advantages. StrongDM was easier to deploy and use, with a straightforward architecture compared to the competition. This made it easier for Beekeeper to transition from their existing setup to a Zero Trust model while streamlining their operations.
StrongDM Streamlines, Simplifies Access Management
A key benefit of StrongDM was its ease of use, leading to widespread adoption across Beekeeper's teams. Solsona recalled, "The previous approach was nuts and painful, but [StrongDM] is glorious." StrongDM's user-friendly deployment and seamless integration meant faster employee onboarding and offboarding. The ability to remove a user from the single sign-on (SSO) provider and instantly revoke all access was extremely simple, Solsona said.
"StrongDM was much simpler architecturally than Teleport. With Teleport, you need to run all these different services, and it got to be too much. It was much simpler to run StrongDM compared to Teleport. Hashicorp Boundary was 4-5 years away from what StrongDM is doing now"
- Daniel Solsona, Head of DevOps, Beekeeper
StrongDM's Access Workflows also helped Beekeeper automate workflows and route human approvals for access. With this feature, admins could make universal changes in the infrastructure without provisioning every user manually. It enabled Beekeeper to implement the Principle of Least Privilege (PoLP), granting specific people access only when needed and with appropriate controls. By reducing end-user credentials and adopting a just-in-time access approach, Beekeeper took significant steps toward achieving Zero Trust.
Key Benefits of StrongDM for Beekeeper:
- Elimination of Multiple VPNs: StrongDM enabled Beekeeper to eliminate the need for separate VPNs for each region in AWS and GCP, simplifying access management.
- Simplified Onboarding and Offboarding: StrongDM made it easy to add or remove users from the system, ensuring a smooth, secure transition when employees join or leave the company.
- Automated Access Workflows: StrongDM's Access Workflows feature automated the process of granting access, reducing manual interventions and streamlining operations.
- Principle of Least Privilege (PoLP): With StrongDM, Beekeeper could implement PoLP, granting access only when necessary and reducing the risk of over-permissioning.
- Comprehensive Audit Logs: StrongDM's detailed audit logs allowed Beekeeper to track user activities and ensure compliance with security policies.
- Zero Trust Implementation: StrongDM provided the flexibility and simplicity needed for Beekeeper to pursue its Zero Trust initiatives, offering a clear path to achieving this security model.
Better.com Adopts Zero Trust Access
Better.com is an online lender that provides a 100 percent digital home buying process that is faster, easier, and more transparent. As a financial tech company handling sensitive customer data, Better.com needs a robust network security approach. But prior to strongDM, they didn’t have an efficient management system for database access.
Read the full Better.com case study here.
Weeklong Waits for Access Lead to Productivity Losses
Despite their highly digitized public-facing services, their backend management processes and governance operations were highly manual—creating burdensome overhead costs and increased risk of error. As a result, it often took up to a week to get access provisioned. This not only took team members away from higher priority activities but also had a downstream impact on productivity in favor of security. And with 41 databases and five database management systems, this approach was unsustainable—they needed a solution that could help them implement Zero Trust across their systems while scaling and strengthening their data security posture.
StrongDM Makes Access Control Easy, Boosting Productivity
That’s where strongDM came in. StrongDM makes it easy to grant access and audit access control. Better.com was able to implement strongDM within a day and started seeing results immediately. In fact, within a week, Better.com saw an increase in user requests once users saw how easy it was to access databases.
And users can access the database from anywhere. “For Zero Trust, StrongDM is an amazing tool—BYOD, within the company, outside [the company], wherever you need to go, you can access the data in a secure way,” says Ali Khan, CISO at Better.com.
Key Benefits of StrongDM for Beekeeper:
- Proactive data loss prevention: With StrongDM, Better shifted from a reactive security posture to a proactive approach to data loss prevention. By monitoring and detecting suspicious activity in real time, Better.com was able to suspend users before they could cause damage.
- Faster incident response: StrongDM’s audit capabilities ensure all activities are logged and tracked, from permission changes to employee queries. This provides peace of mind while ensuring compliance and the ability to respond quickly to potential incidents.
- Reduced overhead costs: StrongDM relieves the burden on security teams to monitor and manage database connections so they can focus on other priorities. Before strongDM, it took Better.com’s team a week to get someone provisioned. Now it takes just minutes.
- Improved compliance and regulatory adherence: StrongDM enables stronger and simpler compliance without unnecessarily locking down data and preventing business users from accessing the information they need to do their jobs.