
Your security stack shouldn't dictate your infrastructure choices. Move faster across AWS, Azure, GCP, and on-prem with unified security that deploys in minutes and scales automatically—enabling innovation, not blocking it.
Your competitors move fast. StrongDM makes it so you don’t have to choose between security and productivity, accelerating release cycles while strengthening security posture. Turn compliance into a competitive advantage, not a constraint.
Before StrongDM
After StrongDM
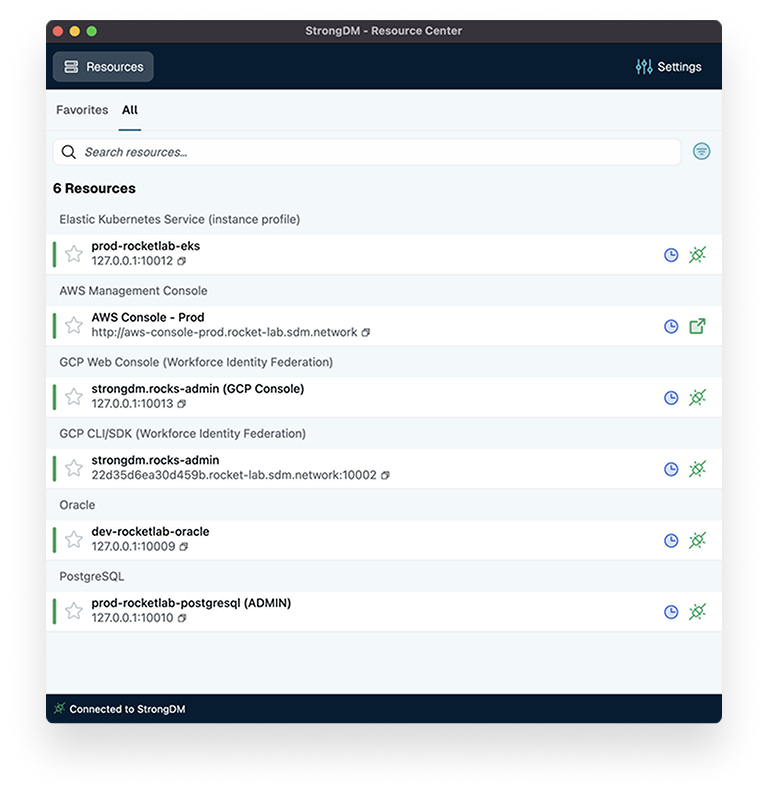
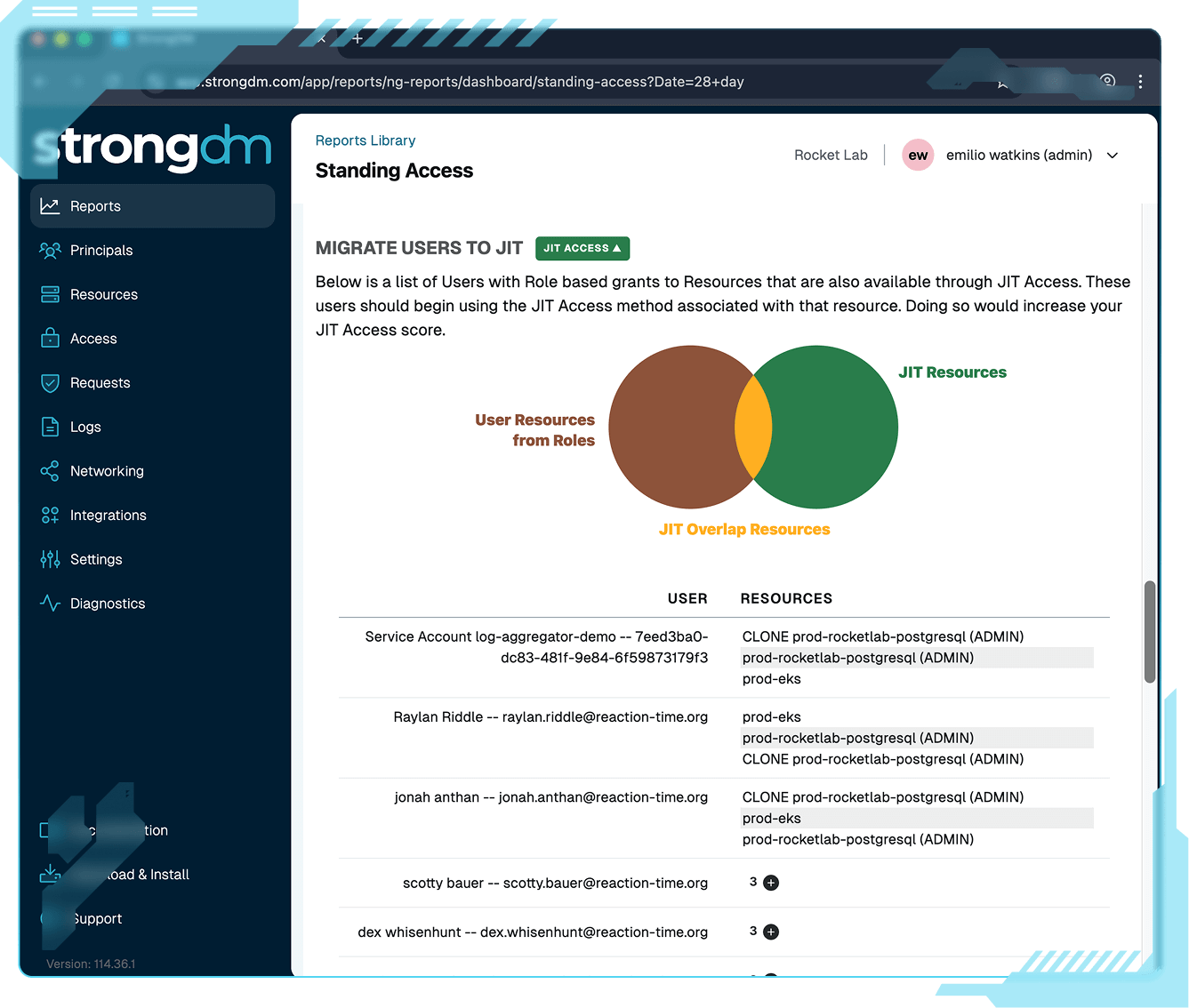
StrongDM’s Cedar-based Policy Engine continuously evaluates user, device, resource, and risk context to authorize access at runtime. Define once, enforce everywhere, and adapt instantly as conditions change across your cloud, hybrid, and on-prem environments.
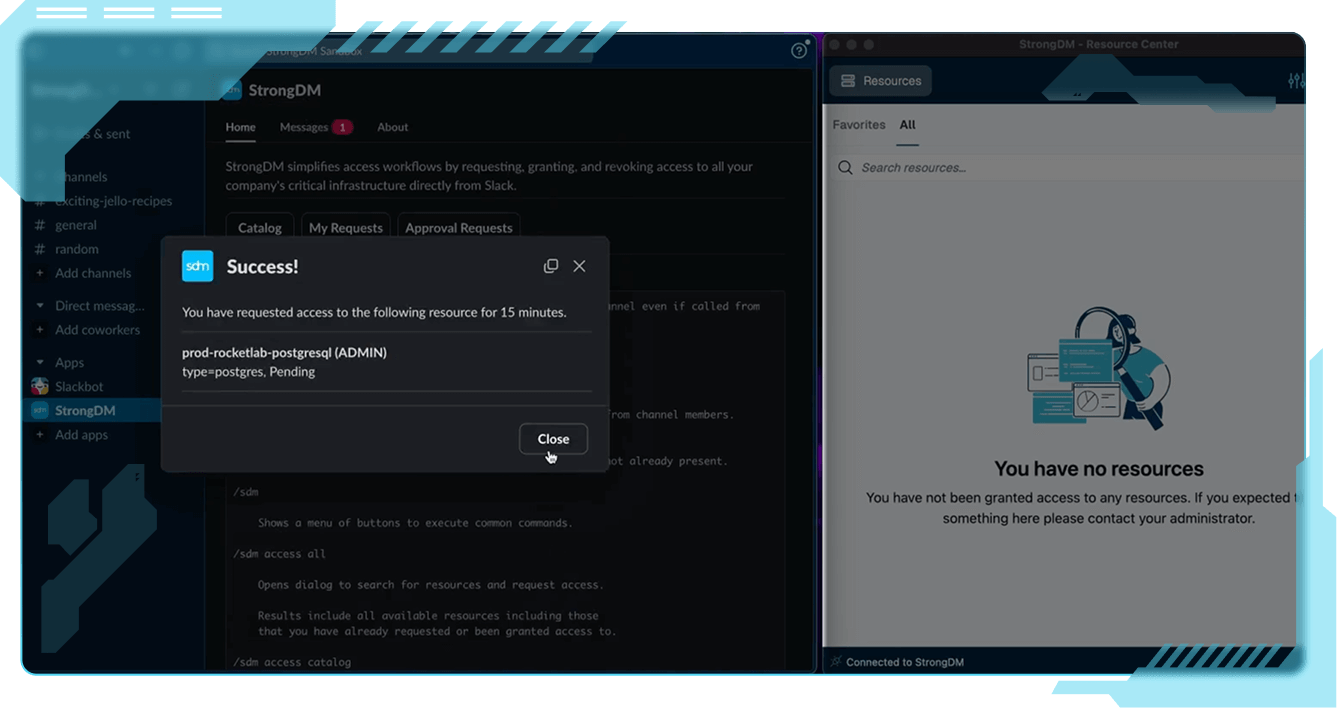
StrongDM enforces policy and access continuously, not just at login, to adapt in real time as conditions change. Every action, session, and identity is authorized at runtime for uncompromising control.
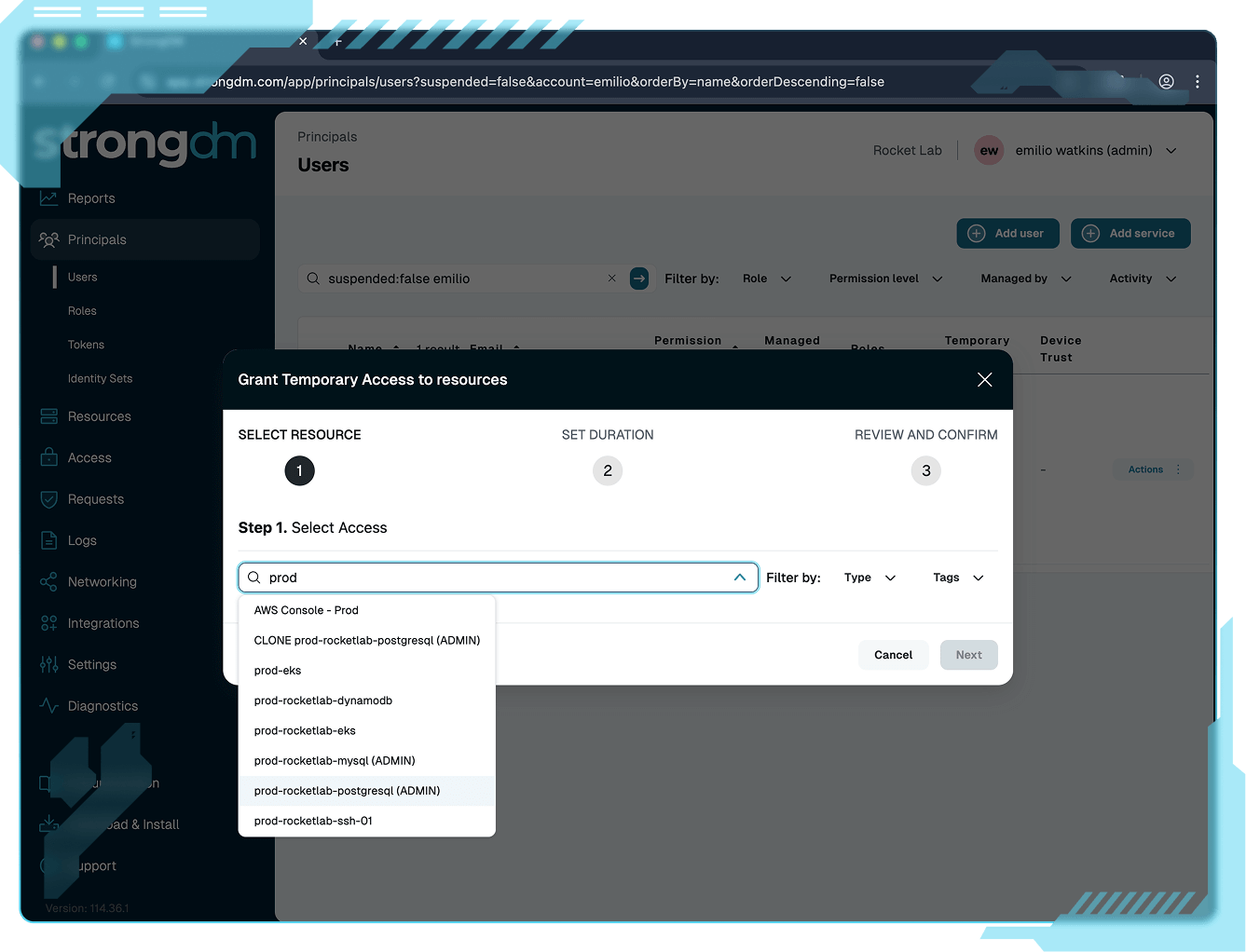
Built for developers, operators, and security teams alike, StrongDM delivers Zero Trust control that integrates cleanly into existing workflows. No context switching, no waiting, no frustration.
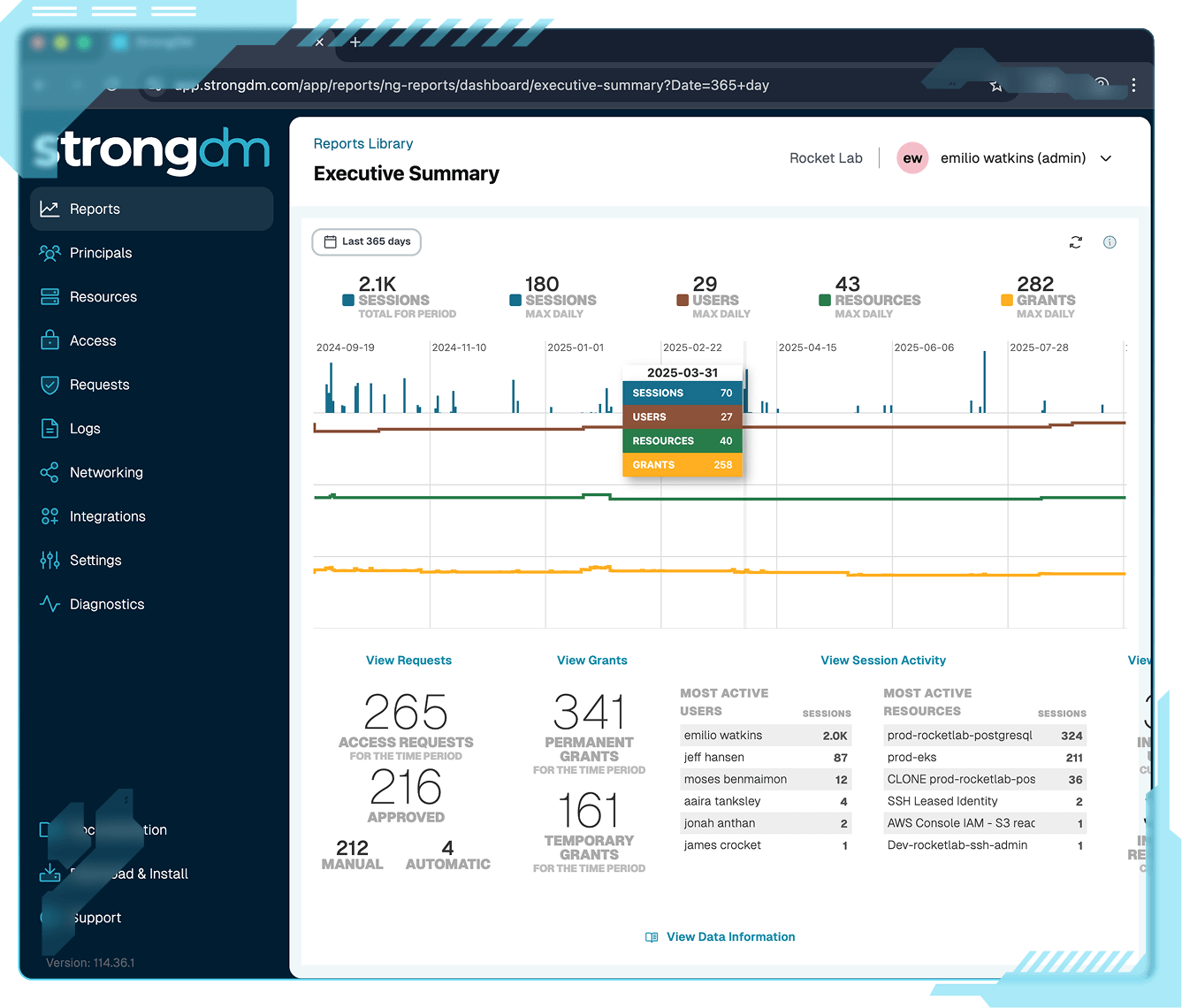
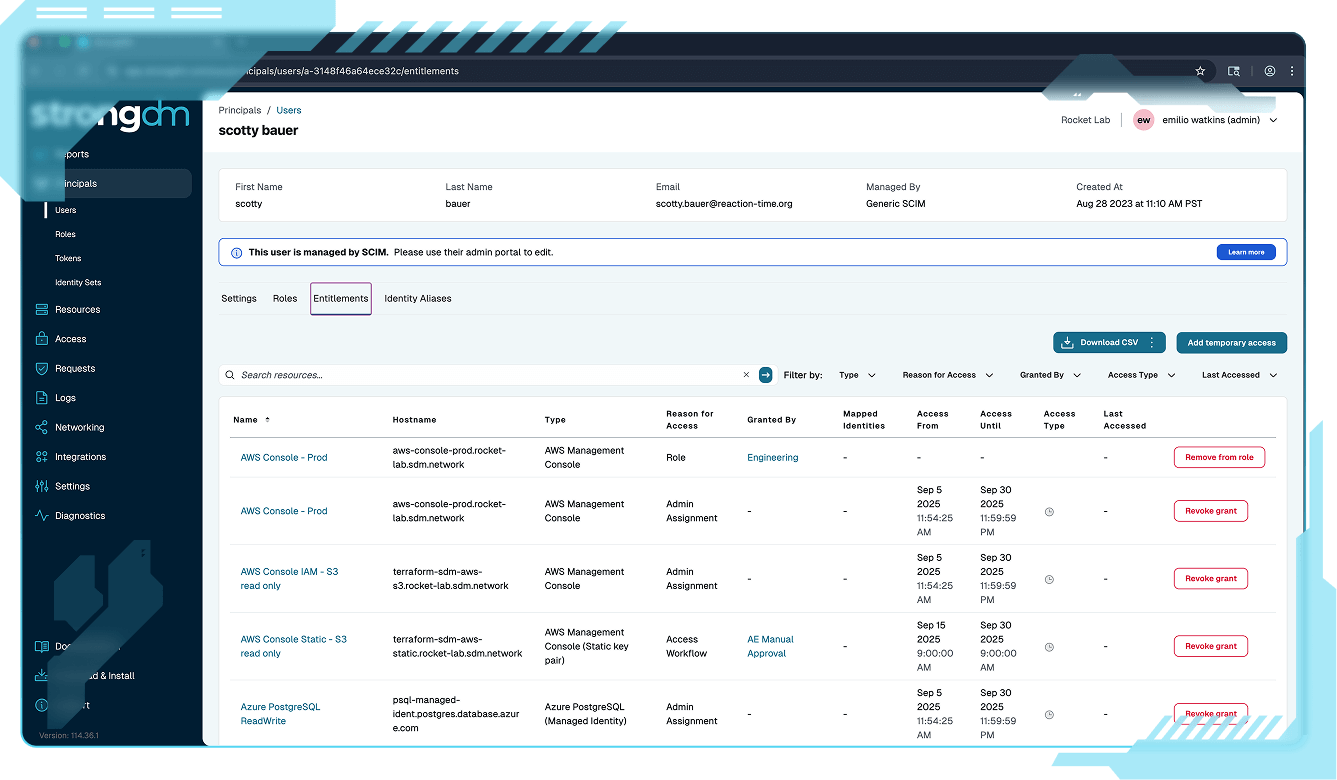
Capture and monitor every session across users, machines, and agents in one unified view. StrongDM eliminates blind spots and provides the audit-ready visibility legacy PAM can’t.
StrongDM layers on top of your existing stack with no migration or code changes. Deploy in hours, not months, and modernize your access model without breaking what works.
“Security is a necessary part of day-to-day life. In terms of how we go forward, StrongDM will continue to be part of that story. It has all the mechanisms in place for database access control that we require, and I haven’t found a competitor yet that does the same thing.”
“We chose StrongDM because the solution is the one solution to rule them all. You simply integrate all your data sources into StrongDM; you integrate all your servers into StrongDM; you integrate all your Kubernetes clusters into StrongDM. You give your developers one simple tool they need to connect using SSO, and they have access to what they own.”
“Clearcover remains committed to the industry’s best security practices. StrongDM provides us with better insights to bolster our security posture.”
“I would urge all other CISOs to adopt strongDM as their database proxy platform. It's been amazing for all of our users. When we first got strongDM, we implemented within, I think a day. And within a week we saw more and more users requesting access to it, once they saw how easy it was to access databases.”
“With StrongDM, people don't have to maintain usernames and passwords for databases. With servers, they don't have to have keys. For websites, they don't have to have passwords. And so when you start eliminating the need for passwords and you start looking at things like Zero Trust, I believe that the attack surface is completely reduced.”