Augmenting Legacy PAM with StrongDM: Getting to Dynamic Access


Written by
Dominic GarciaLast updated on:
September 15, 2023Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Privileged access management (PAM) tools have become ubiquitous across organizations. The ability to add additional security measures for credentials and accounts with escalated permissions has become a requirement for security teams and for cybersecurity insurance.
However, as enterprises continue to evolve and embrace the cloud and modern tools like Kubernetes and containers, it’s become increasingly difficult to manage credentials across disparate tools and environments easily. There are a few reasons for this.
The Cloud Simplifies Infrastructure, Complicates Access
Embracing the cloud immediately complicates security and how you manage access. Where you may have had a discrete set of credentials you need to protect, you now have an entirely new environment–or in the case of multi-cloud, multiple new environments. And if you’re an organization that will continue to maintain on-premises technologies, suddenly, you have to figure out a hybrid approach to access management because most legacy PAMs don’t support the cloud.
Further complicating matters, PAM tools like BeyondTrust, CyberArk, Delinea, OktaASA and Teleport force you to use their specific vaults. So, your DevOps teams who did the responsible thing by utilizing HashiVault and AWS Keystore are put into a tough spot – either continue to operate outside of the PAM or migrate to another vault. This brings us to the challenge of vault vendor lock-in.
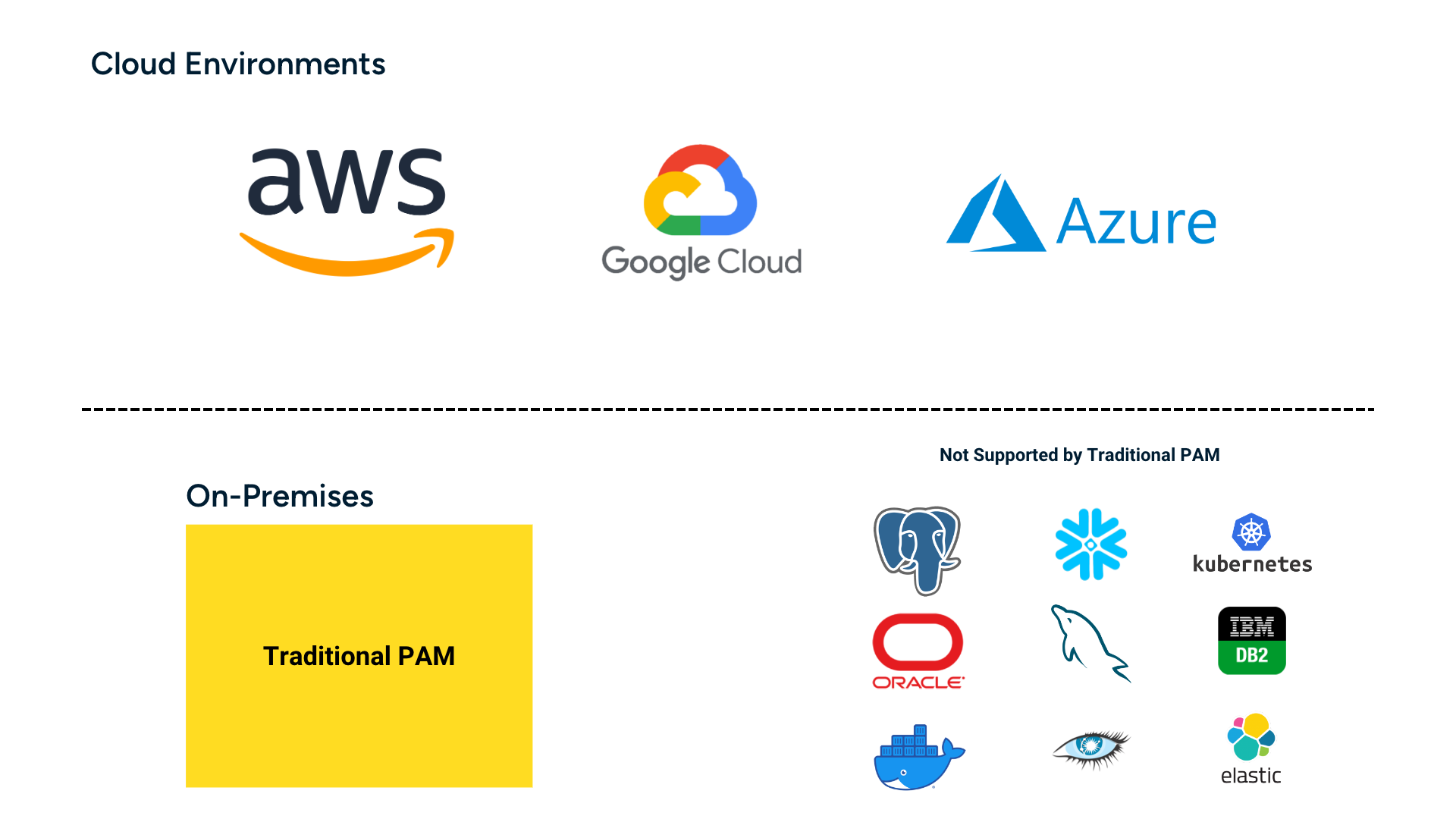
Vault Vendor Lock-In
PAM tools have an underlying vault to manage and protect credentials and secrets. If you’re using the cloud, each cloud vendor has their own vault as well.
The bad news? Vaults are specific to each tool, and they don’t integrate. Once you’ve chosen to use a specific PAM tool, it can become prohibitively complex and expensive to change or update tools. That means most organizations use their traditional PAM tool for on-premises access and each cloud provider’s tool for that specific cloud environment.
Gaps in Coverage: Limited Native Integrations
PAM tools also tend to have a limited number of protocols they support. That creates gaps in your IAM strategy, leaving access to sensitive and critical tools like databases, Kubernetes, and containers unprotected. As organizations continue to embrace new tools, it is imperative that their approach to access management is dynamic and flexible enough to support any tool–existing or new–in their stack.
Augmenting PAM: Getting to Dynamic Access
Extending secure access beyond your PAM tool doesn’t have to be prohibitively expensive or require a rip and replacement of the PAM investments you’ve already made. It simply requires technology and processes that complement your existing PAM strategy and deployments.
That’s where StrongDM comes in.
StrongDM is a platform that provides comprehensive access controls and auditing capabilities for managing privileged access across modern IT environments. StrongDM enables you to extend the protections of PAM to all of your technical users, as well as to the cloud and to technologies that may otherwise not be supported. The goal is to get to dynamic access–an access model that can support changes in your organization’s teams and tech stack dynamically.
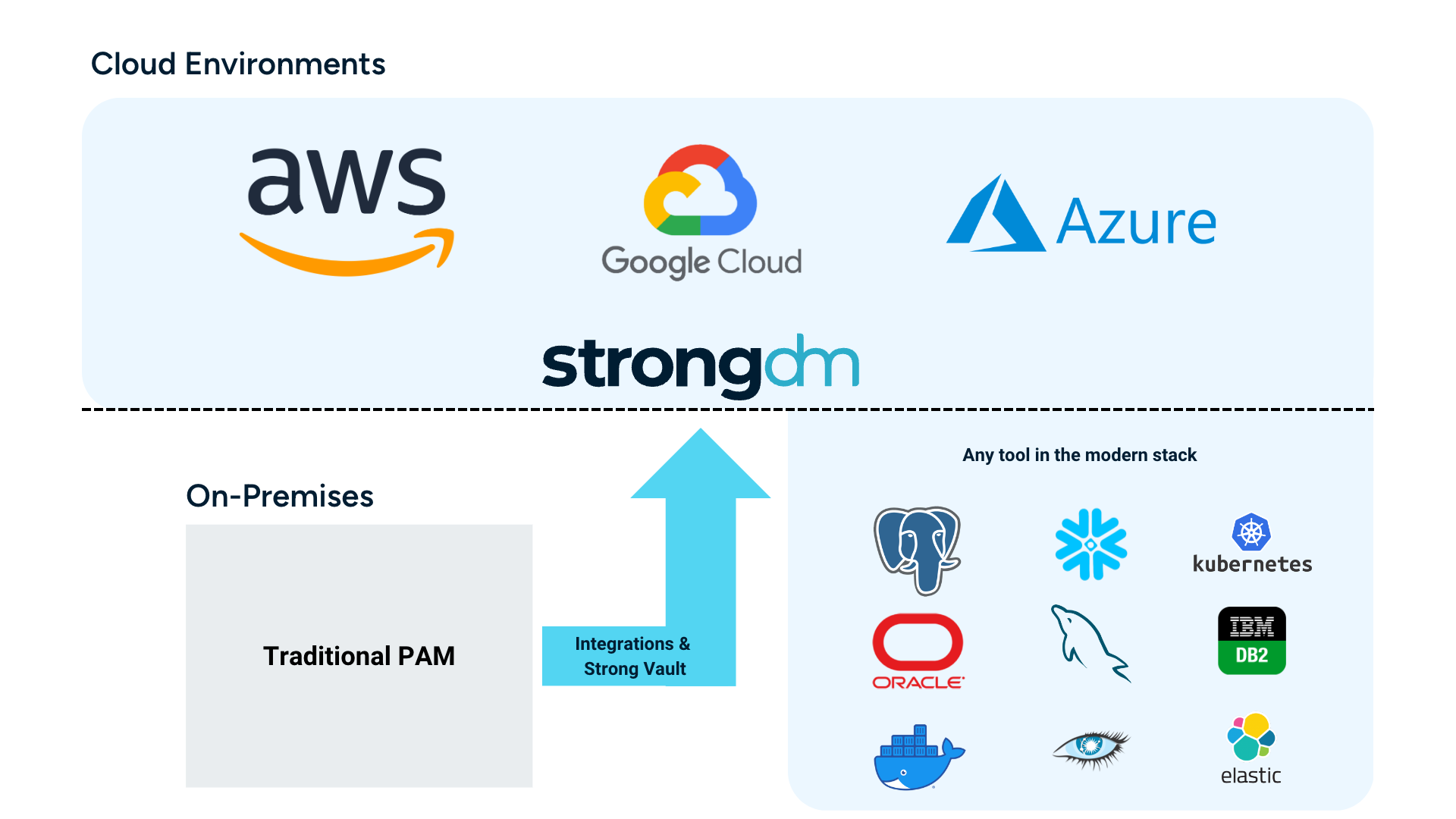
Consolidating Cloud Access Management
StrongDM can help to consolidate how you manage access in the cloud, including for multi- and hybrid-cloud deployments. Because StrongDM is vendor agnostic, it integrates across all three major cloud providers to provide a central location to manage access across cloud environments. This gives your team full visibility into who is doing what, where, and when; while also making that access auditable for compliance.
Getting Beyond Vault Lock-in
StrongDM can augment traditional PAM tools like CyberArk, BeyondTrust, Delinea or others in several ways, including supporting multiple concurrent vaults and providing support for a wide range of infrastructure and native integrations, including cloud environments.
This is particularly useful in large organizations where different teams may use different PAM tools or vaults. Rather than requiring each team to manage its separate vault or move everything out of an existing vault, StrongDM provides a unified platform to manage access across multiple vaults and PAM tools, allowing for consistent policies and streamlined management.
Covering the Gaps: 100+ Native Integrations
In addition to supporting multiple concurrent vaults, StrongDM also supports a wide range of infrastructure and native integrations that traditional PAM tools may not. This includes support for cloud environments like AWS, Google Cloud, and Microsoft Azure; common protocols like SSH and RDP; and newer tools like cloud-native data stores, Kubernetes, and containers. This means that organizations can use StrongDM to manage privileged access across all of their IT infrastructure, regardless of where it is located or how it is accessed.
Auditing Access Across Your Stack
One of the key advantages of using StrongDM to augment your existing PAM deployment is the ability to log all access and activity across all infrastructure and protocols, providing a detailed audit trail that can be used for compliance, incident response, and forensic analysis. This level of visibility and control is critical in large organizations where the risk of insider threats and data breaches is high.
Getting to Dynamic Access
Dynamic access is all about providing secure access for your technical staff, regardless of the tools or environments they’re working with. Two pieces of this methodology that cannot be overlooked are just-in-time access and zero standing privileges.
For access to be truly dynamic, it must also be ephemeral. It’s access that is provisioned and exists while it’s needed (just-in-time), and no longer exists when it’s not (zero standing privileges). This is the only way to achieve least privilege and ensure that every possible approach to reducing credential-related risk has been taken.
StrongDM can be a powerful complement to traditional PAM tools like CyberArk in large organizations. It can enable you to enhance your security posture, improve your compliance posture, and reduce the risk–all in a way that supports your existing cloud and IAM strategies.
Interested in learning more about how StrongDM can augment your PAM deployment? Sign up for a demo today.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Dominic Garcia, Technical Marketing Expert, has held marketing leadership roles for Silicon Valley technology companies specializing in database, data management, and data analytics solutions. As head of content marketing at Splunk, Dominic contributed to boosting the company’s market visibility and its growth from a $100M to a $1.3B company. He brings relentless creativity to the task of connecting people with technical products to improve their lives. Dominic holds a B.S. degree in Public Relations from the University of Texas at Austin. To contact Dominic, visit him on LinkedIn.
You May Also Like




