What Is Cloud PAM? Migration, Challenges & More

Written by
John MartinezLast updated on:
June 26, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Cloud migration is inevitable. And while moving data, virtual machines, and microservices to a cloud environment might seem relatively straightforward, the same cannot be said for migrating Privileged Access Management (PAM).
A PAM cloud migration poses a number of challenges, including reconciling legacy and cloud-based access control frameworks and configuring access control among a range of disparate services. At the same time, since few migrate completely to the cloud, organizations must manage access for legacy resources not running in the cloud.
The key to successfully migrating PAM from an on-prem environment to the cloud is a provisioning strategy that incorporates both access and visibility. Below, we’ll dig into what exactly that looks like.
What Is Cloud Privileged Access Management (PAM)?
Cloud Privileged Access Management (PAM) is a security framework designed for safeguarding critical data in cloud environments. It focuses on controlling and monitoring access to privileged accounts, ensuring that only authorized individuals have entry. This helps mitigate the risk of unauthorized actions and enhances overall cloud security.
Why Migrate PAM to the Cloud?
In both on-prem and cloud environments, privileged access management lets you assign defined access to critical resources based on the “privileges” associated with particular users or groups. Properly configured and managed, PAM keeps sensitive assets secure, by only allowing users to access the systems and data that they need.
⚠️ Traditional PAM deployments have gaps. Learn how to protect your databases, the cloud, Kubernetes, and more with our legacy PAM augmentation guide.
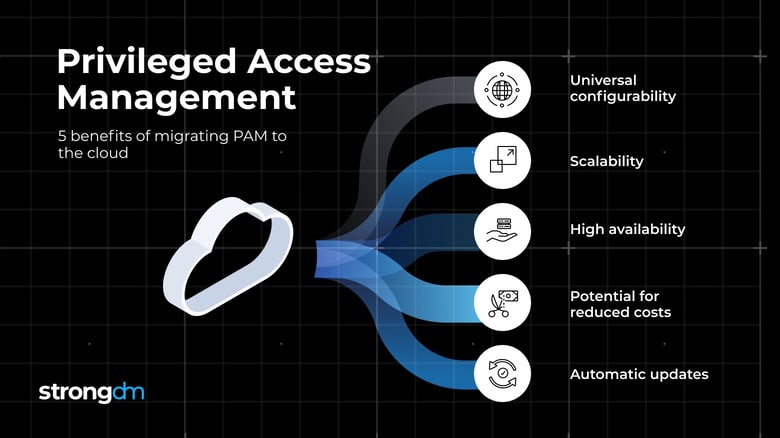
While most companies migrate PAM as part of broader infrastructure modernization strategies, migration can free up infrastructure resources devoted to the hosting and ongoing maintenance of a legacy solution. When moved to the cloud, PAM becomes more flexible, offering benefits, including:
- Universal configurability: Cloud-based PAM solutions can be managed from any location with an Internet connection.
- Scalability: A PAM solution hosted in the cloud can scale to fit environments of any size. Whether you have ten users to manage or ten thousand, the same solution should work.
- High availability: Because cloud-based infrastructure offers minimum service disruptions, PAM solutions that run in the cloud offer more uptime and, therefore, higher availability.
- Potential for reduced costs: Most cloud PAM vendors provide pricing models that allow you to pay based on the services you need. This can lead to reduced costs depending on the vendor and specifications, it can also as your stack grows and you require different pricing tiers.
- Automatic updates: Cloud PAM vendors handle updates, patches, upgrades, reducing the effort required by the organization to maintain hardware and software.
These benefits help to explain why, as of 2018, 50 percent of organizations in the United States had deployed PAM solutions in cloud environments.
Challenges to PAM Cloud Migration
The lift-and-shift strategy so common to data migration isn’t necessarily the best fit for moving PAM from an on-prem to a cloud environment. In fact, PAM migration to the cloud presents some unique challenges that require a more sophisticated strategy.
Here’s why:
- Different security models: Legacy PAM solutions that were designed first and foremost for on-premises environments handle security in a fundamentally different way from cloud-based, SaaS alternatives. The former lack continuous monitoring, for example, and the ability to trace interactions between different types of cloud services (such as virtual machines and serverless functions). Companies that adopt a lift-and-shift approach must therefore find ways to make their on-premises PAM solution cloud-aware, which will be difficult and (in all likelihood) expensive.
- Shared cloud accounts: In public cloud environments, a single cloud account is often shared by multiple employees within an organization. This makes access requests and activity more difficult to track on a per-user basis. It also complicates efforts to translate on-premises access control policies into cloud environments, and to assign access privileges on a granular basis. At the same time, because cloud-based resources are typically shared by large groups, it entails a steep increase in the volume of users to manage.
- Risk of standing privileges: Admins It can be difficult in the cloud to avoid the temptation of configuring “standing privileges,” or assigning access privileges on an ongoing basis. Standing privileges are easier to manage because admins have to configure them only one time. They are also easier to reproduce because the same configurations can be copied from one environment to another. Nonetheless, standing privileges pose a risk because they give users unlimited access, even in cases when they need access only to certain types.
- Configuring multiple cloud services: Cloud environments are typically composed of multiple types of cloud services, such as virtual machines, storage and containers. PAM needs to be configured independently for each type of service. This configuration burden means that it may take months to set up PAM when migrating to the cloud, especially when relying on legacy PAM solutions that can’t be configured natively for cloud environments.
- Administrative strain. From manually setting up new users to rotating credentials when new users are offboarded, PAM solutions can create a mass of administrative tasks for sysadmins and database admins. Manual management can result in inefficiencies, including account credentials stored in spreadsheets, idle provisioned accounts, and a multi-step onboarding process.
Provisioning Access With a Single Control Plane
Because of the challenges discussed above, PAM is not well-suited to the needs of organizations that have migrated to the cloud. A better strategy is to choose an access control solution that offers an alternative to PAM by provisioning access for all users, not just privileged accounts, through a single control plane. A control plane is a SaaS solution that centralizes access granting and auditing for any on-premises or cloud-based firewalled resource. Retaining benefits such as access from anywhere, high availability, and scalability, a control plane helps you move beyond privileged access to access for everyone:
- Manage access for all users. PAM provides access only to privileged users, such as those who serve as admins. A control plane, in contrast, can manage access for all users. This approach is preferable in cloud environments where normal users require controlled access to resources.
- Provision access in fewer steps. With cloud PAM, you’ll need to set up your solution within each individual server and database, and then, for each new hire, provision database credentials, ssh keys, and VPN passwords. A control plane eliminates this entirely. By integrating with any identity provider, it collapses all access for SSH, RDP, etc. into a single centralized point. With permissions databases and servers and applications centralized, onboarding and offboarding can be done from one interface.
- Enable role-based access. No one needs constant, unfettered access. The built-in user and role management within the StrongDM admin allows you to give each user the correct level of access for the correct amount of time. In this way, you can configure access with as much granularity as you need, while avoiding standing privileges that can lead to loss of system integrity.
- Audit logs and auditing strategy. Automated audit trails cover your entire infrastructure, giving you the ability to log every permission change, database query, SSH and kubectl command. With StrongDM you can standardize logs across any database type, Linux or Windows server, and Kubernetes.
- Offboarding. With StrongDM, there’s no need to rotate credentials and update passwords when a user is offboarded. From the control plane, you can suspend SSO access once to revoke all database and server access.
- Remote work access and contractor access. Most companies have a large roster of vendors and contractors who need varying levels of access to complete tasks. From a control plane, you can see exactly what they have access to, offboard them when their work is complete, and ensure you are in accordance with compliance requirements.
The value of a single control plane is even greater if you’re among the 58 percent of companies with a hybrid cloud model, which entails using on-premises infrastructure and the cloud at the same time. With a single control plane, you can manage privileged access for all parts of your infrastructure -- and on any type of operating system or directory service -- without having to juggle multiple PAM solutions, spend months setting up your configurations, or struggling to shoehorn legacy PAM tools to fit a cloud architecture.
Simplifying Your Cloud PAM Migration with StrongDM
Virtually every organization today is using the cloud in one way or another. Traditional PAM solutions are ill-equipped to address the access-management needs of cloud environments, which require role-based access management for all users, not just those with privileged roles. StrongDM’s control plane provides flexible, centralized and easily auditable access management for the cloud.
See for yourself with a free, 14-day StrongDM trial.
Learn more about how StrongDM helps organizations with an enterprise-ready Cloud PAM solution.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like





