

Written by
Fazila MalikLast updated on:
May 3, 2023Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Have you ever found yourself holding onto things that no longer serve you? While change isn’t easy, sometimes it's important to recognize when it's time to let go and move forward.
It’s time to let go of legacy privileged access and adopt a Dynamic Access Management (DAM) platform that operates with today's infrastructure. In today’s world, security must extend to all of your technical users—including developers, security analysts, data scientists, and marketing analysts. The same old Privileged Access Management (PAM) simply isn’t enough anymore.
At StrongDM we manage and measure the effectiveness of access policies. Our recent research shows that 87% of privileged credentials are not even used once per quarter. This highlights how traditional practices are falling short. We strive to help customers reach a security posture of zero standing permissions with credentials that only exist when needed and are never exposed to the end user.
To get there, it’s partially about the tools, but also about the people. Asking people to give up standing credentials—which may represent power and status—could be met with resistance but we have some ideas on how to overcome that. More often, people don’t even realize they had those credentials—and that’s a source of risk that could be easily eliminated.
This month, StrongDM is introducing a suite of features to manage secure and dynamic access across your entire stack. It’s time to let go of the past and embrace the present and the future.
Better Enforce Security Policies With Advanced Insights
Advanced Insights: Organizations need to be confident that security policies are being enforced. Admins can now easily report on all the resources and roles of their users. The new Reports Library shows how your most critical resources are used and whether roles are over-privileged or underutilized. Within the reports, admins can continue to track every activity and query with the StrongDM™ Audit API and export logs in a usable and parsable way to your company’s data analytics tools of choice. You’ll also be able to answer common user queries regarding infrastructure access for audits, investigation, and compliance use cases, which makes recertifications accurate and efficient.
Keep Your Secrets Safe
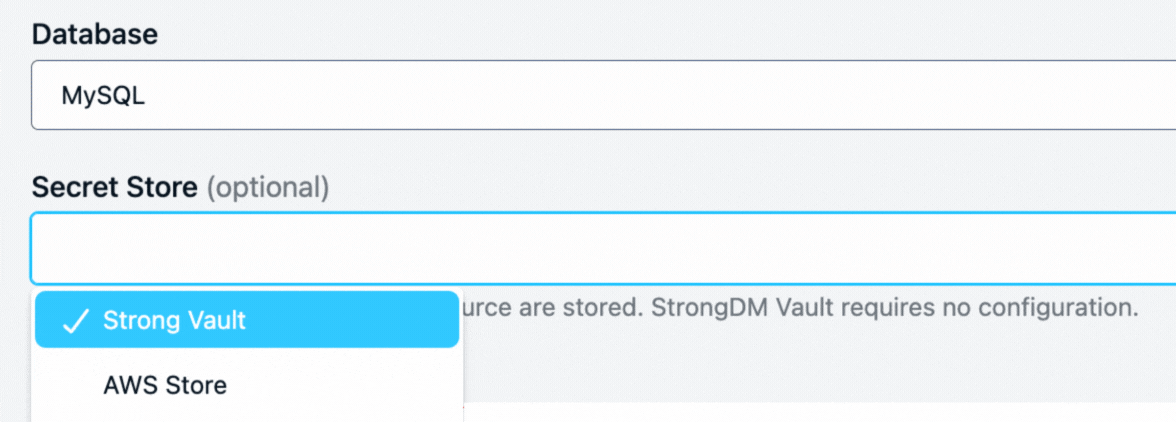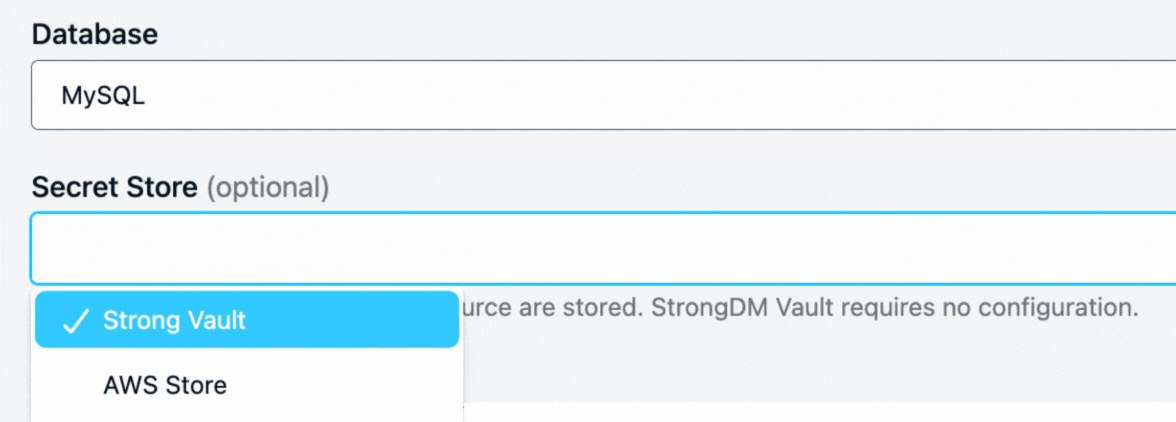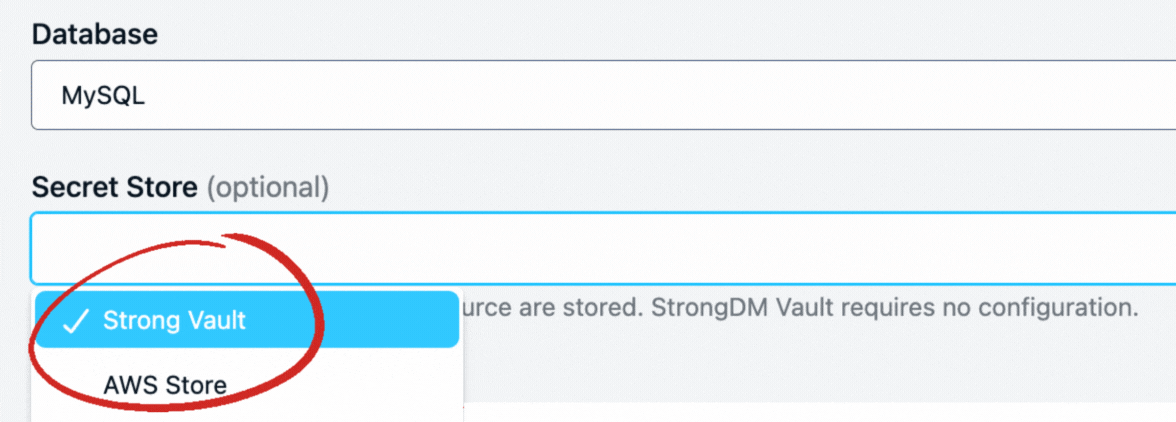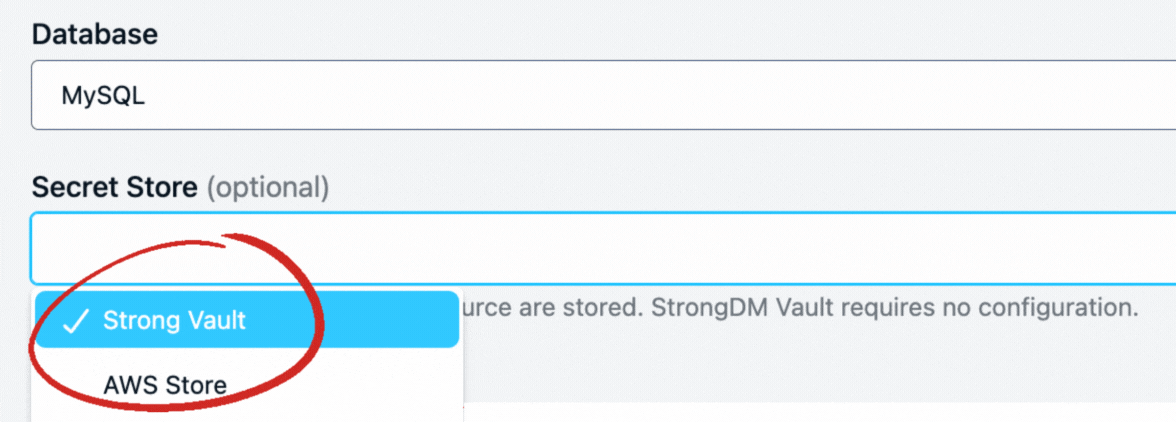
Strong Vault: Protect your organization’s most sensitive authentication tokens from unauthorized access and use. With the Strong Vault you can store, checkout and secure all your secrets, keys, and credentials in one location – or you can continue to use all the vaults/keystores you have across your organization, concurrently. The StrongDM proxy fetches credentials from the vault when access is granted without the credentials ever being exposed to the end user. Supported vaults include Azure Key Vault, CyberArk Conjur, CyberArk Digital Vault, Delinea Secrets Server, HashiCorp Vault, GCP Secrets Manager and Amazon Secrets Manager or the native Strong Vault.
Make Dreams of Zero Trust a Reality
Access Workflows (Closed Beta): Get closer to your Zero Trust aspirations within a few clicks. Access workflows empower customers to easily adopt Zero Standing Privileges to request, approve, and grant access as needed. This new feature supports multi-step processes and change management that are as simple or complex as your security policies require. Every step of the workflow is mapped with an end-to-end chain of events tied directly to audit logs.
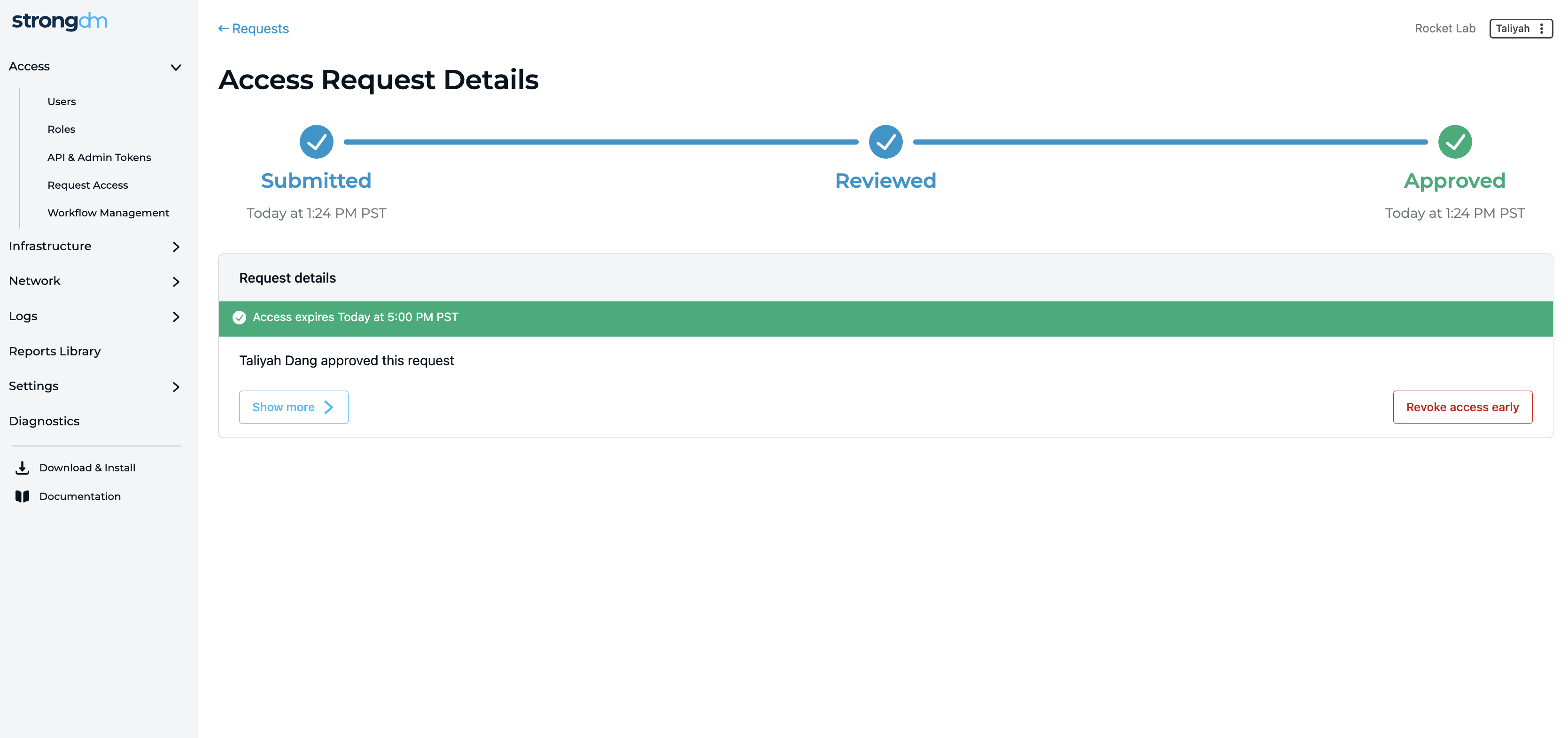
Writing Access Rules Has Never Been Easier
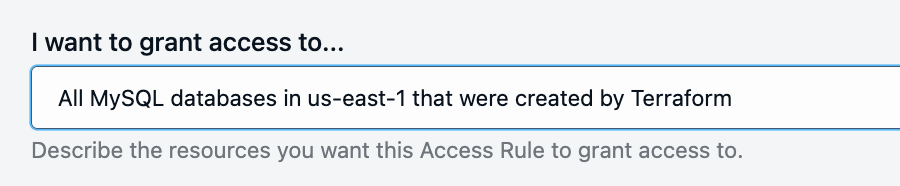
Natural Language Access (Closed Beta): We recognize that putting a written access policy into practice can be hard – especially ensuring that you’ve coded the rule accurately. With the new Natural Language Access feature, admins can create access rules just as simply as writing out the rule in English. Assign resources, create roles, and more.
This new fleet of features is the first step in the ultimate journey of enabling customers to achieve Zero Standing Privilege and dramatically shrink their access attack surface. The adventures in access are just beginning, but you don’t have to go it alone. Let's enter the future together.
Interested in trying our Beta features? Contact info@strongdm.com
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Fazila Malik, Sales Enablement Expert, as an accomplished Product Marketing Manager in the technology industry with over 5 years of experience, Fazila transitioned to a Sales Enablement leader position passionate about empowering go-to-market teams to excel in their roles. Throughout her career, she has worked with a range of technology products, including software applications and cloud-based solutions. Fazila is a member of the Product Marketing Alliance and an AWS Cloud Certified Practitioner. To contact Fazila, visit her on LinkedIn.
You May Also Like




