Striking the Balance: User Experience and Security in Access Management

Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
There is no shortage of complex and nuanced topics in the field of IT. After 16 years in the industry, access management continues to be one of the most sensitive and controversial aspects of the job. But it’s not the technology that makes it difficult. It’s the people.
People don’t like friction. The moment something feels hard to use, people look for a different way to do it. If a tool or a process is not efficient or intuitive, end users will find a way around it. While resourcefulness is a positive trait in many instances, it’s not ideal for access.
Before we talk about access that users love, we need to understand why traditional approaches don’t work for them.
Friction Fuels Frustration
It’s no secret that if a tool is hard to use, or gets in the way of your productivity, your desire to use it decreases, and your desire to work around it increases. Here’s a simple chart:
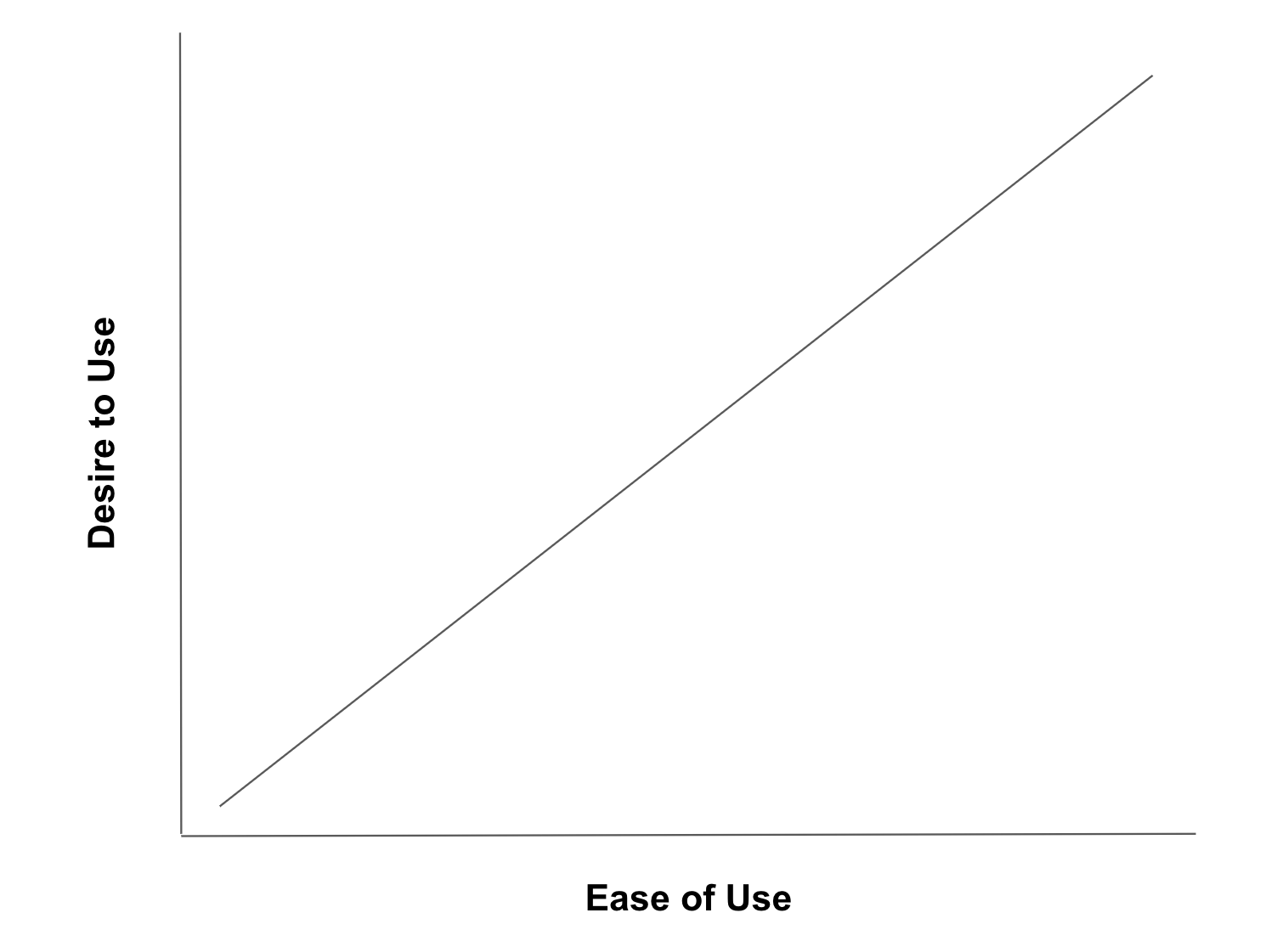
Technical employees in particular rely on access management systems to do their jobs effectively. Without the ability to access the right databases, log into Kubernetes clusters, or add necessary tools to existing access management solutions, productivity and morale suffer.
While this relationship may seem obvious, traditional privileged access management (PAM) tools have (rightfully) earned a reputation for being difficult to implement, use, and administer. So rather than removing barriers and encouraging adoption, they add barriers that spawn workarounds that can actually increase your risk. When productivity and morale take a dive, users adopt shadow IT, share credentials, and maintain backdoor access. Cumbersome tools, tools without proper explanation, and the absence of training or education can also result in workarounds or dropping the tool altogether.
The Access Productivity Gap Persists
StrongDM explored the impact access has on productivity and security in a third-party survey titled, “The Access Productivity Gap”. Here are some of the most telling statistics:
- Access issues consistently impact productivity: 64% of organizations have their productivity impacted on a daily or weekly basis due to access issues.
- Significant time is lost simply accessing infrastructure: 73% of employees require 15 or more minutes to get access to infrastructure, with over a quarter (30%) requiring more than 30 minutes.
- Poor access practices mean missed deadlines: 52% of development teams have missed deadlines due to issues with accessing infrastructure, with 53% of teams being held accountable for the missed deadline even if it was caused by lack of access to the infrastructure.
It's alarming that 57% of organizations take days or even weeks for infrastructure access to be approved and granted. For users, the tension is additive, and the path of least resistance wins more often than not.
For example, research has shown that the moment a security tool is hard to use, people will start to share credentials or shadow IT in order to get around security requirements. Here’s an example of how the user experience of legacy access management tools is making the job harder for employees and teams.
|
Role |
User Experience Challenges |
|
|
|
|
|
Clearly, access is a sensitive topic when productivity and security are on the line. There are a lot of things end users don’t like when it comes to access. So what do they like? That’s a good question, and where StrongDM comes in.
How StrongDM Improves…
The Admin Experience
IT and security teams often have their hands full when it comes to managing and securing access to their entire stack. That’s because each tool typically has its own process and workflow for provisioning and deprovisioning access. This is also why legacy PAM tools have primarily focused only on accounts with elevated privileges (and often only critical infrastructure).
StrongDM delivers an admin experience that greatly simplifies how access is provisioned, deprovisioned, and managed, ultimately making it possible to extend secure access to all accounts, not just those that are privileged. There are a few key features that make this possible:
- Central control plane: a single, centralized location to manage access grants
- Eliminates vault sprawl: StrongDM integrates with virtually every secrets vault, enabling administrators to centrally manage secrets policies
- Integrates with common identity providers: Easily add and remove users and automate the assignment of permissions based on their role in your chosen IdP, such as Okta
By delivering a smooth and intuitive admin experience, it becomes feasible to implement just-in-time access and ultimately Zero Standing Privileges. When forced to use complex or distributed access workflows, it becomes prohibitively difficult and expensive to secure access across your entire organization.
The End-User Experience
DevOps and engineering teams have long struggled with getting access to the tools they need when they need them. The importance of addressing this problem cannot be overstated. Research has shown that when it’s difficult for end-users to securely access their tools, they often resort to unsecure solutions–such as sharing credentials or shadow IT.
StrongDM provides a simple and straightforward approach to find and request access to the tools they need to use. The StrongDM UI provides DevOps and engineering teams with a simple drop-down menu that provides access directly to the tools they need–regardless of where they exist (on-prem or the cloud) and without sharing credentials with the end user or their workstation.
CLI more your thing? You can access resources through StrongDM via the command line as well. The product was designed to make life as easy as possible for end users, making it a product they want to use.
The CISO Experience
When it comes to infrastructure access, one of the biggest gaps facing CISOs and security leaders is visibility. Visibility into who has access, are they using that access, and which tools are actively being used.
StrongDM provides CISOs with the visibility they need to understand infrastructure access across their organization and arms them with the information they need to reduce the attack surface posed by access and credentials.
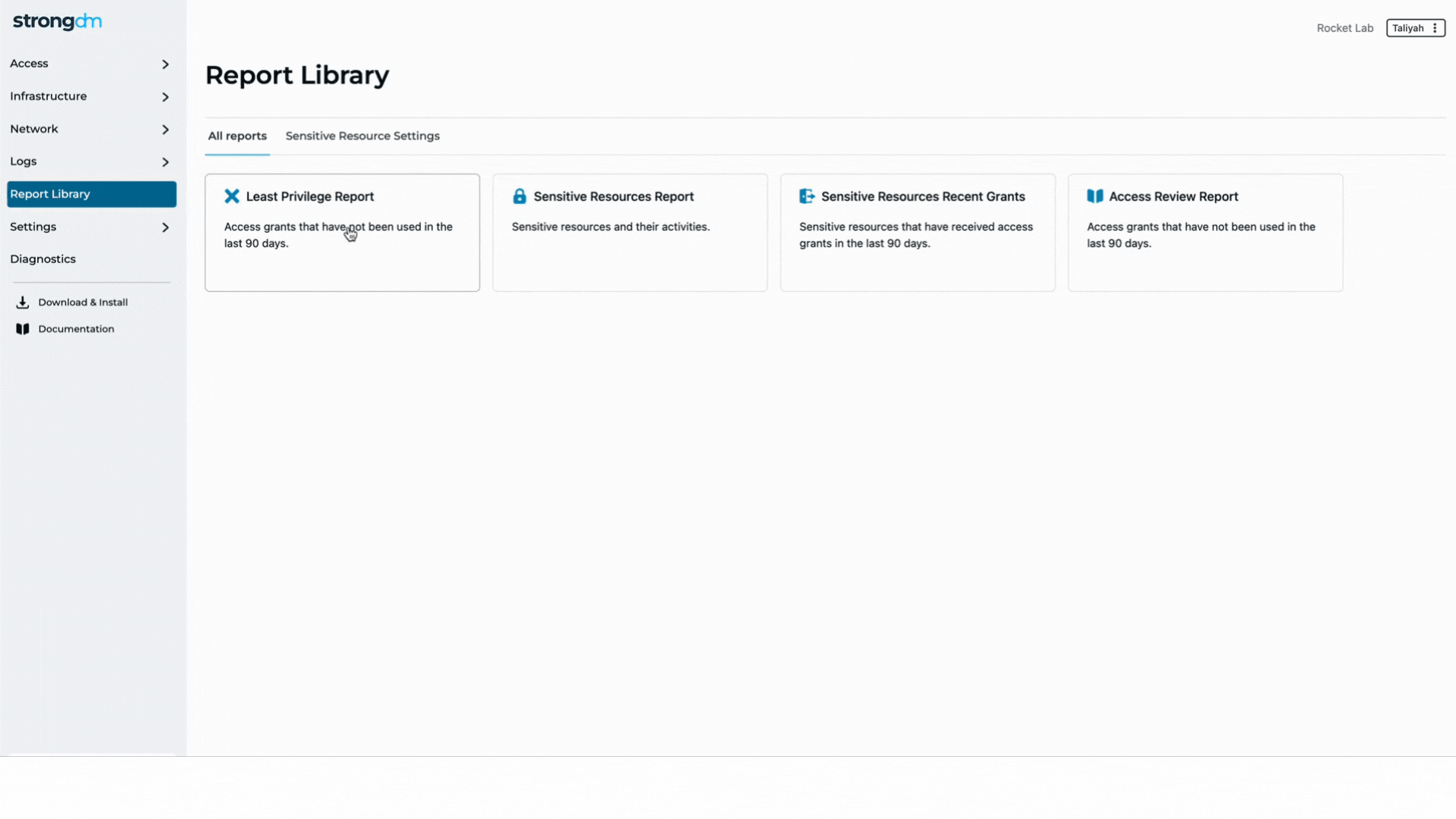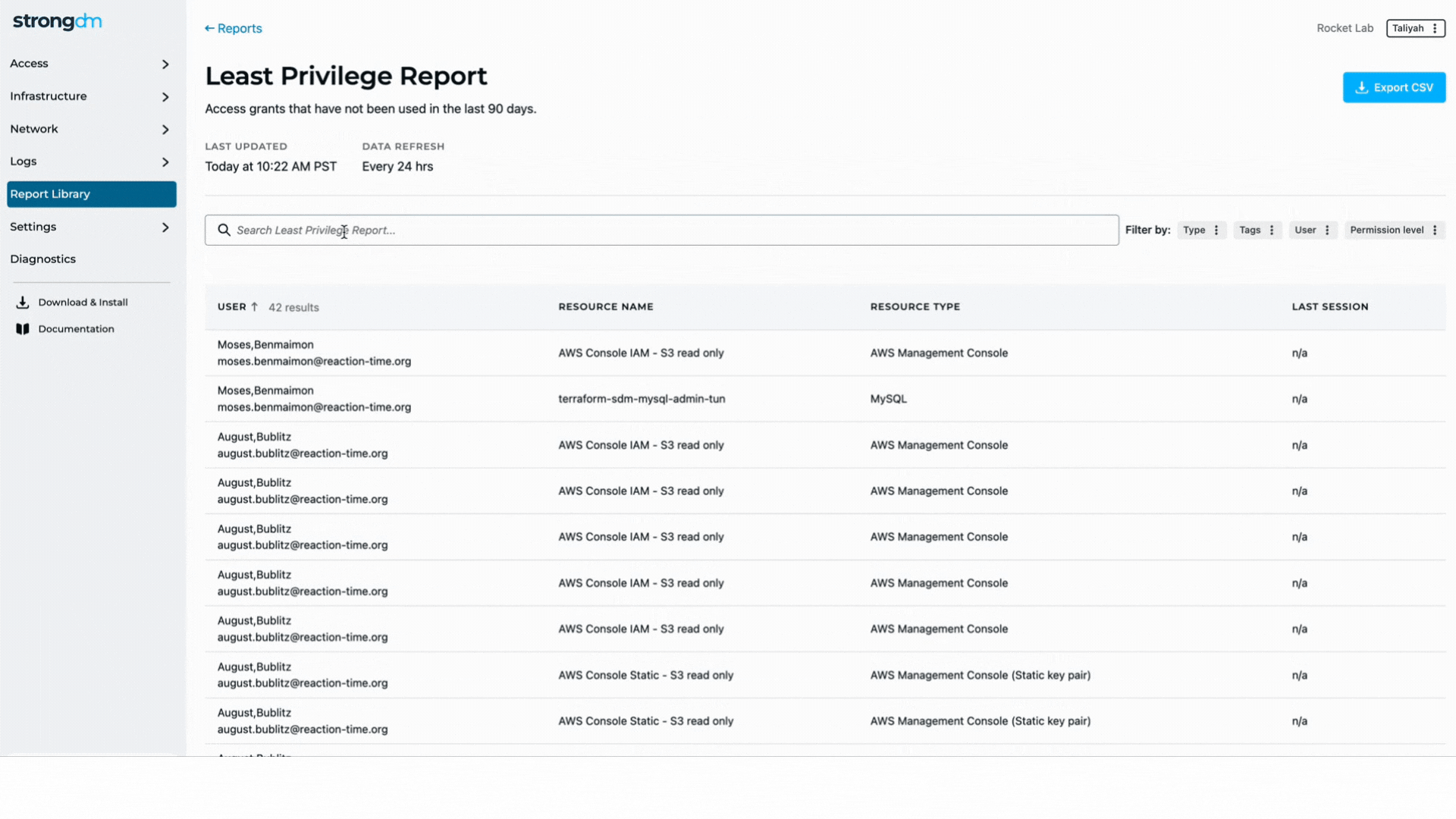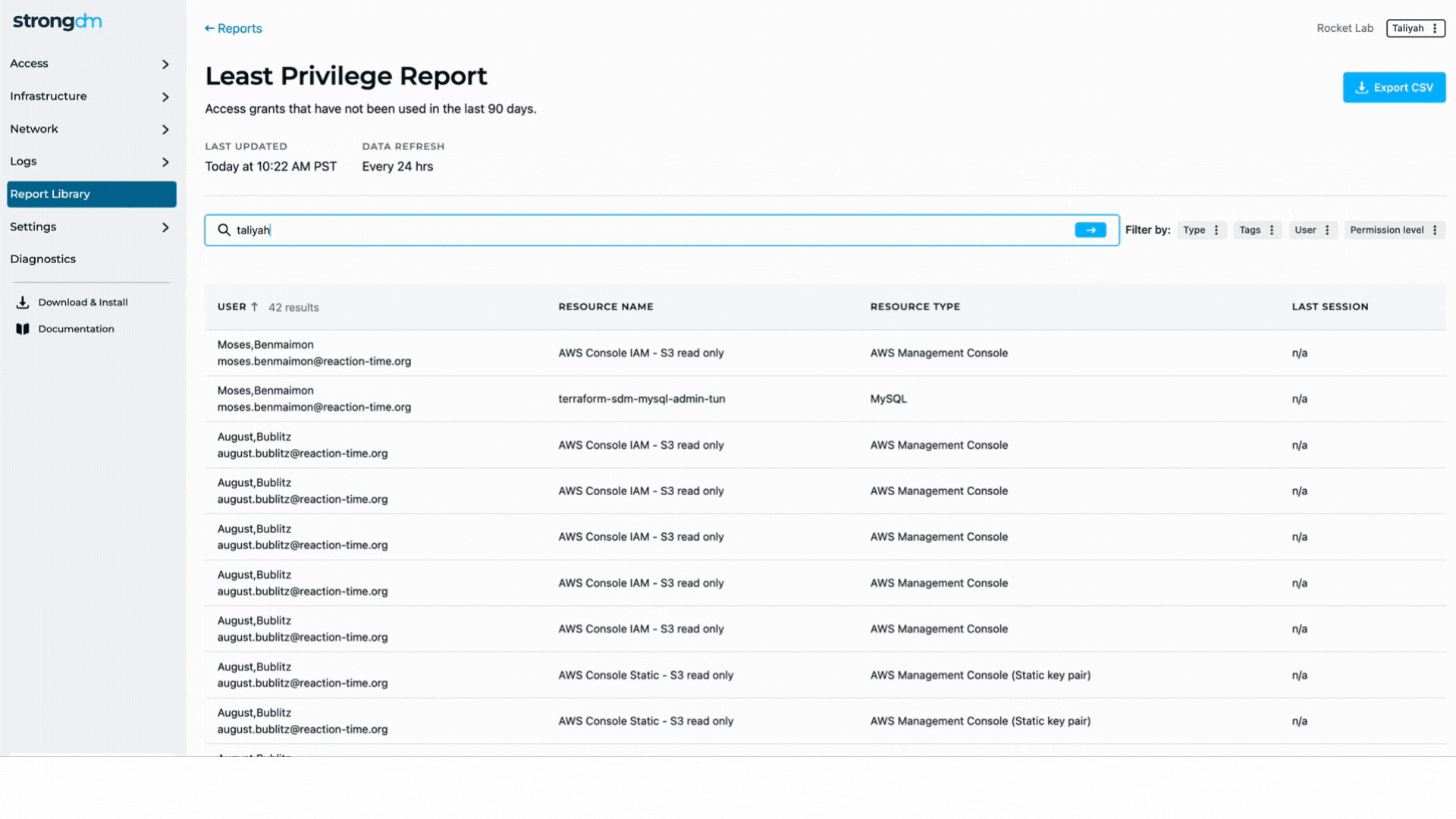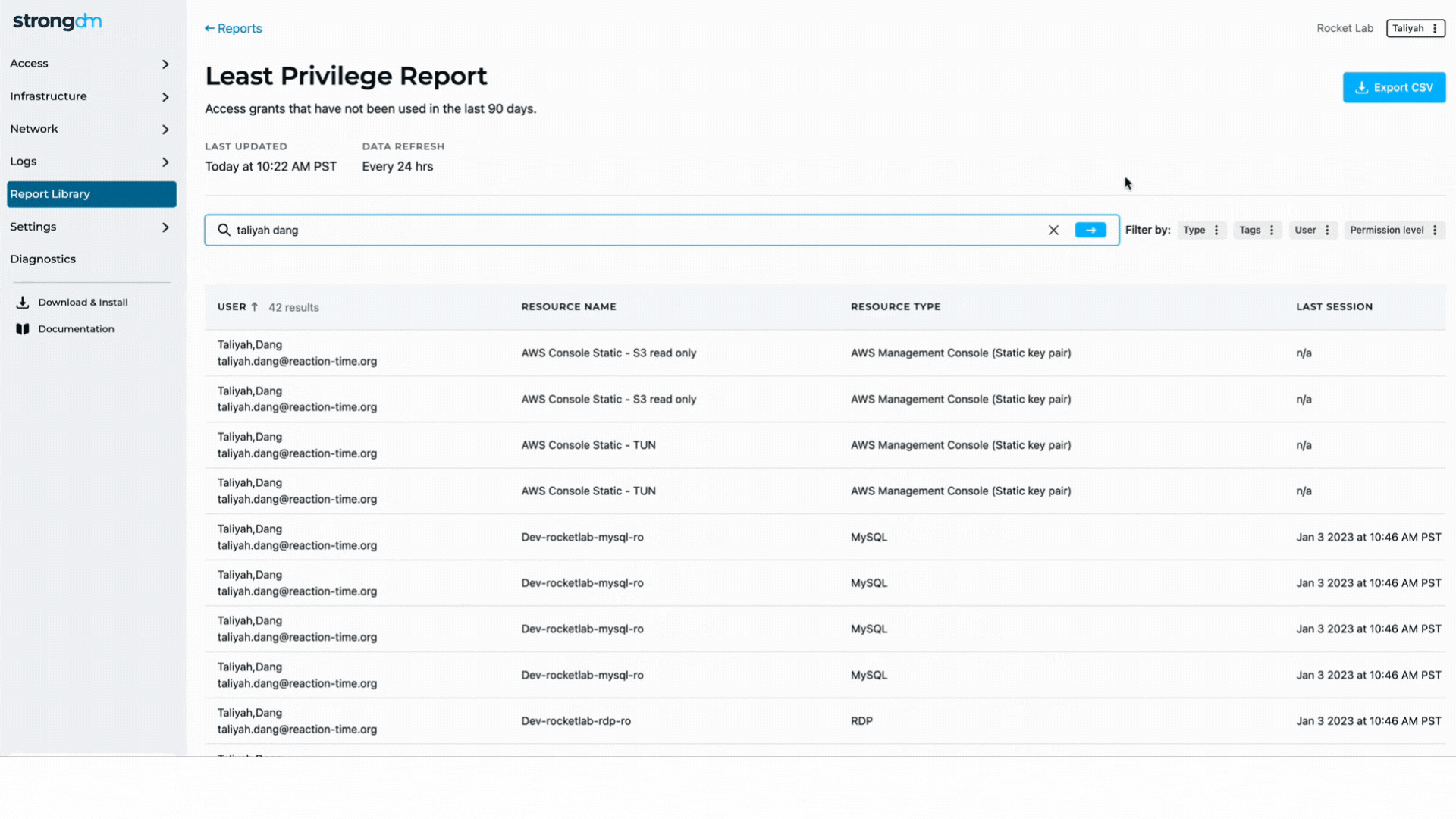
These features include:
- Advanced Insights: With automated reporting, CISOs can get the visibility needed to understand who has privileged access, how often it’s used, and even identifies which resources are not being accessed
- Logging & Auditing: StrongDM provides logging and auditing features that make it easy to tell who had access to which resources, when they had access, and what they did on each system. The logs can also be added to your SIEM or SOAR system, to support existing security initiatives.
- Reduce spend, and increase security: Often, StrongDM customers find that they can retire existing security tools, such as VPNs and legacy PAM tools, while also driving additional security with regard to credentials. This can help lower overall security tool spend, while also reducing the attack surface.
Striking Balance Between Productivity and Security
Striking a balance between productivity and security is crucial, and it begins with adopting tools that prioritize the needs of end users, support the security framework, and respect admin preferences. In this section, we will explore the types of access that users love and discuss the top five capabilities every access management tool should embrace:
1. Superior Ease-of-Use
Tools that follow consistent patterns and conventions make it easier for users to learn and understand permissions and access controls. From the user interface to the help support system, every touchpoint should make it easy to request, approve, and audit access to resources within the organization's technology stack. A user-friendly tool like StrongDM reduces the learning curve and encourages widespread adoption.
2. Low Operational Overhead
Introducing a new tool should not require hiring additional team members or specialized administrators. Unlike CyberArk, the StrongDM interface is so simple, your team won’t need extensive training or dedicated personnel. Minimizing operational overhead in this way not only saves costs but also allows the organization to focus resources on core business activities.
3. Automation and Integration
Through automation, administrators can swiftly handle access requests, approvals, and audits, reducing delays for end users. Intelligent access provisioning, including Just-In-Time, RBAC, or Temporary access capabilities are favorite features within the StrongDM platform. The admin also appreciates being able to expedite access approvals and reduce the time technical teams waste waiting for permissions. Best of all, StrongDM seamlessly integrates with existing systems and tools, encouraging a smooth workflow and user adoption.
4. Streamlined Processes
To enhance productivity and reduce the likelihood of risky workarounds, organizations should strive to streamline access management processes wherever possible. This can be achieved through self-service access controls and technologies such as single sign-on (SSO). These tools simplify the access experience for end users while maintaining strong security controls. Simplified menus and straightforward workflows also contribute to increased efficiency and reduced time spent in the tool.
5. People-Centric Mentality
To bridge the Access Productivity Gap, organizations must put their people first. Access management solutions that put people first prioritize ease of use, efficiency, and timely access approvals. Tools should enhance productivity, not hinder it. By implementing a user-friendly and intuitive platform like StrongDM, organizations spare frustration for end users, admin, and security.
Getting to a better access experience
The user experience cannot be overlooked when it comes to improving security. Driving the adoption of security tools can be extremely difficult, but it doesn’t have to be. It all comes down to finding tools that go beyond making your organization secure, they also need to make the lives of their users easier.
By adopting an access management tool that aligns with the needs and preferences of end users, organizations can create a resilient and efficient technical environment. Remember, the key is to strike a balance between productivity and security. So, I urge leaders to empower end users with tools they love and watch as productivity soars while security stands tall. These goals don’t have to be mutually exclusive.
Want to learn more? Sign up for a StrongDM demo.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Brad Schaider, Senior Manager, IT, is a versatile wrangler of technology who has spent the past 20 years maintaining computer systems in academia, the entertainment industry, and software startups. Driven by the mantra of constant improvement, he aims to streamline and automate every touchpoint. Alongside his technical prowess, Brad possesses a unique talent for steering conversations toward his passion for food (BBQ). He thrives on playing with new technologies, especially when it involves tinkering with hardware and gadgets. Additionally, he finds joy in assisting others with their tech issues, fostering a social and supportive IT team environment. Along Brad’s journey, he amassed an impressive 100+ feature film credits, listed on his IMDB page.
You May Also Like




