Cedar Policy Integration
Integrating a robust authorization framework like Cedar Policy Language (CPL) into existing systems and applications is a pivotal step towards fortifying security posture: various techniques can be employed, each with unique advantages and capabilities.
Techniques for integrating CPL into existing systems and applications
Cedar API: Cedar extends a suite of APIs to integrate its policy language into the existing infrastructure. The APIs facilitate real-time policy enforcement and decision-making within applications, thus acting as the nervous system that transmits authorization signals across the application ecosystem. By employing Cedar's APIs, organizations unlock the avenue to a seamless integration experience, allowing for real-time interactions and decisions crucial for maintaining a robust security perimeter.
Cedar SDKs: SDKs are tailored for various programming environments. These SDKs are the bedrock for embedding policy decision points within applications, thus forging a symbiotic relationship between the application logic and the authorization framework. The beauty of Cedar's SDKs lies in their ability to assimilate within different programming paradigms, offering a versatile solution for integrating the Cedar Policy Language into a diverse range of applications.
Custom Adapters: Adapters are crafted to bridge the chasm between Cedar and existing systems, acting as the translators that decode the language of Cedar so that it is understandable to the existing systems.
Benefits and challenges associated with Cedar Policy integration
Integrating Cedar Policy Language (CPL) into existing systems brings notable benefits. Primarily, it enhances security by providing a robust framework for defining and enforcing authorization policies. The granular access control feature of Cedar allows precise permissions management, ensuring that resources are accessed only by authorized entities. Moreover, real-time policy enforcement is a critical advantage, enabling immediate response to authorization requests, essential in dynamic and high-stakes environments. Compliance with industry regulations is another benefit, as Cedar can be configured to enforce policies that adhere to various regulatory standards, making it a viable choice for regulated industries like finance and healthcare.
On the flip side, developers may encounter challenges during the integration of Cedar. The initial setup can be complex, requiring a good understanding of Cedar to ensure correct configuration and integration. This highlights the necessity for expertise in Cedar for successful implementation. Additionally, thorough testing is crucial to validate that the policies are enforced correctly and identify potential issues early in the implementation process. This testing phase is not just a one-off task but an ongoing requirement to ensure the Cedar integration continues functioning as expected amidst evolving system and application landscapes.
For StrongDM customers, we’ve done the difficult work of integrating Cedar into our Zero Trust PAM Platform. Utilizing Cedar policies for fine-grained authorization requires no rewrites to your existing applications. Amazing!
Cedar Policy Management & Administration
Policy management and policy administration, though closely related, serve distinct functions within an organization's security framework.
Policy Management
Definition and Revision: Policy management primarily involves the creation, updating, and deletion of security policies. It entails defining the rules and conditions under which resources can be accessed within a system.
Deployment: It includes deploying these policies across the organization's network, ensuring they are applied correctly wherever necessary.
Monitoring and Enforcement: Policy management also involves monitoring the enforcement of these policies and making adjustments as needed to maintain the desired level of security.
Compliance Checking: Ensuring that the set policies comply with external regulations and internal standards is a part of policy management.
Performance Monitoring: Monitoring how policies affect system performance and making necessary adjustments falls under policy management.
For effective Cedar policy management across different applications, a centralized policy repository is essential. It acts as a single source of truth for all authorization policies, ensuring consistency in enforcement across applications. Automated deployment pipelines are another critical requirement, facilitating the swift propagation of policy updates across different environments. Real-time monitoring and alerting mechanisms are also vital to keep track of policy enforcement and to identify any anomalies promptly.
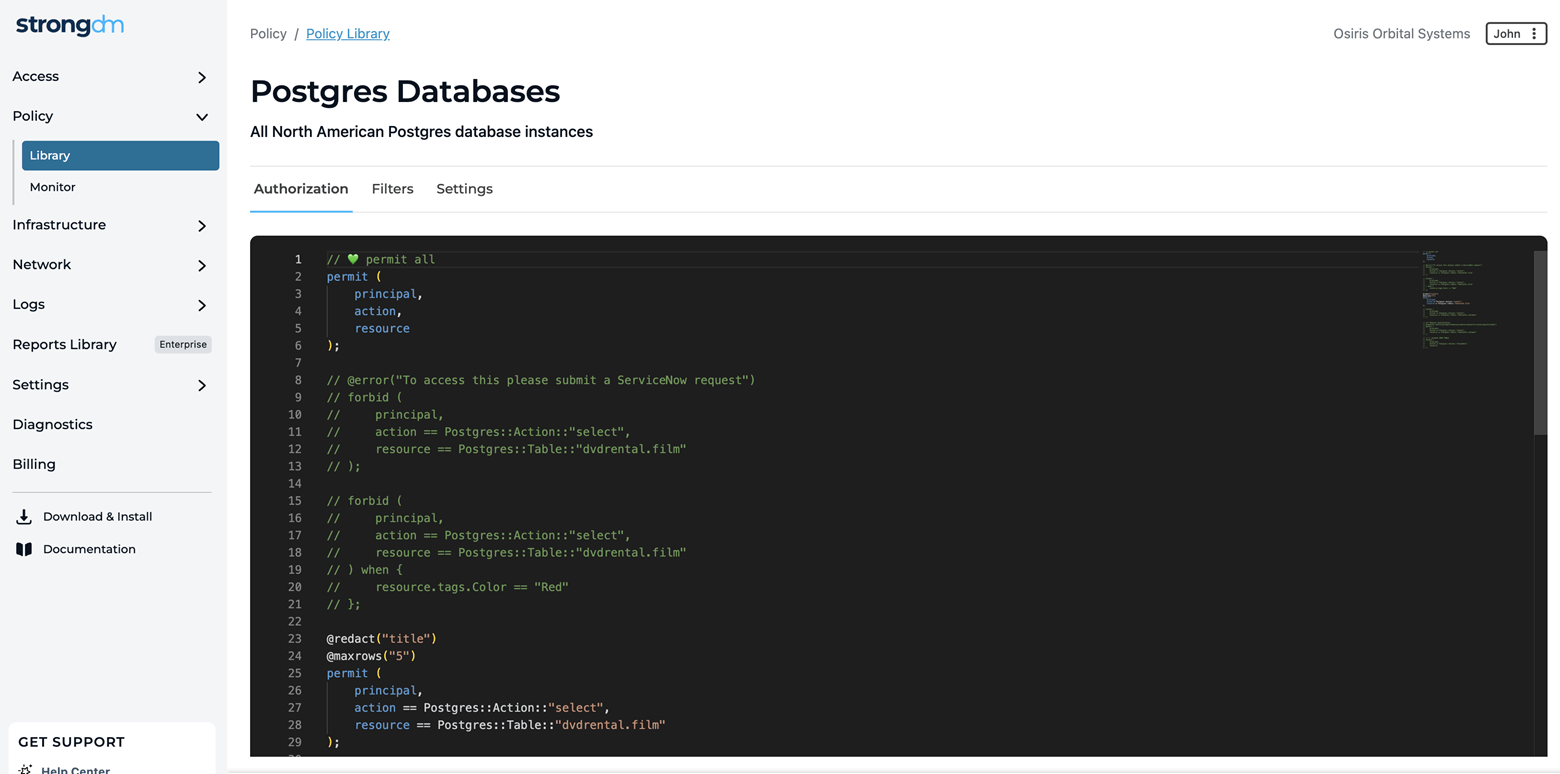
The robust Strong Policy Engine by StrongDM™ is powered by the Cedar Policy Language. This enables distributed enforcement of centralized policies, creating a secure and unified access control framework across your infrastructure. The engine allows for policy evaluation with sub-millisecond response times, aligning with the high-performance standards that StrongDM users expect.
With centralized policy management policies are written once and enforced everywhere. StrongDM simplifies policy management by extending existing RBAC and ABAC policies with new signals and controls. This centralized approach streamlines administration, reducing the complexity of access control. With StrongDM, you can establish security measures that are uniformly enforced across all your diverse applications and infrastructure components. It builds upon the natural strengths of these resources by adding layers of security policies, thereby improving the existing controls and safeguards.
Cedar Policy Management & Administration
Policy management and policy administration, though closely related, serve distinct functions within an organization's security framework.
Policy Management
Definition and Revision: Policy management primarily involves the creation, updating, and deletion of security policies. It entails defining the rules and conditions under which resources can be accessed within a system.
Deployment: It includes deploying these policies across the organization's network, ensuring they are applied correctly wherever necessary.
Monitoring and Enforcement: Policy management also involves monitoring the enforcement of these policies and making adjustments as needed to maintain the desired level of security.
Compliance Checking: Ensuring that the set policies comply with external regulations and internal standards is a part of policy management.
Performance Monitoring: Monitoring how policies affect system performance and making necessary adjustments falls under policy management.
For effective Cedar policy management across different applications, a centralized policy repository is essential. It acts as a single source of truth for all authorization policies, ensuring consistency in enforcement across applications. Automated deployment pipelines are another critical requirement, facilitating the swift propagation of policy updates across different environments. Real-time monitoring and alerting mechanisms are also vital to keep track of policy enforcement and to identify any anomalies promptly.
Policy Administration
Centralized Control: Policy administration usually refers to the centralized control and oversight of all policy management activities. It's about overseeing how policies are created, modified, and deleted.
Access Control: This includes managing who has the authorization to create, modify, or delete policies, thereby ensuring only qualified individuals can make changes to policies.
Audit Trail: Maintaining a comprehensive audit trail of all policy changes, including who made the changes and when, is a crucial aspect of policy administration.
Reporting and Analysis: Generating reports and analyzing data regarding policy enforcement, violations, and compliance levels fall under policy administration.
Training and Awareness: Ensuring that staff is adequately trained on policy-related matters and is aware of the importance of compliance is also a part of policy administration.
Having centralized administration for managing and monitoring Cedar policies is crucial. It simplifies governance by consolidating management and monitoring into a single point, providing clear oversight on policy enforcement and compliance. Centralized administration is necessary for compliance auditing as it offers a coherent audit trail of policy configurations and enforcement actions.
In a nutshell, policy management is more about the lifecycle of the policies themselves (creation, deployment, monitoring, and enforcement). In contrast, policy administration is about governance, control, and oversight of policy management activities. Both are crucial for maintaining a robust and compliant cybersecurity posture within an organization.
The Cedar Policy Language: Features, Syntax and Ecosystem
Cedar Policy Language enables precise and intelligible authorization policy authoring. This structured approach accelerates integration into existing systems and simplifies the management of policies, ensuring coherent governance over authorization. Moreover, the real-time policy evaluation capability of CPL is crucial for dynamic environments where authorization decisions need to be made swiftly. When juxtaposed with other policy languages, Cedar's emphasis on application-level authorization and its ability to articulate fine-grained policies shine through. The comparative simplicity and precision in policy definition give CPL an edge, making it a preferred choice for many cybersecurity professionals.
In this document, we will not detail the specifics of the Cedar syntax, operators, validation, grammar, or templates. For those details, please refer to the Cedar documentation.
Cedar Syntax
A standout feature of Cedar is its structured syntax, designed to articulate policies clearly, thus facilitating easy integration and management. Each policy statement describes how a user (Principal) is allowed to interact (Action) with a service/application (Resource) under a particular condition (Context). This is also known as the PARC model.
While Open Policy Agent (OPA) utilizes Rego as its policy language, Cedar's syntax is constructed to provide a potentially more straightforward approach to policy definition. To illustrate, consider a simple policy that allows read access to a resource:
Cedar Policy
permit (
principal,
action == Action::"read",
resource
);
OPA Rego Policy
default allow = false
allow {
input.action == "read"
}
Cedar Policy Language Ecosystem
An emergent yet vibrant community surrounds Cedar, comprising cybersecurity professionals, developers, and organizations. In the Slack community you'll find not only a forum for discussion and troubleshooting, notices about events and new releases, as well as resources for learning and implementation. The availability of comprehensive language documentation, SDK documentation, tutorials, and policy playground makes mastering Cedar and implementing it in operational environments more manageable. Furthermore, the active engagement of the community in evolving the Cedar Policy Language, sharing best practices, and providing support underscores the collaborative spirit that drives the continuous refinement of Cedar.
Automated, Distributed Enforcement of Cedar Policies
Distributed policy enforcement is a methodology that decentralizes enforcement so that it occurs across various points within a network or system. One of the primary benefits of distributed policy enforcement is the granular control it affords over diverse resources - custom applications, SaaS applications, data stores, servers, Kubernetes clusters, and various IT infrastructure – all across an organization's digital landscape.
Here's a breakdown of how it operates:
Decentralization: Unlike centralized enforcement, where policies are enforced at a single point or a central location, distributed policy enforcement spreads enforcement across multiple points in the network or application infrastructure.
Local Enforcement: Each enforcement point operates locally, making decisions based on the policies defined for that particular point. This local enforcement allows for faster decision-making and reduces the latency that might occur if requests had to be sent to a central location for processing.
Policy Consistency: Despite the decentralization, the policies are consistent across the system. They are defined centrally but enforced locally, ensuring a uniform security posture across the entire network.
Scalability: A distributed enforcement model scales efficiently as it can handle an increasing number of enforcement points without requiring a proportionate increase in central resources. This scalability is essential for large, distributed systems where centralized enforcement might become a bottleneck.
Real-time Authorization: With enforcement points located throughout the system, real-time authorization decisions are made locally, ensuring immediate response to requests based on the prevailing policies.
Adaptability: The distributed nature allows for more adaptable enforcement, as local enforcement points can adjust to local conditions while adhering to the global policy framework.
Improved Performance: By reducing the need for centralized processing of authorization decisions, distributed policy enforcement can improve system performance and user experience.
Automation plays a pivotal role in elevating the efficacy of distributed policy enforcement. Tools like AWS Verified Permissions and StrongDM Zero Trust PAM are instrumental in this context, offering avenues for seamlessly automating policy enforcement using CPL. These tools not only streamline the deployment of Cedar policies but also ensure consistent enforcement across different systems and applications. Through automation, organizations can manage and enforce policies dynamically, adapting to the evolving security landscape with agility.
The synergy between centralized Cedar policies and distributed policy enforcement provides a robust framework for managing fine-grained authorization. By leveraging automation tools like AWS Verified Permissions and StrongDM Zero Trust PAM, organizations can significantly enhance their security posture and get closer to their Zero Trust goals.
Enforcement can take one of several paths: allow, deny, or trigger a workflow for additional approval or authentication. Admins can design automated authorization workflows to activate further authentication (MFA or 2FA) or additional approvals under certain conditions or scenarios. This process, often called Multi-party authorization (MPA), enhances security and ensures that sensitive operations are adequately reviewed or verified.
Real-world examples of Cedar Policy in various domains
The versatility of Cedar policies shines through as we explore some examples of how it could be implemented across various industries.
Financial Services: Every Financial Services organization has to be a fortress of sensitive data, where layers of authorization policies protect every transaction and every account detail. Implementing Cedar can greatly simplify the enforcement of fine-grained authorization policies in banking applications to bolster security and ensure a compliant, secure environment for managing financial transactions and sensitive data.
Healthcare: In healthcare organizations, Cedar can help safeguard sensitive patient data. Employing Cedar to manage access control in Electronic Health Record (EHR) systems is not just a technological integration but could save lives. Cedar's role in managing access control ensures that only authorized personnel can access and modify patient records, thus building a robust shield against unauthorized access and potential data breaches.
E-Commerce: The multi-tiered architecture of e-commerce platforms is a fertile ground for potential security threats. The integration of Cedar enhances security without compromising on user experience, striking a delicate balance that is crucial for fostering trust and ensuring a seamless shopping experience.



