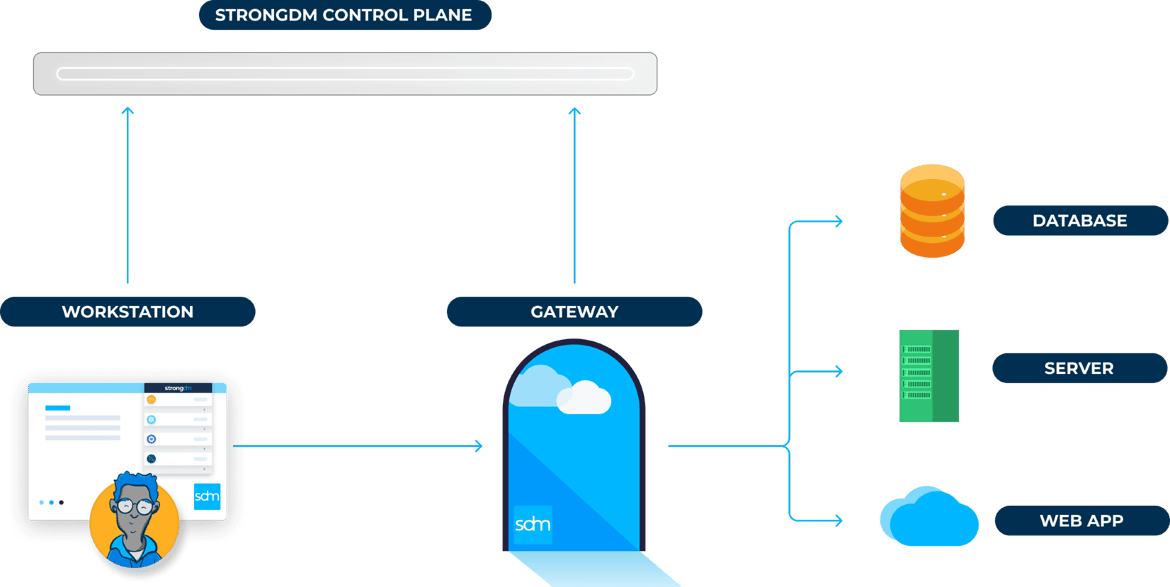
The Local Client
The local client tunnels requests from the user’s workstation to the gateway, through a single TLS 1.2-secured TCP connection. StrongDM supports Mac, Windows, and Linux workstations.
To authenticate, users login to the local client; that call can be optionally redirected to your identity provider or SSO.
The local client consists of both graphical and command-line interfaces.
The Gateway
Gateways are the entry point to your network. They can be deployed with a DNS entry, sit privately on the corporate network, and/or behind a VPN.
In the case of a flat network, it is the gateway that talks to the target systems. If internal subnets disallow ingress, relays create a reverse tunnel to form connections to the gateway. All data routes through your network.
Gateways decrypt credentials on behalf of end users, and deconstruct requests for the purposes of auditing.
Gateways and relays are deployed in pairs, and scale horizontally.
Configuration Layer
The Admin UI houses configuration. Users are assigned to roles, and roles are collections of permissions across servers, databases, clusters, and web apps. Configuration is pushed down to the end user's local client, and updated in real-time.
Trusted by:


StrongDM Design Principles
Zero Trust means that determining whether a user (person or machine) should have access to a system or data needs to be assessed throughout every session, not only when they attempt access.
Using risk-based assessment, access needs to be severed immediately if trust is no longer achieved.

See StrongDM in action. 👀