
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
One thing is clear in the software space: New features aren’t adopted if they don’t solve specific problems for the people who actually use the product. Solving real problems means conducting research and asking hard questions. It means gathering evidence and interviewing multiple customers as well as leaders in the space to relieve the pain and positively impact the business.
So when it came time for StrongDM to roll out new features to help us innovate the PAM space, we embarked on a research journey with some of the top movers and shakers in security, IAM, and PAM. Here’s what we found.
Security Leaders Have A Credential Problem
Our survey proved that 85% of privileged credentials are not used on a quarterly basis—not once. To understand why this happens so often, we enlisted a team of twenty CISOs to help us dig deeper. We heard the same three answers repeatedly in our focus groups:
- Leaders don’t know who owns legacy credentials so they can’t hold owners accountable.
- Managers insist their teams need access to things that they don’t really need.
- No one knows which credentials are NOT actively used; making housekeeping difficult.
These three discoveries inspired the development of Advanced Insights with StrongDM.
How Do We Solve This Credential Problem?
You can’t solve what you can’t see. Advanced Insights combines StrongDM Audit API with a new Reports Library to give leaders visibility into how access is being used and help them enforce least privilege access. Together, these technologies enable organizations to have total visibility over their access grants.
StrongDM Audit API
This tool enables audit logs to be exported into an organization’s security or data analytics tools of choice in a usable and parsable way. The StrongDM API also allows users to programmatically interact with their organization in StrongDM in order to create, remove, or manage users, roles, permissions, gateways, relays, resources, and more.
Specifically, users can use the StrongDM API to do the following:
- Audit the permissions staff have to backend infrastructure like databases, servers, and clusters
- Identify which permissions staff have not used recently
- Revoke unused permissions to enforce least privilege
- Identify which staff have permission to access sensitive systems
- Audit every query and command executed during sessions on sensitive systems
It’s an important tool that enables many of our most powerful features across the StrongDM platform.
Reports Library
Powered by StrongDM’s Audit API, this library provides admins with a complete view of resources and roles that are overprivileged and underutilized, as well as reports to track all user activity across the entire infrastructure.
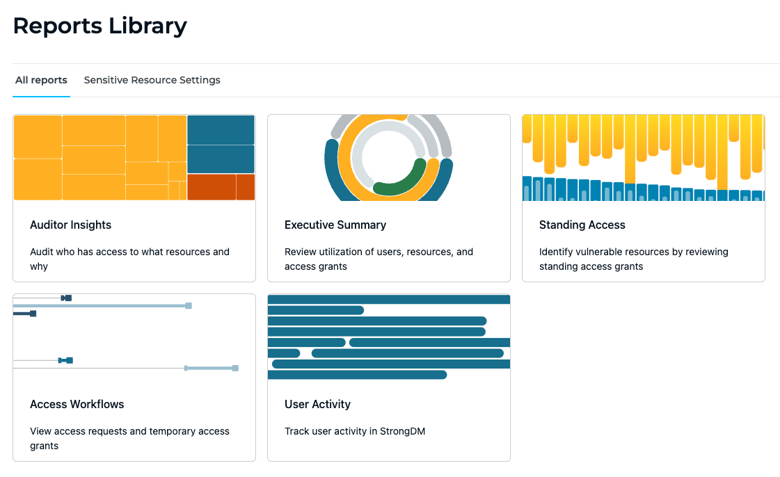
You Have Questions; We Have A Report For That
Each report within the library will allow you to answer critical questions to prove security best practices are enforced across the entire backend tech stack. These questions were voted the most pressing (and anxiety-inducing) by our team of experts.
Q: How effectively are you enforcing least-privilege access? 🔎
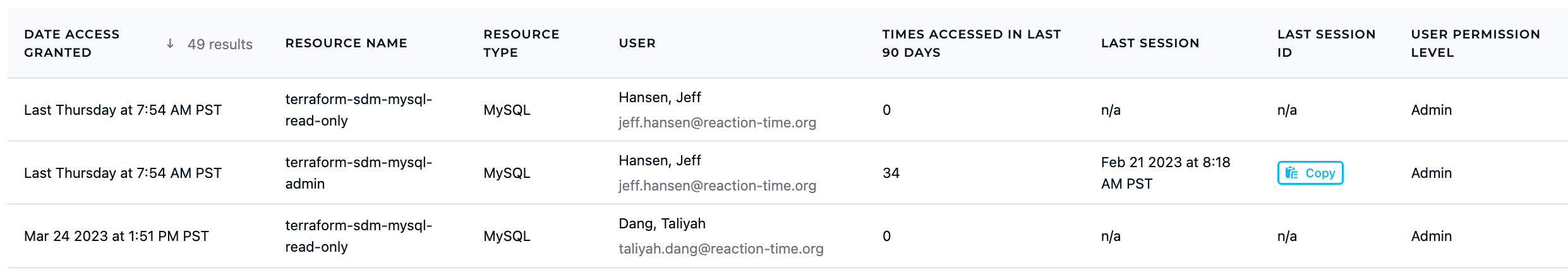
A: Use the Standing Access dashboard to view what permissions have not been used over a specific time period. Revoke any unused access privileges or implement workflows for Just-in-time access.
Q: How quickly can you complete a recertification campaign? 📝
A: Try our Auditory Insights dashboard to know exactly who has access to what, through which role at any given time. Complete audits more efficiently with out-of-the-box reports for access policy questions.
Q: Who has access to sensitive systems? 🔐
A: Review the User Activity dashboard to see how many sessions occurred, and for how long. Create alerts for unusual behavior. Better understand access behavior patterns around your most sensitive resources.
If any of the questions presented make you feel a little weary or uncertain, let’s have a conversation. We’d love to show you Advanced Insights in action.
Each report within Advanced Insights will allow you to answer critical questions to prove security best practices are enforced across the entire backend tech stack. These questions were voted the most pressing (and anxiety-inducing) by our team of experts.
Why Advanced Insights?
Leaders needed a way to see what was previously unseen. They also needed a way to answer questions that they couldn’t answer before. Who really has access? How often do they use it? And do they really need it? With Advanced Insights, you can see the unseen and answer the unanswerable.
Sure, Advanced Insights gives leaders and managers a direct line of sight to the most critical questions in their inboxes, but there’s a bigger picture here. Below are just a few scenarios that Advanced Insights will simplify:
- Zero Trust initiatives - Like least privilege access
- Digital transformation - Support for Kubernetes and the modern tech stack
- Cloud migration - Support for multi-cloud
- Compliance requirements - Streamline recertification
- Cost reduction - Do more with less
Conclusion
We don’t do vanity features at StrongDM. Because vanity features lead to vanity metrics. And vanity metrics don’t fool anyone. They certainly don’t move the needle for CISOs, architects, and IAM leaders. Advanced Insights is just one of the many new features we are rolling out this year to make Zero Trust access a reality for more organizations. Stay tuned for more!
Check out this blog for the scoop on all our new tools and reports.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Angela Donlan, Content Manager, Angela supports the marketing team by developing creative content that helps StrongDM tell its story in creative and authentic ways. Experienced in the advertising agency space and the consulting world, Angela spent her early career years serving as a client-facing writer and project manager for brands large and small. Her specialties range from brand development and strategic campaign planning to social media execution and long-form content production. Angela obtained her Bachelor of Science in Business Administration from the University of Tulsa. She majored in Marketing and Management and completed minors in Advertising and Communications during her time at TU. To contact Angela, visit her on LinkedIn.
You May Also Like




