Latest blog posts from Schuyler

In today's rapidly evolving digital landscape, the concept of cyber resilience has taken center stage. This resilience refers to an organization's capacity to not only withstand but thrive in the face of cyber emergencies, such as the escalating menace of cyber attacks. This article delves into the critical importance of cyber resilience, shedding light on the ever-growing challenges and threats faced by organizations today, and how the right framework, like StrongDM, can fortify an

Want a secure and compliant AWS environment? Then you need to audit access. Keeping tabs on who has accessed what—as well as the whens, wheres, and whys—helps you spot suspicious activities and address them promptly. Without this kind of access control, your sensitive data could be exposed to malicious actors, putting you at risk of data breaches and subsequent regulatory nightmares or service interruptions.

When it comes to cloud security, AWS follows the Shared Responsibility Model. They secure the underlying infrastructure while you protect your data, applications, and systems—including the identities that access them. Integrating AWS with a dynamic access management tool like StrongDM is key to securing identities in the cloud. StrongDM centralizes access control, while AWS offers robust security measures, contributing to a solid defense against unauthorized access.
Secure access controls must be applied universally and consistently across all your infrastructure—from the Linux boxes in your datacenter to your Kubernetes clusters in AWS. StrongDM Dynamic Access Management is uniquely positioned to provide seamless, secure access across your entire stack, simplifying access management and compliance for your legacy systems and modern cloud stack.

AWS authentication confirms the identity of users trying to access your resources, safeguarding against potential intrusions and data breaches. But weak authentication practices—like easy-to-guess passwords and single-factor authentication (SFA)—are far too common and they leave the door wide open for threat actors. Weak authentication often leads to data theft, resource misuse, financial and reputational nightmares…the list goes on. On the contrary, strong authentication measures like

Organizations must meet comprehensive cyber insurance requirements to qualify for coverage. This article defines seven key cybersecurity insurance requirements. Adhering to these requirements will ensure you’ve covered your bases in case of a claim.

In the 1990s, the TV series “The X-Files” made the phrase “Trust No One” popular. Now, with cybercrime increasing at an alarming rate, “trust no one” – or Zero Trust – is a phrase echoing through enterprises. In 2021, the average number of cyberattacks and data breaches increased by 15.1%. That same year, the U.S. government spent $8.64 billion of its $92.17 billion IT budget to combat cybercrime. It also released the CISA Zero Trust Maturity Model.
Networking decisions can be challenging, and no one wants to make a costly mistake. The information in this article will help you understand how SD-WAN and VPN compare, so you can decide which option fits your organization best. You can find a networking solution that provides your employees with a secure internet connection while meeting your business needs and budget.

Cloud computing isn’t a trend, it’s how businesses grow. In 2022, most enterprises said they use cloud services, and more than half say they plan to spend even more on cloud applications and infrastructure in 2023. Cloud scalability offers flexibility at a reasonable price, making it an important business tool. In this article we’ll discuss what scalability is in cloud computing, the benefits of cloud computing scalability, and discuss ways businesses use scalability.
At any given moment, your network may be under attack. Are you prepared? Broken API authentication can expose your data and let hackers in. A data breach compromises an organization as well as its customers, destroying trust and losing customers. Don’t worry, though. The API security best practices in this article help you protect your network from malicious attacks.

On the heels of President Joe Biden’s Executive Order (EO) 14028, the memo recommending Zero Trust Architecture to protect US government computers, the US Department of Defense (DoD) issued its own Department of Defense Zero Trust Strategy. Published in October 2022, the DoD Zero Trust Strategy addresses the rapid growth of cyber threats and the need for an enhanced cybersecurity framework.

A continuous integration, continuous delivery pipeline—or CI/CD pipeline—is a process workflow companies use to streamline and automate software development. A CI/CD pipeline automatically builds and tests code changes to detect bugs before the new code is merged and deployed.
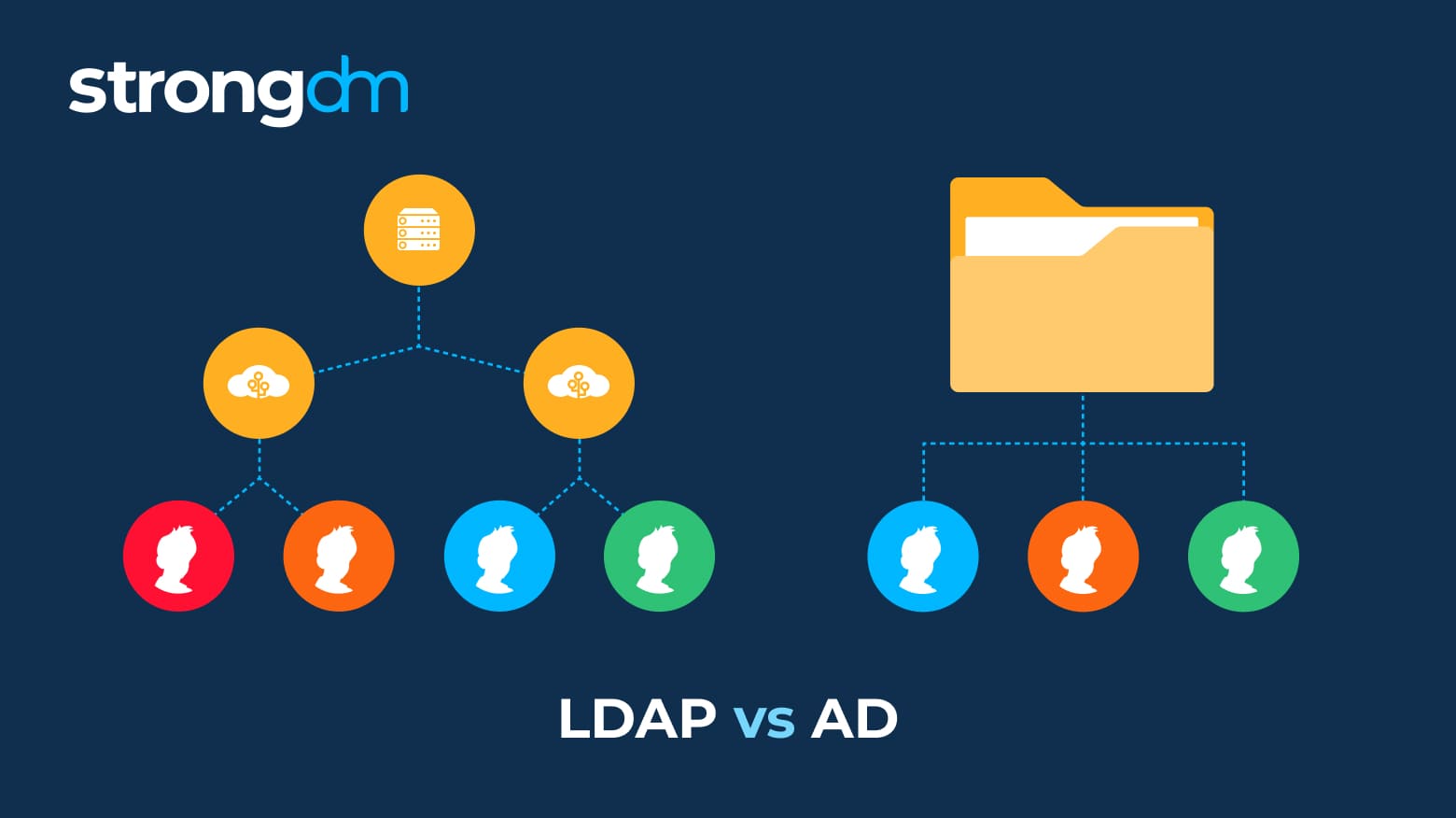
Struggling to understand the difference between Active Directory and LDAP? Don't worry, we’ll make it simple. These are just two among many methods that can provide secure user authentication and authorization. The information in this article will help you decide if LDAP or Active Directory is right for your organization. Robust security and a seamless user experience are attainable, and you can have both!
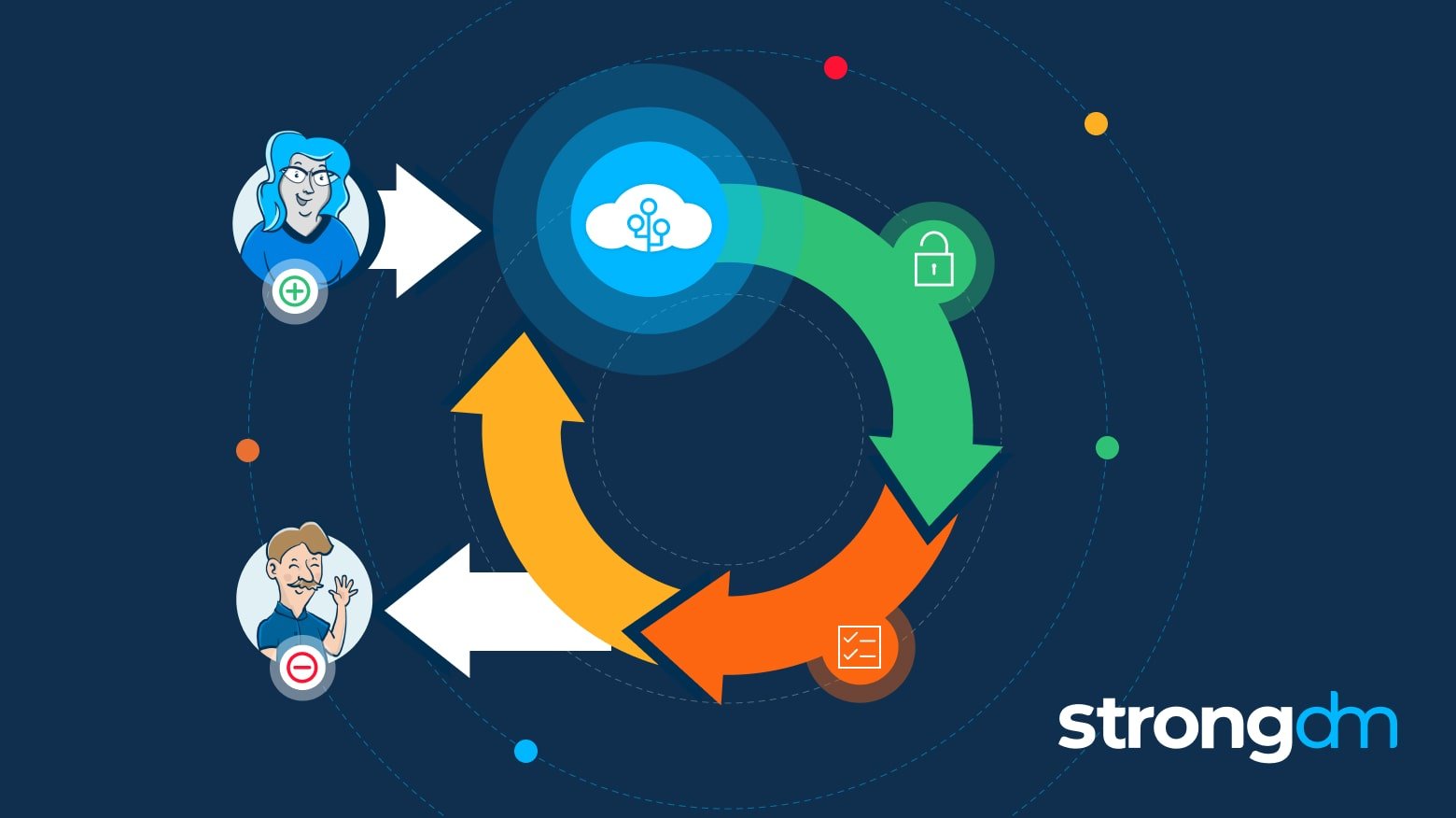
In this article, we will define SCIM and cover the basics of SCIM security. You’ll learn what SCIM stands for, how SCIM provisioning works, and why SCIM SSO is essential. By the end of this article, you will have a clear understanding of what SCIM means and how auto-provisioning via SCIM streamlines cloud identity management, increases employee productivity, and reduces IT costs.

