What Is SCIM Provisioning? How It Works, Benefits, and More

Written by
Schuyler BrownLast updated on:
June 25, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Summary: In this article, we will define SCIM and cover the basics of SCIM security. You’ll learn what SCIM stands for, how SCIM provisioning works, and why SCIM SSO is essential. By the end of this article, you will have a clear understanding of what SCIM means and how auto-provisioning via SCIM streamlines cloud identity management, increases employee productivity, and reduces IT costs.
What Is SCIM Provisioning?
System for Cross-domain Identity Management (SCIM) is an open standard that simplifies cloud identity management and allows user provisioning to be automated across multiple domains.
SCIM supports the exchange of user identity data between an enterprise identity provider (or an identity and access management system) and cloud service providers by providing an easy way to grant users access to cloud-based applications, while keeping sensitive data secure. It alleviates the burden of manual provisioning and gives employees a frustration-free user experience.
What is SCIM protocol?
The SCIM protocol is an application-level standard that enables secure management and exchange of identity data across domains. Based on JavaScript Object Notation (JSON) and Representational State Transfer (REST), the SCIM standard leverages REST APIs to facilitate the creation, modification, retrieval, and discovery of identity resources, including users and groups.
Importance of SCIM Provisioning
The recent and rapid adoption of cloud-based applications has made SCIM user provisioning a vital part of the identity management landscape. With the average enterprise using nearly 1,300 cloud services, companies need a secure, cost-effective way to automate provisioning and manage the user lifecycle in the cloud.
SCIM provides the scalability growing companies need. As organizations hire more employees and adopt more cloud-based applications, identity and access management becomes increasingly complex. Managing large numbers of accounts manually consumes valuable IT time, introduces errors, and impedes productivity. SCIM solves these problems and offers additional advantages.
Benefits of SCIM Provisioning
Perhaps the greatest benefit of SCIM is that it provides a standardized, secure methodology for exchanging information between IT systems. This ensures interoperability across domains without expensive custom integrations.
SCIM allows single sign-on (SSO), which increases security compliance and reduces the attack surface malicious actors could exploit. Automating individual users’ access and SCIM group provisioning significantly reduces manual efforts and mitigates the risk of human error and zombie accounts. A modern SCIM tool simplifies employee onboarding and offboarding and provides visibility into all IT infrastructure.
Finally, SCIM auto-provisioning increases productivity across the entire organization. Besides freeing up IT teams to focus on more valuable tasks, SCIM, in partnership with access management, reduces the time needed to grant access to backend infrastructure, giving employees a productivity boost. Together, these benefits improve the return on investment (ROI) on IT infrastructure and reduce the total cost of ownership (TCO).
🔥Hot Tip: The CISO at Better.com made automated provisioning much easier by implementing StrongDM, integrating automated access workflows into their current deployment and onboarding pipeline. “Before StrongDM, it would take up to a week to get someone provisioned. With StrongDM, we can now do that in minutes.” You can make your life easier too.
How Does SCIM Work?
SCIM defines a schema for representing user and group identities and provides a REST API for managing identity lifecycles. The API leverages common HTTP request methods (e.g., POST, GET, DELETE, etc.) to perform Create, Read, Update, and Delete (CRUD) operations on identities.
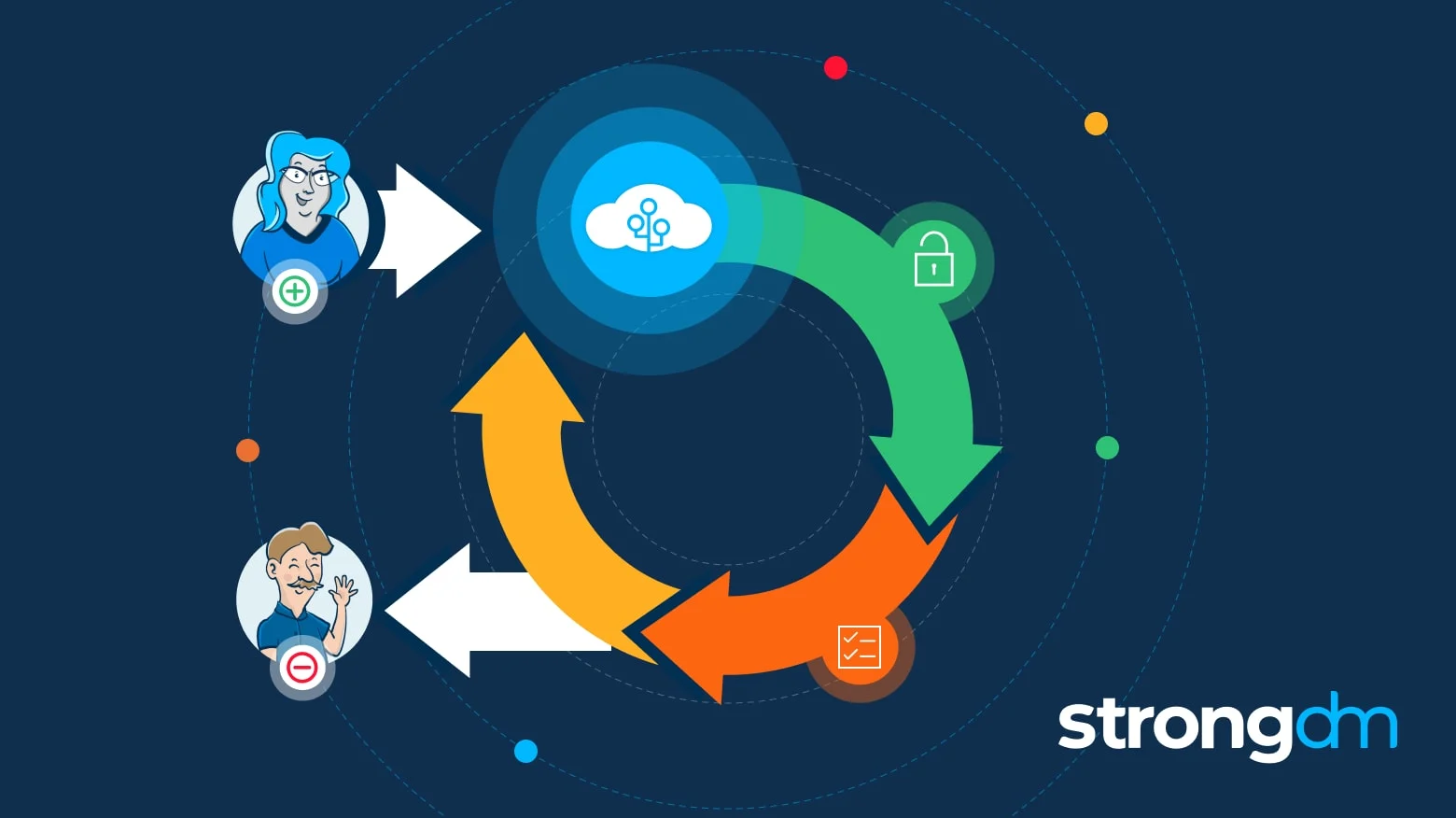
In SCIM, the “client” is the company’s IAM system or identity provider (SCIM IdP) and the “service provider” is typically a software-as-a-service (SaaS) application, such as Salesforce or Zoom. The client stores and manages the identities and permissions the service providers require. When an administrator creates, changes, or deletes an account on the client side, SCIM updates the service provider side automatically, keeping all systems in sync.
Defining core identity resources in a SCIM environment enables clients and service providers to communicate user identity data securely. Because SCIM supports interoperability across domains, it integrates seamlessly with cloud-based applications and works with other enterprise security tools, such as firewalls.
SCIM vs. SAML vs. SSO
SCIM vs. SAML
Security Assertion Markup Language (SAML) is an XML-based standard that enables authentication based on the user credentials stored in an enterprise identity and access management (IAM) system. While the global SAML market continues to grow and SAML provides an easy way to manage access to the resources an organization hosts, it is an ineffective system used on its own for cross-domain identity management
Organizations that use cloud-based solutions need a method for managing user access to resources in external providers’ domains. SCIM provisioning provides a way to automate access to all the applications and services an organization uses. Without SCIM, IT administrators would need to create and maintain external user accounts manually—a very complex and time-consuming task.
SCIM vs. SSO
Single sign-on (SSO) is an authentication method that enables users to access multiple applications using a single set of login credentials—typically, a username and password. It strengthens security and eliminates the need for users to remember a separate set of credentials for every application they access.
While SCIM and single sign-on (SSO) work together, each serves a different purpose. SCIM provides an easy way to provision users’ access across multiple domains, whereas SSO performs SCIM authentication by verifying users’ credentials.
How StrongDM Helps You Adopt SCIM Provisioning
StrongDM’s simplified SCIM auto-provisioning dramatically reduces the time needed to grant access requests, allowing employees to get into the resources they need more quickly. You can choose which users and groups you want your identity provider to manage, synchronize role-based access controls, manage policy exceptions, and more.
StrongDM integrates seamlessly with any SCIM-based directory service, such as Okta, Azure AD, or Google. Tighter SCIM integrations enable you to manage just-in-time, least-privilege access to critical infrastructure directly from your identity provider.
✨ Do It Now: Provisioning access between StrongDM and your IdP is super simple. See how it works to assign or adjust permissions for a specific user.
With StrongDM’s powerful set of attribute-based rules, you can grant access dynamically whenever a resource is spun up or spun down. Besides providing the flexibility needed in today’s ephemeral computing environments, rules eliminate costly manual administration and give organizations more granular control when provisioning infrastructure.
Save Time and Money by Simplifying Provisioning with StrongDM
StrongDM’s Zero Trust Privileged Access Management (PAM) platform gives security teams rigorous, precise control over systems access. With the ability to set conditional access based on any criteria or variables, companies can reduce the risk of data exposure and shrink the attack surface — all without sacrificing productivity and efficiency.
On top of that, StrongDM provides a single source of truth for cloud identity management, easing friction, streamlining user provisioning and deprovisioning SCIM tasks, reducing IT costs, and helping employees get access to the resources they need faster under a comprehensive Zero Trust security framework.
Want to experience frustration-free Zero Trust for yourself? Sign up for our free demo.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Schuyler Brown, Chairman of the Board, began working with startups as one of the first employees at Cross Commerce Media. Since then, he has worked at the venture capital firms DFJ Gotham and High Peaks Venture Partners. He is also the host of Founders@Fail and author of Inc.com's "Failing Forward" column, where he interviews veteran entrepreneurs about the bumps, bruises, and reality of life in the startup trenches. His leadership philosophy: be humble enough to realize you don’t know everything and curious enough to want to learn more. He holds a B.A. and M.B.A. from Columbia University. To contact Schuyler, visit him on LinkedIn.
You May Also Like




