Joiners, Movers, and Leavers (JML) Process (How to Secure It)

Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
People come, and people go, and while digital identities should cease to exist after a departure, many times, this doesn’t happen. At any given time, organizations can have thousands of user identities to manage and track, so when processes aren’t automated, it’s easy for many identities to fall through the cracks. This phenomenon is called Identity Lifecycle Management, and when it comes to access and security, it’s worth the time to get it right.
Identity lifecycle management is the process of managing user identities and access privileges for all members of an organization. It follows each user from onboarding to departure: Provisioning, updating, or revoking access to applications and resources as appropriate. Said another way, Identity Lifecycle Management manages the provisioning and deprovisioning of access with the flow of joiners, movers, and leavers.
What are Joiners, Movers, and Leavers (JML)?
- Joiners: A new employee joins the organization and needs to be onboarded.
- Movers: An employee receives a promotion, changes departments or teams, or moves across the organization due to restructuring.
- Leavers: An employee departs the organization and needs to be offboarded.
The JML Process Challenge
Inter-departmental cooperation between IT, HR, and Operations helps organizations stay on top of the Joiner, Mover, and Leaver cycle, but cooperation alone can’t solve the issue at scale. When organizations rely on manual processes, the processes can be prone to errors, potentially leading to privilege creep, dormant accounts, and breaches.
This is where automation and tooling come into play. While many identity providers have tackled this problem from an application perspective, easily managing it for infrastructure and back-end resources can still be a struggle. But it doesn’t have to be.
How to Automate the JML Process
StrongDM is a proxy that manages and audits access to databases, servers, clusters, and web apps. The platform reduces risk by combining the appropriate policies with an automated approach to access management to oversee Identity Lifecycles from joiners to movers and leavers.
With StrongDM’s powerful set of attribute-based rules, you can grant access dynamically whenever a resource is spun up or spun down. Besides providing the flexibility needed in today’s ephemeral computing environments, rules eliminate costly manual administration and give organizations more granular control when provisioning infrastructure.
Intrigued? Check out these videos to see StrongDM in action.
How To Link Okta Groups to StrongDM Using SCIM Provisioning:
How to provision StrongDM users, groups, and roles through Okta:
The Automated JML Process Examples
Let’s walk through an example of how companies can combine policy-based solutions with an IdP integration using StrongDM. We’ll name our fictitious employee Pamela. Pamela works for The Happy Place Company, a company that uses StrongDM to manage infrastructure access.
Joiners
Pamela joined The Happy Place Company in October 2022 as a DevOps Engineer. She is onboarded to the team. She needs to receive access to only what she needs. Using her IdP, Okta, Pamela is assigned a Group Assignment based on her role as a DevOps Engineer. The Okta Group then determines the infrastructure she has access to within StrongDM.

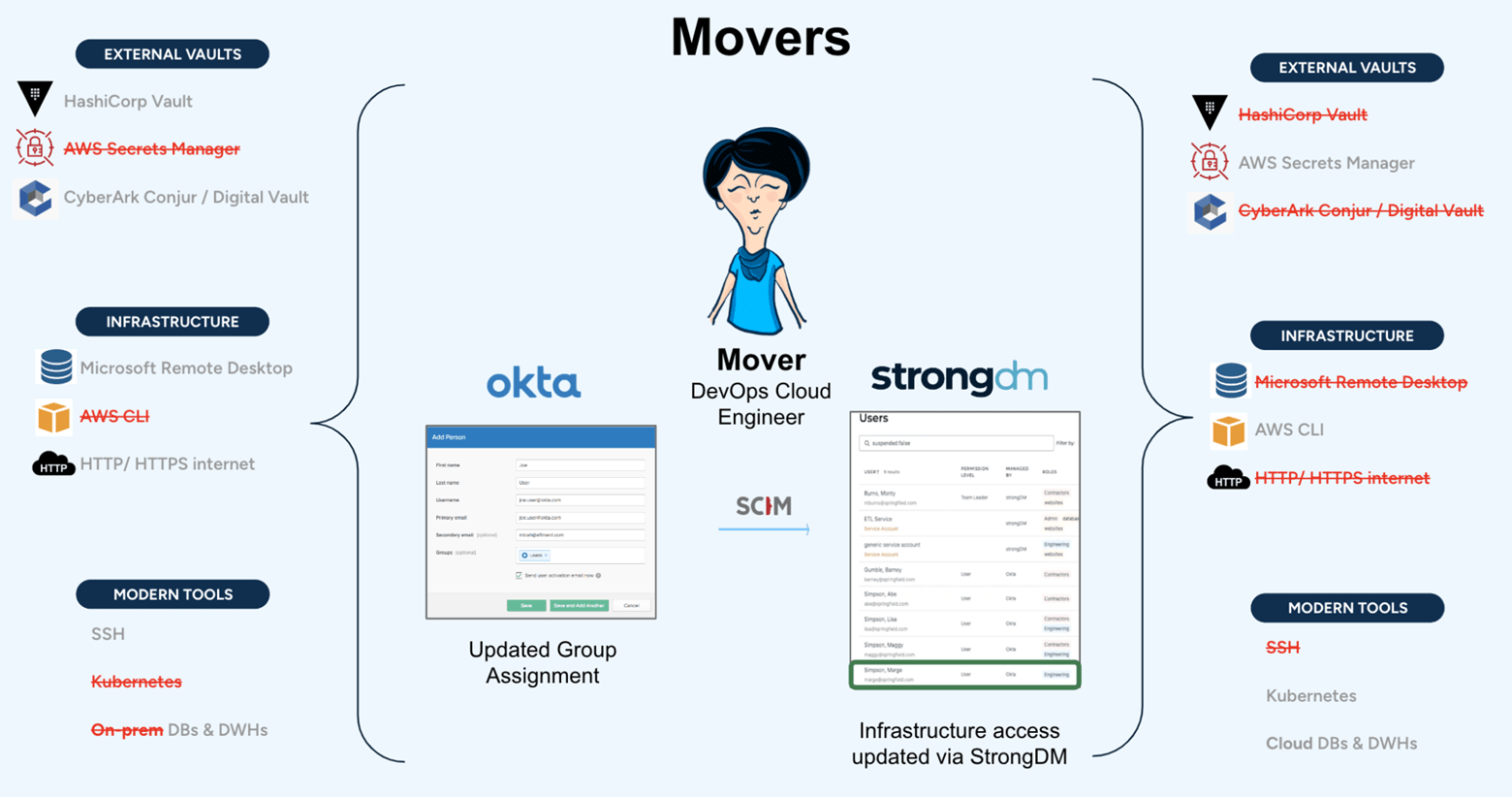
Movers
In September of 2023, Pamela realizes her passion for cloud engineering outweighs her fondness for her current role. She switches departments and joins a new team as a Cloud Engineer. When her role changes, so does her access. She no longer needs access to certain vaults, infrastructure, or tools, and she needs access to cloud resources.
Leavers
In January of 2025, Pamela is ready for her next adventure. She announces she is opening up her own business and sets her departure date. Now that Pamela is leaving The Happy Place Company, all of her access must be revoked at the end of her last day.

SCIM: How StrongDM and the IdP Work Together
SCIM supports the exchange of user identity data between an enterprise identity provider (or an identity and access management system) and cloud service providers by providing an easy way to grant users access to cloud-based applications while keeping sensitive data secure.
SCIM provides the scalability that growing companies need. As organizations hire more employees and adopt more cloud-based applications, identity and access management becomes increasingly complex. Managing large numbers of accounts manually consumes valuable IT time, introduces errors, and impedes productivity. SCIM solves these problems and offers additional advantages.
StrongDM’s simplified SCIM auto-provisioning dramatically reduces the time needed to grant access requests, allowing employees to get into the resources they need more quickly. You can choose which users and groups you want your identity provider to manage, synchronize role-based access controls, manage policy exceptions, and more.
StrongDM integrates seamlessly with any SCIM-based directory service, such as Okta, Microsoft Entra ID (fka Azure AD), or Google. Tighter SCIM integrations enable you to manage just-in-time, least-privilege access to critical infrastructure directly from your identity provider.
Frustration-free JML Processes with StrongDM
The StrongDM®’s Zero Trust Privileged Access Management (PAM) platform provides a single source of truth for cloud identity management. It eases friction, streamlines user provisioning and deprovisioning SCIM tasks, reduces IT costs, and helps employees get access to the resources they need faster—all without sacrificing security.
Want to experience frustration-free Joiner, Mover, and Leaver processes for yourself? Sign up for our free demo.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
Angela Donlan, Content Manager, Angela supports the marketing team by developing creative content that helps StrongDM tell its story in creative and authentic ways. Experienced in the advertising agency space and the consulting world, Angela spent her early career years serving as a client-facing writer and project manager for brands large and small. Her specialties range from brand development and strategic campaign planning to social media execution and long-form content production. Angela obtained her Bachelor of Science in Business Administration from the University of Tulsa. She majored in Marketing and Management and completed minors in Advertising and Communications during her time at TU. To contact Angela, visit her on LinkedIn.
You May Also Like




