
Written by
John MartinezLast updated on:
September 29, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Google Cloud Secret Manager is an intuitive platform for managing API keys, user passwords, digital certificates, and other sensitive data and administering access control policies for business resources. While cost-friendly and reliable for securing Google Cloud applications, you should look to other Google Cloud Secret Manager competitors if you manage complex infrastructure and need multiple integrations. In this article, we examine the top Google Cloud Secret Manager alternatives and each product's strengths and weaknesses.
Google Cloud Secret Manager Overview
Brief product summary
Google Cloud Secret Manager is an all-in-one lifecycle, secrets, and provisioning management system. It gives IT teams a single source of truth to administer, access, and audit secrets for Google Cloud applications and security tools.
Because it's a Google product, the interface shares a similar layout, color scheme, and navigation format—making it easy to learn and operate secrets data storage, logging, and analysis features.
Use cases
- Storing, encrypting, and accessing Google Cloud secrets, including API keys, passwords, and certificates.
- Automating security policy deployments such as secrets replication processes and least privilege access.
- Letting IT security teams centralize security operations control through integration with Google Cloud Identity & Access Management (IAM) system.
- Logging and auditing access activity, security controls, and potential security breaches within Google Cloud applications.
Pros
- Integration with existing Google products plus API connection options with third-party security and infrastructure systems.
- Easy-to-use system—it has that similar, friendly interface feel of other Google products.
- It's a relatively inexpensive tool, especially compared to other Google Cloud Secret Manager competitors.
Cons
- Restricted to managing secrets for Google Cloud apps only.
- Tough to gauge how users feel about the product—difficult to find online reviews as the product is relatively new.
1. StrongDM
Brief product summary
StrongDM is a Zero Trust PAM platform that removes operational silos between secrets and access management processes. The product supports various resource types, including servers, cloud services, databases, applications, and Kubernetes.
It also offers a broad range of integration capabilities, including other secrets management and IAM tools, so that enterprises can secure access across their entire technology stack in a centralized control system.
Use cases
- Centralizing security operations management—extensive integrations with third-party IAM, single sign-on (SSO), secrets management, directory service, and authentication tools let teams run everything from one interface.
- Streamlining user access and privilege management—the automation helps teams quickly onboard and offboard users and administer just-in-time, least privilege, and temporary resource access.
- Simplifying those tedious audits—the extensive observability, logging, and reporting capabilities help make compliance management a breeze.
Pros
- Security features ensure that credentials and keys always remain hidden from the end user.
- Seamless deployment across infrastructure does not affect current data workflows and can standardize across any database or server type.
- Transparent and straightforward pricing model means no surprise fees.
- Extensive use of access control automation allows IT, DevOps, and security teams to focus time and effort on other projects and operational needs.
Cons
- Requires continual access to StrongDM API for access to managed resources.
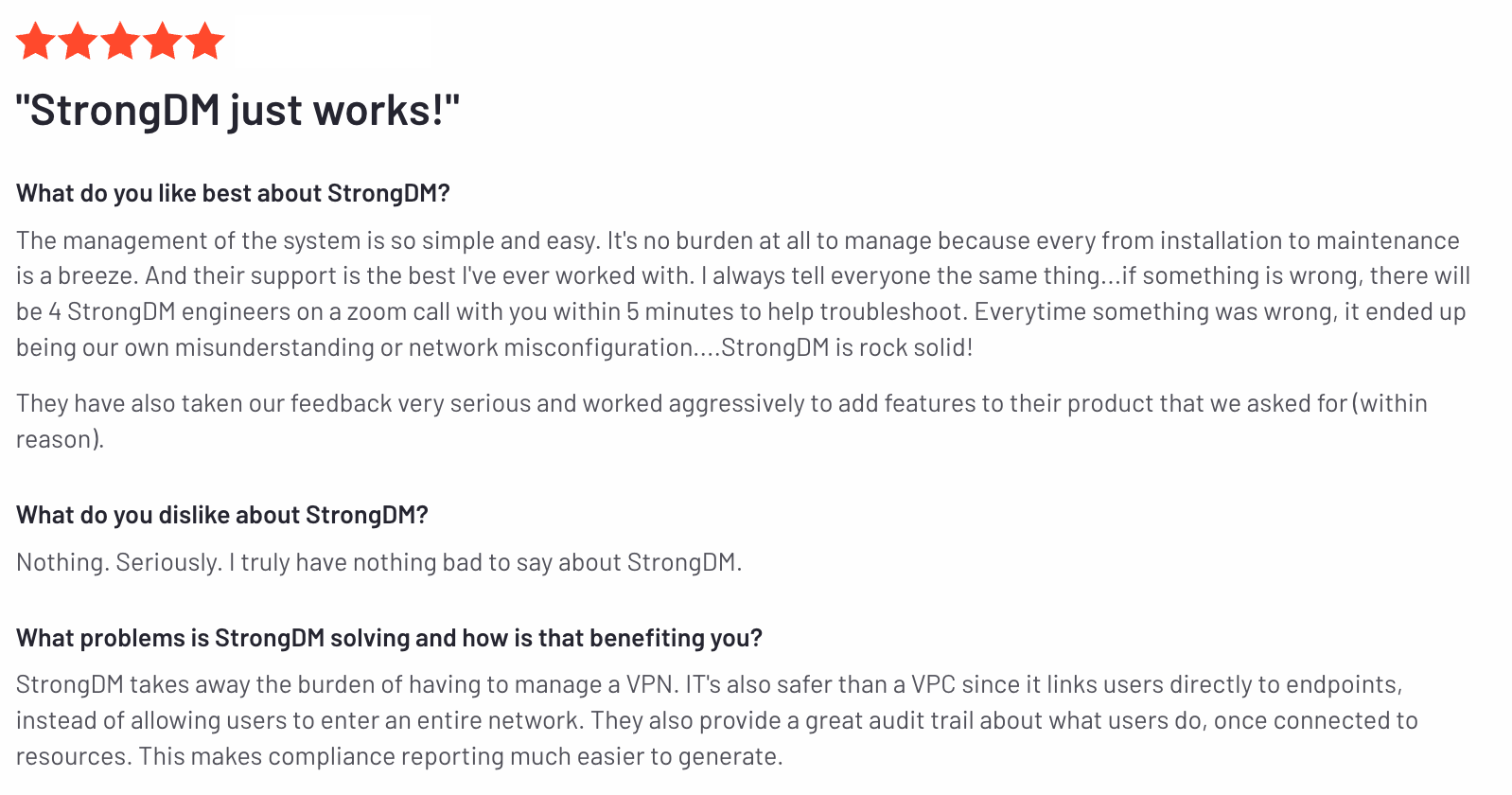
StrongDM’s G2 Reviews
- 4.8 / 5 stars
Read all of StrongDM’s G2 reviews here.
Pricing Information
StrongDM offers simple pricing, including support for all resource types.
Users have the option to sign up for a free 14-day trial.
2. AWS Secrets Manager
Brief product summary
AWS Secrets Manager is one of the best Google Cloud Secret Manager alternatives that can match its pricepoint and feature usability. It's particularly handy for government contractors and businesses under a major compliance umbrella, as the cloud security controls meet most regulatory requirements.
Equipped with robust security capabilities, AWS Secrets Manager helps teams ensure their credentials, API keys, and token data get securely stored, rotated, and replicated as needed.
Use cases
- Managing secure secrets—user credentials, API keys, and tokens are securely stored to access for day-to-day use and replicate for disaster recovery or secret redundancy procedures.
- Ensuring lifecycle tasks don't slip through the cracks—users can automate credential rotation processes for databases, clusters, and applications.
- Overseeing security operations for AWS services—teams can control IAM processes and monitor activity and logs to secure the AWS ecosystem and simplify compliance audits.
Pros
- Uses a pay-as-you-go system that lets companies grow as their capacity requirements for credential storage and API calls increase.
- Users can automate repetitive tasks like credential rotation without code deployment requirements.
Cons
- Users want better product support—tough to get quality service unless enrolled in the enterprise support plan.
3. Azure Key Vault
Brief product summary
Microsoft Azure Key Vault gives organizations a secure solution to store tokens, user credentials, and API keys. IT teams can also use the platform to manage life cycles for encryption keys and transport layer security/secure sockets layer (TLS/SSL) certificates.
Run in the Azure cloud, Key Vault, by default, supports numerous cloud compliance requirements—even meeting the NIST Federal Information Processing Standards (FIPS) through its use of hardware security modules (HSMs) for secrets storage.
Use cases
- Providing a central source to store and retrieve user credentials, tokens, certificates, and API and cryptographic keys for secure access to cloud services.
- Freeing up IT resources and personnel for other projects by letting users automate secrets management activities like enrollments, renewals, replications, and segregation.
- Simplifying compliance management and processes of securely scaling network IT resources.
Pros
- Users find it easy to navigate the graphical unit interface (GUI) and integrate it with Azure security tools and applications.
- Offers many third-party options to supplement any secrets management features missing from the product.
Cons
- Users want to see improved integrations with other cloud providers and key management capabilities extend to other endpoints like mobile devices.
- Latency issues are common for retrieving and authenticating keys and for API responses.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like



