Identity and Access Management (IAM) Best Practices

Written by
John MartinezLast updated on:
October 17, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Identity and Access Management (IAM) has become an essential element of security plans for many organizations. To reap the most security benefits, it is imperative that companies ensure that their IAM tools and processes are set up correctly. In this article, we will share 11 identity and access management best practices your company should adopt to establish a strong security posture. By the end of this article, you’ll know the next steps to take to incorporate IAM best practices into your security strategy.
1. Adopt a Zero Trust Approach to SecurityMany companies have applications, platforms, and tools that are designed with implicit trust features. Implicit trust means that if users have access to your network or log in to a tool, the system “remembers” them and doesn’t always prompt the user to verify their identity again. These lax access permissions can pose a major risk to your organization’s security stance if an unauthorized entity gains access to your system via a remembered credential.
A Zero Trust security model relies on these core principles: never trust, always verify; assume breach; and apply least-privileged access. By adopting a Zero Trust model and services that work with IAM, companies can always guarantee users are who they claim to be before allowing access to company resources. This constant authentication supports IAM best practices by reducing the risk of unintentionally allowing access to unauthorized users.

IAM tools and a Zero Trust strategy work well together because Zero Trust architecture ensures your IAM policies and procedures are followed whenever and wherever a user needs access by employing hybrid identity and access management best practices. Zero Trust’s foundational rule of applying least-privileged access helps define access policies, while IAM tools simplify and streamline the authentication process to allow the right level of access without interrupting workflows.
A StrongDM study showed that, on average, 85% of credentials had not been used in the last 90 days. And all of those credentials represent an attack vector for bad actors. Least privilege access is best applied through just-in-time (JIT) access workflows. This means that standing access is eliminated, and access is only granted when it is needed.
⚠️ Caution: Traditional Privileged Access Management (PAM) deployments have gaps. Shifting away from PAM solutions to Zero Trust Privileged Access Management (PAM) solution like StrongDM strengthens your security posture through continuous verification and validation of identity, right-to-access, and observability. Learn how to protect your databases, the cloud, Kubernetes, and more with our legacy PAM augmentation guide.
2. Identify and Protect High-Value Data
Protecting your most valuable data starts by limiting who can access it as much as possible—but, to limit access, you first need to know where your most valuable data is stored and how it is used.
Companies identify high-value assets (HVAs) — including data and the systems that house them — based on what data would pose the biggest threat to the organization if it was lost or compromised. This often includes sensitive data like confidential trade secrets or customer and employee PII. Once you’ve identified your high-value data, it’s important to see where it’s stored and what applications and tools have access to that data. These HVAs are often stored in the cloud, so it’s critical to Azure, GCP, and AWS IAM best practices to keep your data secure.
From there, use access control best practices and policies to limit access to that data and deprovision access from users who don’t need that data to do their daily work.
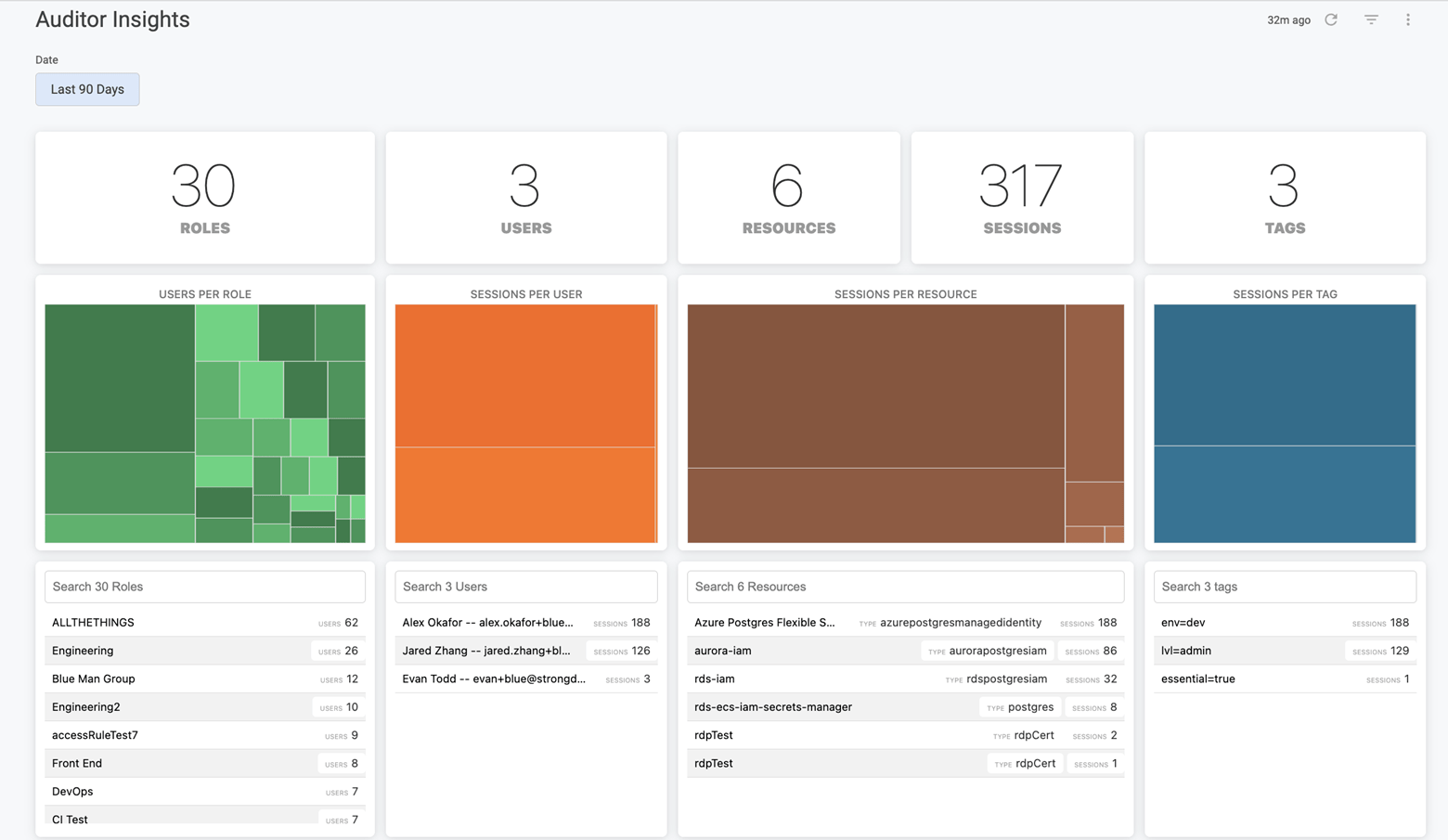
✅ Checkpoint: Make sure your IAM solution offers detailed reports that include:
- access grants
- unused permissions
- user history down to the keystroke
StrongDM offers this kind of reporting so you can automate revocation and continuously monitor access. Combine actionable insights with powerful workflows to reduce your access risk without breaking a sweat.
3. Enforce a Strong Password Policy
Your IAM technologies are only as strong as the identity management best practices and policies that support them. If your team is leveraging single sign-on (SSO) tools, it’s critical that each user’s password is strong, unique, and difficult to guess to support password and IAM best practices. Passwords must be complex enough to deter cyberattacks, frequently changed, and not used for multiple sign-on requirements.
Even if your company uses Multi-Factor Authentication (MFA) alongside SSO tools, that doesn’t mean you can overlook password policies and assume your resources are protected. Instead, set up an audit schedule to regularly review user password strength and continuously make users change their passwords.
🚀 Take it a Step Further: Tighten security and password protocols with StrongDM’s advanced features:
- Rich integrations with SSO ensure that authentication is synced with access
- Keys and credentials are backed up and never exposed to end users
- Integrates with third-party vaults in a centralized platform
4. Use Multi-Factor Authentication (MFA)
User authentication is an essential component of effective identity and access management best practices. After all, if you can’t guarantee a user is who they claim to be, you may be putting your data at risk and unintentionally allowing access to an unauthorized user. This is crucial for advanced types of attacks like synthetic identity fraud, where the hacker has access to primary identifiable information like a person's name or address.
Login credentials alone aren't enough to validate a user’s identity; companies need an additional step to ensure the person logging in with those credentials is the authorized user. MFA tools simplify and automate the authentication process by requiring two or more forms of validation to confirm a user’s identity.
MFA tools often use a combination of these methods to authenticate identity:
- Biometric authentication (e.g., fingerprints or facial recognition)
- Possession authentication (e.g., sending a one-time password to a user’s personal device)
- Knowledge authentication (e.g., answering security questions)
- User location or time data
5. Automate Workflows
IAM tools offer IT teams many opportunities to use automation to make your organization more secure. Automation reduces manual errors, streamlines workflows, and supports compliance and governance needs.
Common tasks like creating accounts, changing passwords, and provisioning or deprovisioning access for personnel changes can easily be automated with IAM technology. These automations support best practices for access control, helping the company stay protected against insider threats when employees leave while also simplifying the transition for new employees or those transitioning into a new role.
Automation also makes it easy to log, audit, and generate reports on a regular schedule for compliance requirements. This eliminates one of the most manual tasks many IT departments commonly deal with.
Get Started: Take a look at our quick overview of how to automate database access management.
Ultimately, automation helps companies cut down on help desk requests, save time and money, and better leverage the capabilities of their IAM tools.
6. Adopt The Principle of Least Privilege
One of the most common roles and permissions best practices is applying the principle of least privilege. IAM least privilege encourages organizations to restrict access and permissions as much as possible, without interfering with users' daily workflows.
Role management best practices should be used to define the minimum amount of privilege users in each role need to perform their work. In addition to this role-based access control, organizations can also leverage attribute-based access control to further define the permissions necessary across different departments. However, the goal is to regularly audit usage, reduce unnecessary standing permissions, and grant system function permissions to limit capabilities wherever possible.
It’s especially important to limit administrative and change capabilities to ensure single admins don’t have excessive permissions they don’t need. Divide responsibilities to avoid over-provisioning access to certain people and adopt privileged access management best practices (PAM).
7. Enforce Just-in-Time Access Where Appropriate
In some circumstances, the principle of least privilege doesn’t provide the necessary flexibility that certain situations require. For instance, a help desk associate may need temporary elevation of privileges to troubleshoot a customer’s urgent ticket. One way to enforce identity and access management best practices, yet still support the principle of least privilege without compromising user experience, is by leveraging just-in-time access.
Time-limited access makes it easy to elevate permissions temporarily, without giving excessive authority or access to a user who may not need it regularly. These granular permissions are available with disposable or one-time-use credentials, allowing sufficient access without altering your overarching user access provisioning best practices and policies. The temporary access method is especially valuable for users outside your organization who may require periodic access to a system, like vendors or partners.
8. Leverage Both Role-Based Access Control and Attribute-Based Access Control Policies
Using role-based access control (RBAC) and attribute-based access control (ABAC) together can facilitate robust user access management best practices.
RBAC determines access based on a user’s role, giving the same access to everyone called a “third-party vendor,” “administrator,” or “manager” based on their title. This ensures that users have the minimum privileges necessary to perform their work depending on their level. But, using RBAC alone often requires IT teams to do more manual provisioning to provide access to additional tools beyond the fundamentals, which can get challenging as a company’s tech stack expands.
ABAC uses policies to define access based on filters and attributes assigned to users. For example, every employee in the marketing department may need access to a project management tool that employees in other departments don’t. However, using ABAC exclusively can be unnecessarily complex when creating too many attributes to define users.
Combining RBAC and ABAC can help automate provisioning and deprovisioning as users join the company, leave the organization, or change roles. Setting up these access control policies is an essential element of IAM implementation best practices.
9. Regularly Audit Access to Resources
Even with strong policies around access control, over-provisioning remains a problem for many organizations. Auditing is one of the fundamental IAM best practices to build into your overall IAM strategy to maintain the principle of least privilege.
Organizations are constantly adding new tools and applications to their tech stack, and employees may believe they need access to all these tools to perform their work. However, as teams streamline their workflows using those tools, IT commonly finds orphaned accounts that employees aren’t using. By auditing usage logs and access permissions regularly, IT teams can deprovision access and reduce their attack surface.
Limiting access is part of IAM security best practices, but the only way to consistently track what access users really need is through regular audits.
💡 Pro Tip: Create an auditing schedule in your IAM strategy to make sure your team prioritizes this important security procedure. Stay on top of the schedule by adopting a solution that speeds the pace of audits and allows you to conduct them quarterly rather than yearly.
10. Centralize Log Collection
Many IAM tools automatically generate logs, and these logs are valuable tools to help your team meet compliance requirements, audit usage, and strengthen IAM policies. However, not all teams think to centralize where they store their logs.
Rather than pulling logs from multiple locations, many companies store logs on the cloud for easy reference. In an increasingly hybrid work environment, storing logs on the cloud instead of on-premises is often a more convenient and affordable way to keep logs available and accessible. But, when centralizing log collection, companies must consider current cloud IAM best practices to keep valuable log data secure without limiting accessibility.
💡 Pro Tip: With StrongDM, you can stream your audit logs to a third-party object storage service, such as Amazon S3 or export to your preferred security information and event management SIEM/SOAR tool. When your logs are streamed to an external storage location for ingestion into SIEM applications, you gain additional insights and visibility into compliance, security, and other teams.
11. Adopt IAM Solutions That Work With Existing Tools
Using the right tools can make applying identity and access management industry best practices much easier for your organization. There’s no need to force a round peg into a square hole; instead of making IAM solutions fit your existing tech stack, search for the right solutions that already support your existing tools and applications.
Some tools may need to be reconfigured to support IAM technology. However, IAM implementation best practices recommend that you limit how many reconfiguration projects need to be done to integrate IAM technology. Even as you search for the right tools to support your tech stack, you can start identifying and adopting user account management best practices for your organization long before you have the tools to automate it. Defining those policies early will make it easier to set up your IAM framework and systems later.
Make IAM Best Practices Standard in Your Organization
The identity and access management industry is always evolving, but there are some fundamental IAM best practices that can support your organization as your IAM strategy grows. These best practices are great ways to help you build out your IAM framework and further strengthen your security posture.
If you’re wondering how to start implementing IAM within your organization, our IAM guide offers valuable information to help you get started. StrongDM can also help your organization start implementing identity and access management right away with our comprehensive Infrastructure Access Platform.
Want to see how StrongDM takes the guesswork out of your IAM implementation? Contact one of our experts today for a free no-BS demo.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like