Evolving From Identity-Based Access to Dynamic Access Management (DAM)


Written by
Angela DonlanLast updated on:
September 15, 2023Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
You’ve already taken the first step. You’ve decided to take an identity-based approach to your teams. But what comes next? Using that foundation to adopt Just-in-Time (JIT) access and Zero Standing Privileges (ZSP) ultimately enables you to manage access dynamically.
This article is your map for taking the work you’ve done with identity and your identity provider (IdP) and using it as your launchpad for access management. Shifting from identity-based access to a more dynamic access approach is necessary for organizations looking to modernize their access management and better protect sensitive resources at scale and in the cloud.
Identity-Based Access: The Starting Point for Modern Access
The advantages of an identity-based approach over a perimeter-focused approach are clear. When you standardize access controls based on the individuals, your security posture gains increased visibility, granular controls, and centralized management.
Adopting an identity-based access approach and enlisting an IdP is the foundation for modern access management, but it’s also just that–the foundation. It’s basecamp. Identity-based access is the beginning, and there’s more ground to cover on the path to a mature access management strategy. So if identity-based access is the first step in the journey, what is the ultimate goal? And why should IAM teams and IT leaders prioritize reaching the goal? We’ll show you. We even have a map for that.
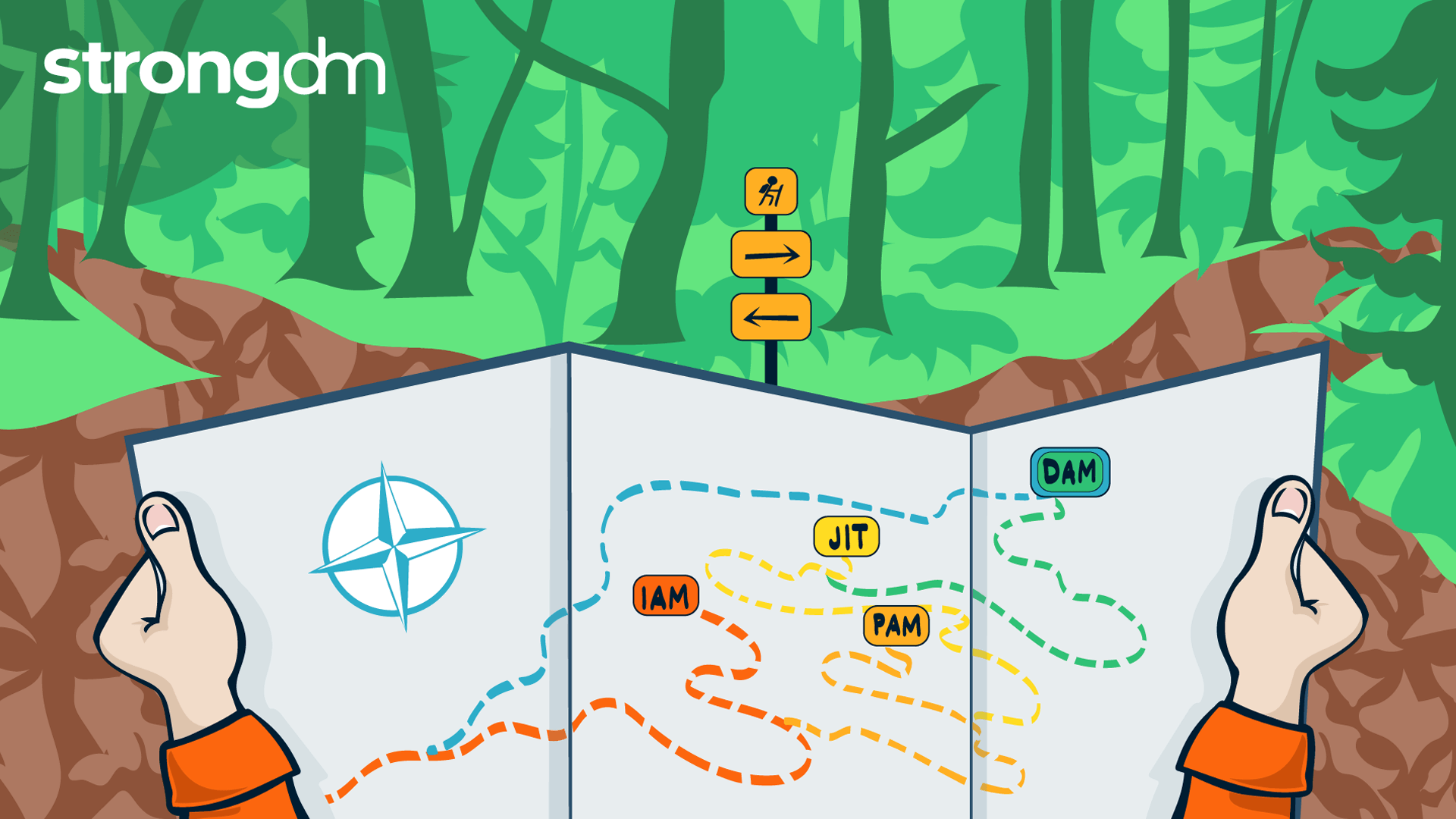
Getting to Dynamic Access Management (DAM)
The main goal of modern access management is to create access rights that ONLY exist in the moments they are needed. In those moments of need, that access must also be secure and auditable—complete with detailed logs of all user activities to meet regulatory compliance requirements, detect suspicious behavior, and conduct effective post-incident investigations. That’s how you turn managing access from burdensome overhead to a system that reduces the attack surface and minimizes risk.
This approach to access management is called Dynamic Access Management (DAM). In this approach, standing permissions are eliminated and replaced with Just-in-Time (JIT) access. DAM enables every technical user to get in, get out, and get on with the next strategic initiative—without loitering or unsanctioned exploration. This marriage of Just-In-Time Access and visibility into the actions and activities for investigations, auditing, and compliance differentiates the DAM approach from the identity-based access approach.
For example, embracing DAM empowers organizations to…
-
Enable Zero-Standing Privileges
When access expires or is bound by time, the risk of misuse decreases significantly. Not every individual needs full access all the time, either. ZSP is especially useful for contractors and third-party vendors.
-
Protect Access Across your Entire Stack
Secure your entire stack. Especially those areas that are gaps for traditional PAM, like databases, Kubernetes clusters, containers, and almost everything in the cloud.
-
Simplify Compliance with Granular Auditing
See who did what and when and record it. Quickly answer auditor questions about who had access to what and what they were doing in the system. Granular auditing separates PAM platforms from DAM platforms.
-
Gain Visibility into Access with Advanced Insights and Analytics
Understand how access is used and which tools are not being accessed and used over time. Advanced Insights and Analytics enables you to revoke access where needed and decide which resources should exist based on usage.
-
Secure Identities Across the Entire Lifecycle
Protect the entire lifecycle of the identity. People change and leave over time with an organization; their access must change with them. Correct access is provisioned when new identities join and when they are promoted or change roles over time. Similarly, access is de-provisioned when they change positions and is deactivated when they leave the organization.
Identity-based access is part of the journey. Dynamic Access Management (DAM) is the destination. DAM is also the identity pillar for Zero Trust, but that’s a topic for another blog.
Curious how your organization can reach the access management promised land? Chat with one of our friendly guides today.
How StrongDM Can Help
StrongDM can help you along your access management journey, ultimately getting you to Dynamic Access Management (DAM). By integrating with your existing identity-based approach, StrongDM can deliver dynamic access for every technical user on your team.
Want to see it in action? Book a demo.
Happy trails! 🏕️
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
Angela Donlan, Content Manager, Angela supports the marketing team by developing creative content that helps StrongDM tell its story in creative and authentic ways. Experienced in the advertising agency space and the consulting world, Angela spent her early career years serving as a client-facing writer and project manager for brands large and small. Her specialties range from brand development and strategic campaign planning to social media execution and long-form content production. Angela obtained her Bachelor of Science in Business Administration from the University of Tulsa. She majored in Marketing and Management and completed minors in Advertising and Communications during her time at TU. To contact Angela, visit her on LinkedIn.
You May Also Like