5 Reasons to Level Up From Identity to Dynamic Access Management

Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Historically, finding an infrastructure access management solution that is secure while still being easy to use has been extremely difficult. Too often, ease of use and complexity end up at odds. StrongDM addresses this challenge–and does so by integrating with your existing identity-based security initiatives.
This blog details how StrongDM enables organizations to level up their access management approach to meet the requirements of Zero Trust Privileged Access Management (PAM), bolster security, and streamline operations.
Embracing Zero Trust PAM empowers organizations to:
☑ Enable Zero-Standing Privileges (ZSP)
☑ Protect Access Across your Entire Tech Stack
☑ Meet Compliance with Granular Auditing
☑ Gain Full Visibility into Access with Advanced Insights and Analytics
☑ Secure Identities Across the Entire Lifecycle
Why level up to Zero Trust PAM?
Leveling up to Zero Trust PAM enables you to activate Zero-Standing Privileges (ZSP), protect access across the entire backend stack, conduct granular audits for compliance, take action with custom insights, and safeguard access throughout the entire identity lifecycle.
1) Enable Zero-Standing Privileges (ZSP)
The ZSP methodology eliminates standing credentials. Removing standing credentials means no one in your organization has standing or long-term access to resources. Instead, organizations utilize Just-in-Time access to provision and deprovision access to sensitive resources.
StrongDM Delivers ZSP through Just-in-Time Access
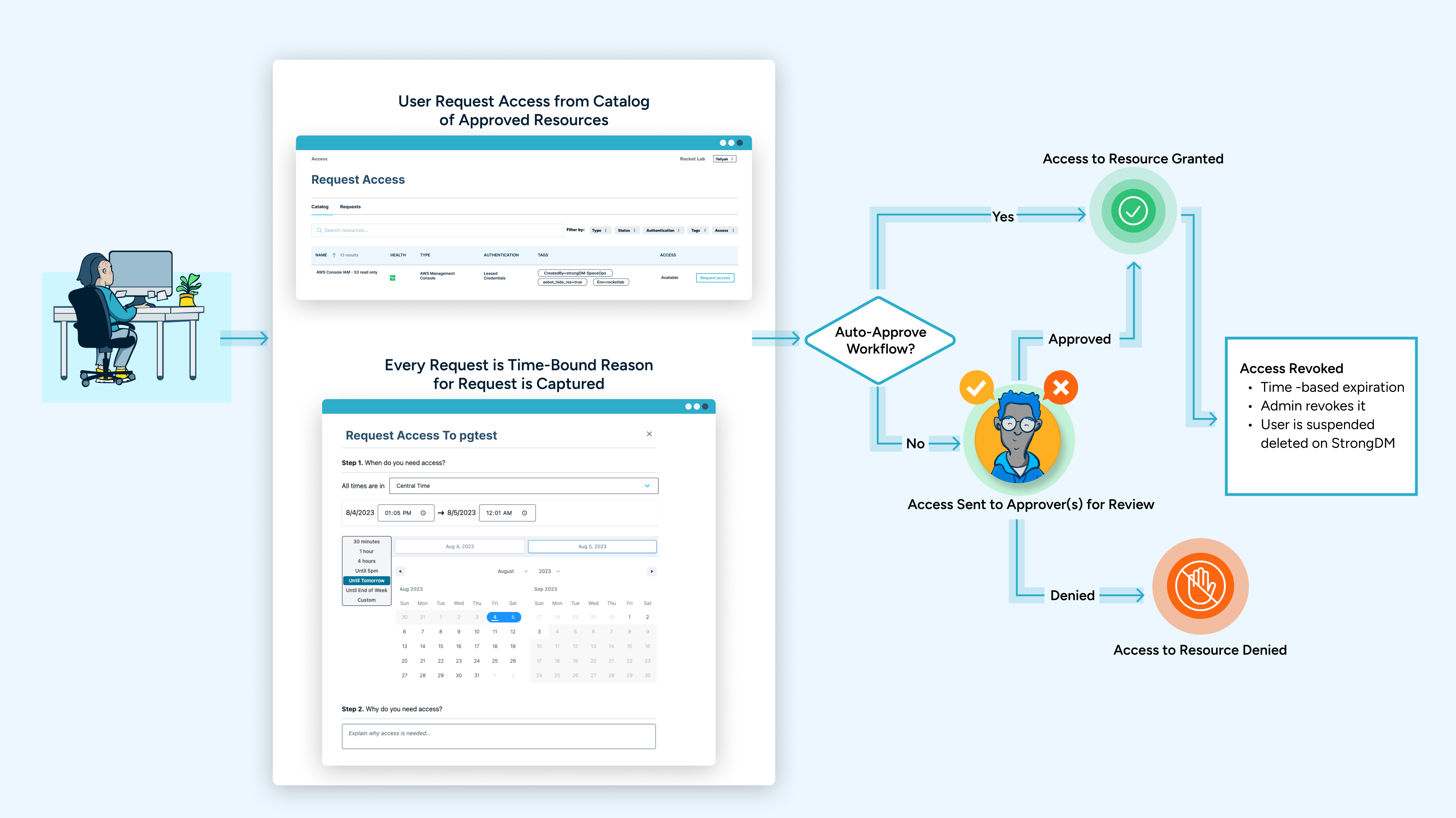
StrongDM enables Just-in-Time Access because it can provision access to virtually any resource when it's needed. From there, users request access and connect based on human or automated approvals. Admins can more easily manage access requests and approvals while end users get access to what they need when they need it.
Want to have an individualized Access Catalog or a directory of available resources based on role or resource attributes (i.e., environment tags, geolocation, etc.)? Check out Access Workflows. Access Workflows supports multi-step processes and change management while also enabling out-of-the-box integrations with ticketing and ChatOps tools, like JIRA and Slack.
Access Workflows in Action
2) Protect Access Across your Entire Stack
Keeping everything straight in today’s infrastructure is a challenge, whether on-premises, hybrid, or in a cloud environment. The surge of modern resources creates a conflict between security and productivity, making infrastructure access a point of contention between those who safeguard resources and those who need access to perform their jobs.
StrongDM Masters the Limitless Stack
Unlike traditional PAM tools, StrongDM works with your entire tech stack and supports native integrations that enhance current investments and future-proof your business. These integrations include support for cloud environments like AWS, Google Cloud, and Microsoft Azure; common protocols like SSH and RDP; and newer tools like cloud-managed databases, Kubernetes, and containers. Organizations use StrongDM to manage privileged access across all their IT infrastructure, regardless of where the resources live.
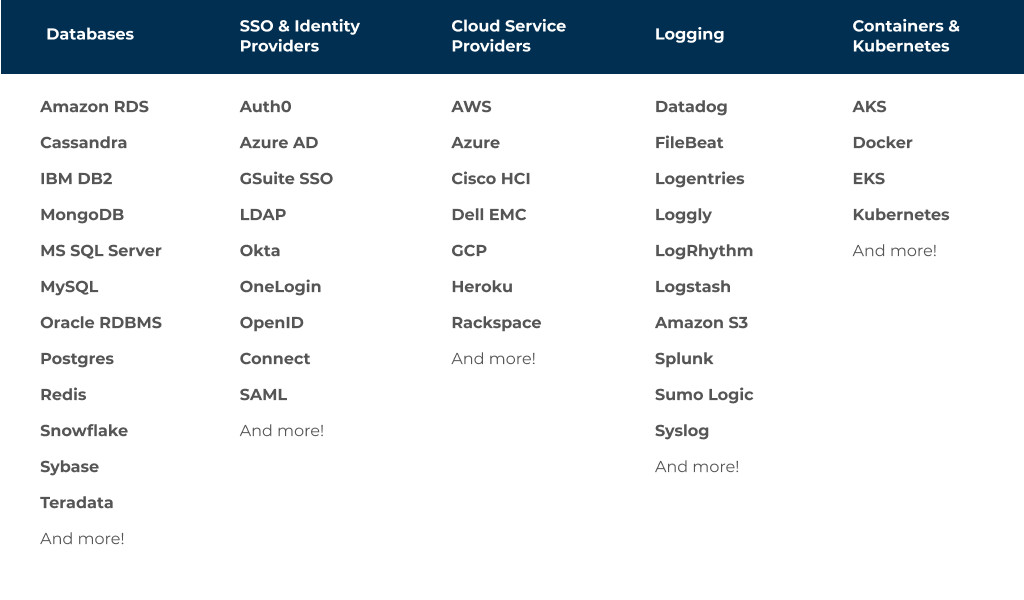
There’s more. We <3 your stack—StrongDM.com/connect.
3) Simplify Compliance with Granular Auditing
Truly dynamic access combines easy auditing capabilities with total visibility into every action–for every team member. Because delivering a clear picture of access risk is much simpler with full visibility into your resources—especially when they span your entire infrastructure.
StrongDM Unlocks Comprehensive Auditing & Audit History
Administrators use StrongDM to review various data points as they exist currently or at any moment in the past. Admins can also export this history in several formats, including JSON and CSV, to easily provide evidence to auditors or to feed to internal tooling. Oh yeah, and those logs integrate with SIEM and SOAR tools seamlessly. And all of that brings us to…
4) Gain Full Visibility into Access with Insights and Analytics
Identifying tools and systems that are NOT accessed and used over time can be just as valuable as understanding the resources employees use daily. A recent survey proved that 85% of privileged credentials are NOT used on a quarterly basis—not once! When privileged credentials exist in perpetuity, so does risk.
StrongDM Reduces Risk and Boosts Productivity with Security Metrics
Unique to StrongDM, Advanced Insights enable administrators to revoke unused privileges and decide which resources should exist based on usage.
Advanced Insights
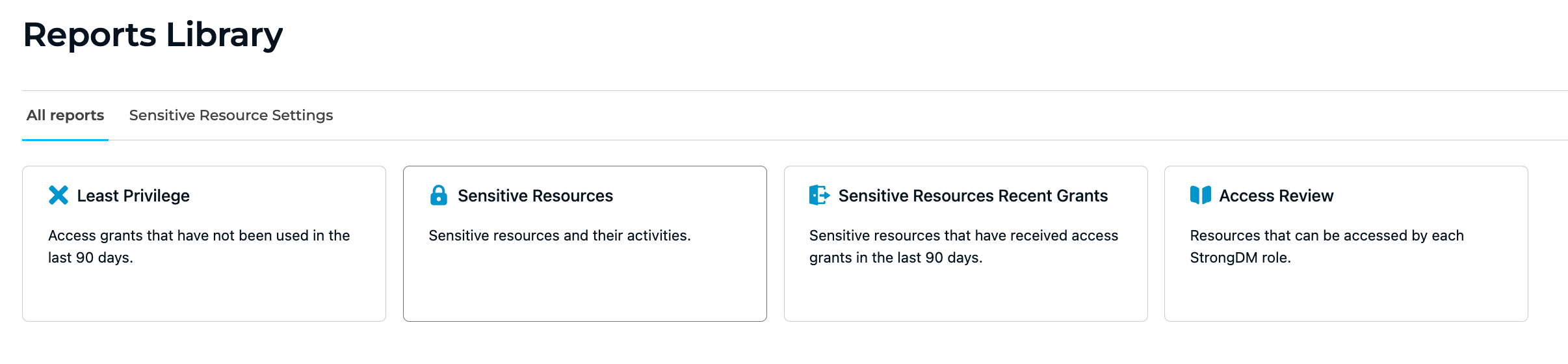
Advanced Insights allows admins to export audit logs into an organization’s security or data analytics tool of choice in a usable and parsable way. These insights help organizations answer common user queries regarding infrastructure access for audits, investigation, and compliance use cases via the StrongDM Reports Library.
The Reports Library
This library gives a complete view of resources and roles that are over-privileged and underutilized, as well as reports on resource grants to sensitive resources in an easy and automated way across the entire infrastructure.
Answer Questions Fast and Make Updates Even Faster
Each report within Advanced Insights will allow you to answer critical questions to prove you are enforcing security best practices across the entire backend tech stack. Here are some of the most-used reports leaders can pull:
- Least-Privilege Report: Get visibility into standing permissions that have NOT been accessed in the past 90 days.
- Sensitive Access Grants: Monitor whenever admins approve access to your most sensitive resources.
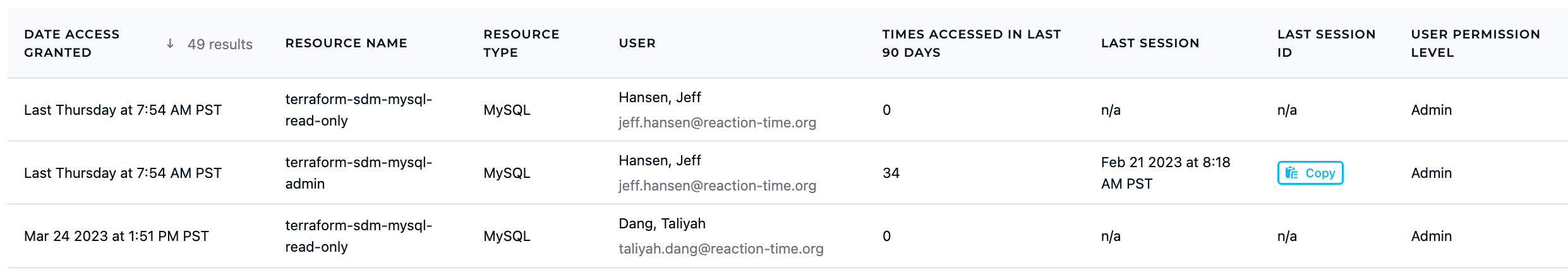
- Sensitive Resources Recent Grants: View the actual contents of every session, including the queries or commands executed, to assess whether anything suspicious occurred.
- Access Review: Understand roles and their assigned resources to see if specific resources are actually in use by those roles.
5) Secure Identities Across the Entire Lifecycle
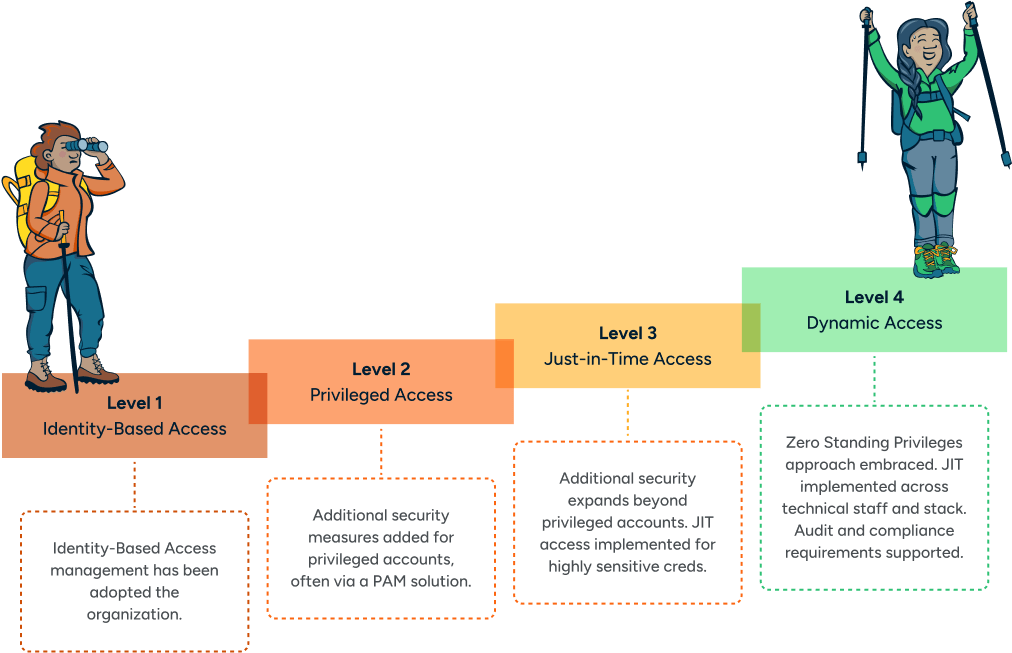
How an organization addresses access lifecycles varies depending on where they land on the Secure Access Maturity Model. Levels 1 and 2 (Identity-Based Access and Privileged Access) of the model use an “Always-On” approach to credentials within the access lifecycle. With always-on access, the credentials for each identity live on until they are retired. Level 3 is somewhat more secure with a combination of always-on access and Just-in-Time access. Only Level 4, Dynamic Access Management, fully eliminates always-on access. Eliminating always-on access means credentials only exist temporarily, users cannot see credentials, and admins can track system activity closely.
StrongDM Enables Just-Right Access For Every User: From Day 1 to their Last Day (and Everyday Inbetween)
People move throughout organizations over time. Their journey is dynamic and fluid—their access must be, too. It’s deeper than just provisioning and deprovisioning access upon arrival and departure. As the individual rotates through new roles or departments, their access must change with them over time. Admins use StrongDM to adjust access dynamically to support those changes.
Leveraging StrongDM to Enable Zero Trust PAM
The transition from Identity-Based Access to Zero Trust PAM is a significant leap toward a more secure and efficient access management strategy. StrongDM is a trustworthy partner in this journey, integrating seamlessly with existing identity-based approaches to deliver dynamic access, granular auditing, comprehensive protection, and identity lifecycle management.
By embracing StrongDM, organizations can realize the benefits of DAM and strengthen their security posture while optimizing operations. We’re ready to guide you toward the ultimate destination: Dynamic Access Management. Are you ready for it? Book a demo.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
Angela Donlan, Content Manager, Angela supports the marketing team by developing creative content that helps StrongDM tell its story in creative and authentic ways. Experienced in the advertising agency space and the consulting world, Angela spent her early career years serving as a client-facing writer and project manager for brands large and small. Her specialties range from brand development and strategic campaign planning to social media execution and long-form content production. Angela obtained her Bachelor of Science in Business Administration from the University of Tulsa. She majored in Marketing and Management and completed minors in Advertising and Communications during her time at TU. To contact Angela, visit her on LinkedIn.
You May Also Like