Supercharge Your SSH and Kubernetes Resources with Remote Identities


Written by
StrongDM TeamLast updated on:
September 6, 2024Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
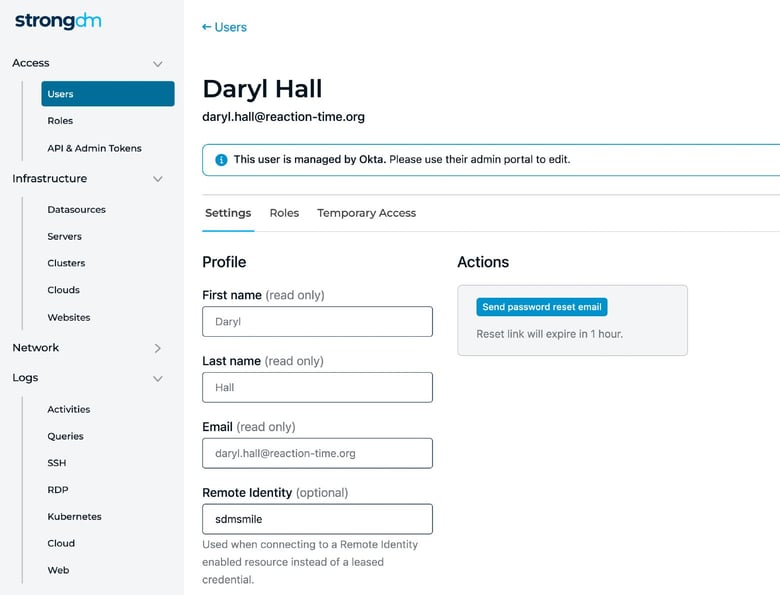
StrongDM, the Zero Trust PAM platform that gives technical staff direct access to the critical infrastructure they need to be their most productive, now gives you more authentication flexibility with Remote Identities. This new feature enables you to connect to StrongDM resources using the identities of individual users instead of a leased credential.
Remote Identities helps you leverage the native capabilities of your SSH and Kubernetes resources and capitalize on infrastructure workflow investments you’ve already made.
Here’s how.
What Is the Remote Identities Feature All About?
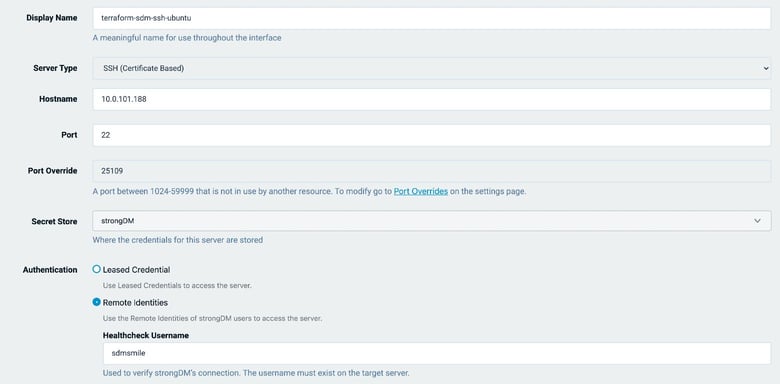
With Remote Identities, you authenticate to an SSH or Kubernetes resource using the identity of the StrongDM user connecting to it instead of StrongDM’s standard leased credential method.
In the StrongDM leased credential model, users access SSH and Kubernetes resources through a centralized set of credentials. This simplifies credential management and helps prevent credential sprawl while preserving all identity information about the StrongDM user accessing your infrastructure in our comprehensive logs.
But, what if you want to take advantage of user profiles and home directories on your servers, or have StrongDM users without auditing privileges relying on native Kubernetes logging and RBAC? Remote Identities allows you to leverage these resource-specific features and more.
Ultimately, though, we leave it up to you to choose if you want to use leased credentials or Remote Identities. Understanding the benefits of using Remote Identities can help you decide.
What Are the Benefits of Using Remote Identities?
The Remote Identities feature allows you to extract more value from your SSH and Kubernetes resources by leveraging their native capabilities.
For instance, it’s now easier to do these tasks:
- Assign Kubernetes permissions at the group level with native Kubernetes RBAC
- Include user-specific profiles on your servers
- Identify specific users associated with processes being executed on multi-tenant systems
Additionally, you can leverage pre-existing investments in infrastructure processes or workflows (such as native alerting, log aggregation, and SIEM integrations).
Have you already done any of the following?
- Set up a SIEM aggregation that consumes native logs directly from your resources
- Establish a local threat identification system that relies on user identities
- Employ disk and compute quotas on a per-user basis
Remote Identities enables you to keep operating all of these processes within StrongDM.
When Does Using Remote Identities Make Sense?
We’ve already highlighted some of the most prominent use cases where authenticating using a remote identity, rather than a leased credential, makes sense. However, let’s recap them here along with a few others:
- Leveraging user-specific profiles and home directories on servers
- Enabling targeted identification and cancellation of server processes based on the user
- Enforcing per-user, per-server quotas on resource usage in multi-tenant systems
- Leveraging native Kubernetes RBAC
- Being able to identify specific StrongDM users in a resource’s native logs
- Using local threat identification systems on resources
- Supporting custom notification, approval, and escalation workflows running on your resources that need to be aware of a user’s identity
New to StrongDM? Sign up for our free no-BS demo and discover how our Zero Trust PAM platform can work for you.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
StrongDM Team, Universal Privileged Access Authorization (UPAA), the StrongDM team is building and delivering a Zero Trust Privileged Access Management (PAM), which delivers unparalleled precision in dynamic privileged action control for any type of infrastructure. The frustration-free access stops unsanctioned actions while ensuring continuous compliance.
You May Also Like




