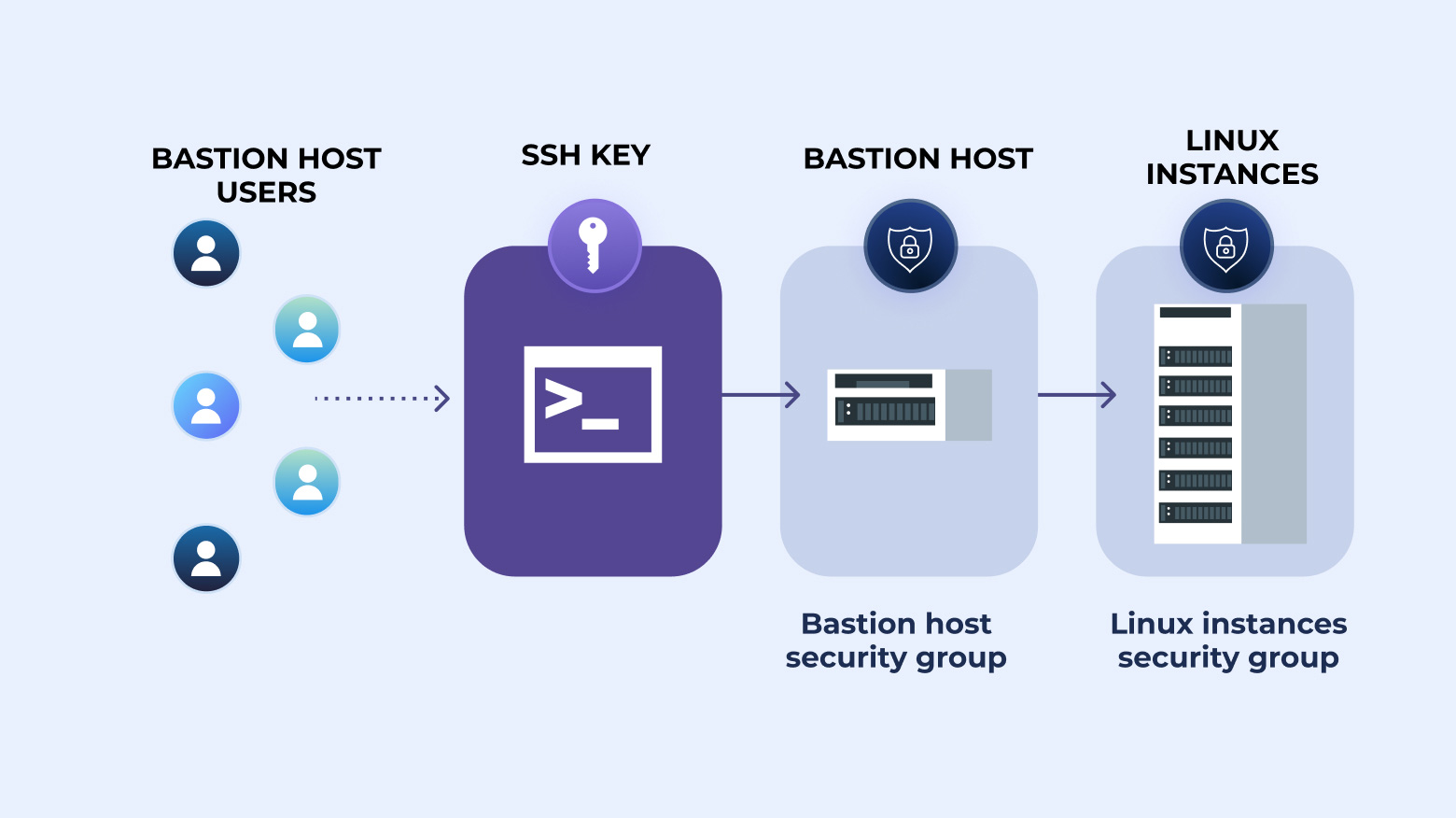
SSH ProxyJump (the -J flag) is a more streamlined way to hop between SSH hosts using one or more bastion hosts. Instead of chaining multiple manual connections, ProxyJump creates a single end-to-end SSH session through the specified jump hosts. It was introduced in OpenSSH 7.5 to simplify access to servers that sit behind firewalls or live in private networks.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

Secure Shell (SSH) is one of the most effective ways to access and manage remote systems. This technology encrypts communications between the client and the server, enhancing system security and preventing unauthorized access. Another important benefit of SSH is its simplicity. This technology is relatively easy to use with various tools and clients, as we will demonstrate below. Plus, you can also use SSH for file transfers, running commands, and even tunneling. This guide explains how to use

This blog post dives into the world of SSH keys and highlights the different types available. By comparing these different SSH key types, we aim to provide insights that allow users to make informed decisions based on their specific security needs.

With an emphasis on the significance of certificate-based authentication, this article seeks to clarify SSH authentication. It gives you a thorough understanding to support the safety of your digital interactions by outlining the benefits of using this approach over traditional ones and covering the implementation steps.

SSH tunneling, also known as SSH port forwarding, provides a secure method for client applications to communicate with remote servers. By encrypting traffic, SSH tunnels ensure data protection during transmission. This article explores the significance of SSH tunneling, its advantages, how it works, and its various use cases.
![How to SSH into Docker Containers [Tutorial]](https://discover.strongdm.com/hubfs/ssh-into-docker-containers.png)
In this article, we’ll cover a way to run console commands in Docker containers that will allow you to mimic the process of using SSH for the same purpose (and if you really need to, a way to gain true SSH access as well).

Learn how Remote Identities helps you leverage SSH and k8s capabilities to capitalize on infrastructure workflow investments you’ve already made.
This tutorial will walk you step by step through how to manually set up SSH passwordless login to a Linux server. These commands should work on the majority of Linux distributions, and instructions are included for modern client machines of the macOS, Windows, and Linux varieties.

Two of the most important questions in security are: who accessed what, and when did they access it? If you have any Linux or Unix machines, you’ll likely find answers in the sshd log. sshd is the Secure Shell Daemon, which allows remote access to the system. In this article, we’ll look at how to view ssh logs.

In our last post, we discussed some of the challenges that are inherent to management of SSH keys across your infrastructure as you scale the number of team members and servers. In this post, we will dig into some of your options and the trade-offs that they provide.
Infrastructure and DevOps administrators face significant barriers in managing Secure Shell (SSH) keys. In this article, we’ll explore the complexities of SSH key management. We’ll also show how to effectively authenticate users without having to manage SSH keys for individual users.

Configure the hosts for logging verbose data, and then send the logs to a cloud provider for long-term storage and access.

SSH audit logs allow you to determine, either retroactively or in real-time, when an unauthorized or destructive action was taken, and by whom.