Unmasking Cozy Bear (APT29): The Urgent Need for Continuous Authorization


Written by
John MartinezLast updated on:
August 22, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Recently, Microsoft revealed that a cyber attack on its systems in late November 2023 was orchestrated by a group of state-sponsored threat actors from Russia. Around the same time, Hewlett Packard Enterprise (HPE) also disclosed that it fell victim to an attack carried out by APT29, or Cozy Bear, a hacking crew associated with Russia's Foreign Intelligence Service.
Cozy Bear specializes in targeting governments, diplomatic entities, non-governmental organizations (NGOs), and IT service providers, primarily in the U.S. and Europe. These state-sponsored groups aim to clandestinely gather strategic and sensitive information for Russia, maintaining prolonged access without raising suspicions.
The latest information suggests that the extent of the cyber campaign might be larger than initially believed. Despite this, Microsoft did not disclose the identities of other entities that were specifically targeted. It’s not for us to speculate, but it is clear that attacks of this nature are becoming far more prevalent. One of the reasons they’re successful is that many organizations are not employing the right security measures to protect their infrastructures, which are becoming more complex and harder to fortify.
More Attacks Happening Through Compromised Accounts
Cozy Bear employs tactics involving the use of hijacked legitimate accounts to gain and expand access within a target environment. Additionally, the group is known for exploiting OAuth applications to traverse cloud infrastructures, both for lateral movement and privilege escalation attacks, with the intent to collect sensitive information such as internal emails.
Because their attack entry point is through legitimate accounts, it allows them to operate discreetly. Their access looks to be normal and accepted. Their behavior, however, is anything but normal, and can’t be caught with legacy privileged access management (PAM) solutions that most organizations are using.
As with all breaches, the post-mortem perspective is hugely instructive. It isn’t about, “we told you so,” but rather, it helps break down the how so we can arrive at the best form of prevention to be used in the future, and improve overall security posture.
What’s especially interesting about this particular attack, and pretty much all of Cozy Bear’s efforts is…well, nothing.
Standing Credentials Do Not Align With Modern IT Infrastructures
Getting unauthorized access to systems through compromised accounts is an old tactic. It continues to work and is actually becoming an increasingly popular approach because it’s harder to assign and manage authorization privileges.
As stacks become more complex (more tools, more integrations, more access points) and access is increasingly decentralized (it’s no longer just a rare group of admins who can access, or grant access, to internal systems), the problem is unwieldy and legacy PAM tools have outlived their usefulness for companies that want to prevent attacks like the ones perpetrated by Cozy Bear and others like them.
In the case of this particular attack, overprivileged and underprotected user accounts allowed Cozy Bear to hijack the same credentials, along with tokens, and sessions. That gave them lateral movement within Microsoft’s cloud environment, and then they took advantage of privilege escalation. And all of this was done by the Cozy Bear crew dropping their OAuth proxies throughout the infrastructure. Lots of access, and likely, all of it was authorized, but clearly, it was unchecked as well.
The attackers are at fault; there is no question. But the discipline of authorization rests on the shoulders of the targeted organization. At its most basic, it’s about what operations you allow your users to perform on infrastructure. But because of the complexity of modern stacks, the use of standing or rotating credentials – the type of access approach employed by legacy PAM solutions – are not adequate. In fact, they are putting organizations at risk. Coordinated attacks like this one will continue to be successful by groups like Cozy Bear if this isn’t addressed.
To address the issue, organizations have to establish and abide by the principles of Zero Standing Privileges (ZSP) and Just-in-Time (JIT) access. And they must enable Continuous Authorization (Continuous AuthZ) to carry it out.
ZSP actively promotes the implementation of a tenet of zero-trust security architecture by taking the concept of least privilege to its ultimate conclusion: no standing privileges are granted to users by default.
The concept of JIT access involves granting access each time a user needs to operate on a particular resource. Subsequently, this access is automatically revoked once the user completes their assigned task, or the time expires. By adopting this permissions strategy, organizations effectively minimize their attack surface by granting access when a user needs it, and only for the duration needed, preventing a malicious actor from hijacking stale, but active sessions.
Let’s explore the role that Continuous AuthZ plays in thwarting hijacked sessions by bad actors.
Vulnerable Entry Points + Privileged Escalations = Breach
Once the intrusion was successful, the Cozy Bear crew applied credential roaming to overwhelm the Active Directory system with LDAP queries from atypical properties. That requires the coordinated effort of multiple impersonated accounts. For the attackers, it was a numbers game. Every time an attempt was made to gain access, they had a chance – perhaps a slim one, but still, they had a chance – to fake their way in. This is the result of malicious intent meeting vulnerable hardware and management software.
With access, the hackers eventually found an arbitrary file vulnerability that could be weaponized to achieve remote code execution. They did this by logging in as the person who was eventually victimized and distributing OAuth proxies across the environment.
In this day and age, this kind of vulnerability seems inconceivable. While security teams are aware of these types of attacks, they’ve misread how to solve the issue. Most organizations began their perimeter defense with PAM solutions, which operate like gatekeepers. As the name indicates, these solutions were built for a time when just a few, privileged users were supposed to have access to key systems. That’s all changed, though.
PAM solutions are making access, and the access process, a choice, not a solution. It looks a little like: quick access or complicated security checks, take your pick. For the user, it looks like the door is being shut when they should be legitimately accessing important resources and applications (which is slowing down business processes and killing productivity), or they are getting rapid access, but the reality is that their PAM is too permissive.
PAM solutions check a user when they enter the environment or access a specific resource, but once access is granted, that user gets free range to move about freely. That’s where Cozy Bear was able to hijack accounts. Standing privileges and recycled credentials actually enable this type of activity.
That’s why a different approach is needed – Continuous AuthZ is checking (continuously):
- Should this person have access to this application?
- Should this session be this long?
- Does their device have end-point protections turned on as expected? Is their machine infected?
- Are they in a location or geography we expect?
There are a huge number of factors that have to be evaluated to determine the legitimacy of a user and a session. If those things are evaluated once at session start, (or only a small subset of signals was accessed), then it’s just a matter of time before you discover the damage that was done. That’s where headlines are made.
How Continuous AuthZ Provides the Best Defense for Modern Infrastructures
Continuous AuthZ is in a constant mode of evaluation, and response: let the user continue or stop them in their tracks.. The authorization never stops, and mathematically, it becomes impossible to keep duping your credential authorizations repeatedly. Even if you get past the first gate, the attacker will eventually be discovered.
The StrongDM platform, and all aspects of Continuous AuthZ, is based on the Zero Trust model. It’s probably not the way you’d want to handle a relationship with your spouse, but it’s mandatory to keep modern environments secure. Users who have adopted our approach are benefitting from a foundation that fundamentally changes the nature of access from static to dynamic. To do that, we use these elements:
Zero Standing Privileges and Just-in-Time (JIT) Access
The implementation of ZSP is facilitated by the concept of JIT access. JIT provides short-term or one-time access to resources through the creation of ephemeral credentials, which automatically expire once the user no longer requires access.
Within a JIT workflow, users can request access to resources on-demand, receiving rapid approval based on role-based or attribute-based access controls. These controls are applicable to both human and non-human users, enhancing access control measures.
In certain instances, requests for new resources or elevated permissions may necessitate administrator approval. A JIT workflow, seamlessly integrated with a support platform, enables users to explain their reasons for elevated permissions, and that information can instigate the process of rapid approval or denial of their requests. Since all requests follow the JIT workflow, organizations can maintain comprehensive logs and session records, facilitating easier auditing processes.
Compare this to the behavior of the Cozy Bear attack. There were no additional measures required to verify or evaluate user access. Again, once in, the user had access to a wide range of applications resources. The Cozy Bear team used “standing access” that existed for the account they hijacked.
Dynamic Access Workflows
StrongDM Access Workflows are built to provide rigor and accuracy to authorization. They enable you to automate how access requests are submitted, reviewed, and approved (or denied). With access workflows, you can create subsets of resources and allow users with particular roles to request access to them. When requests are made, the pre-selected approvers for that workflow are notified and may then accept or deny the request.
These workflows ensure that the right users can obtain access to the necessary tools and, just as efficiently, revoke that access when required. It eliminates the concept of standing credentials by streamlining access requests in accordance with security policies. The benefits of StrongDM Access Workflows include:
- Enhanced Security: Access is granted only for a specified duration, eliminating the need for standing access and thereby reducing the overall attack surface.
- Improved Efficiency: JIT access simplifies user rights management, eliminating the necessity to keep track of individuals with standing permissions.
- Reduced Insider Threats: The risk of persistent access to sensitive data is mitigated. With JIT, the potential damage caused by an insider is confined to a narrow access window.
StrongDM Access Workflows significantly enhance the end-user experience. End-users benefit from an individualized Access Catalog, displaying resources based on their role or resource attributes (such as environment tags, geo-location, etc.). Users can seamlessly request access and connect, subject to either human or automated approval.
Here’s an example of a workflow in StrongDM:
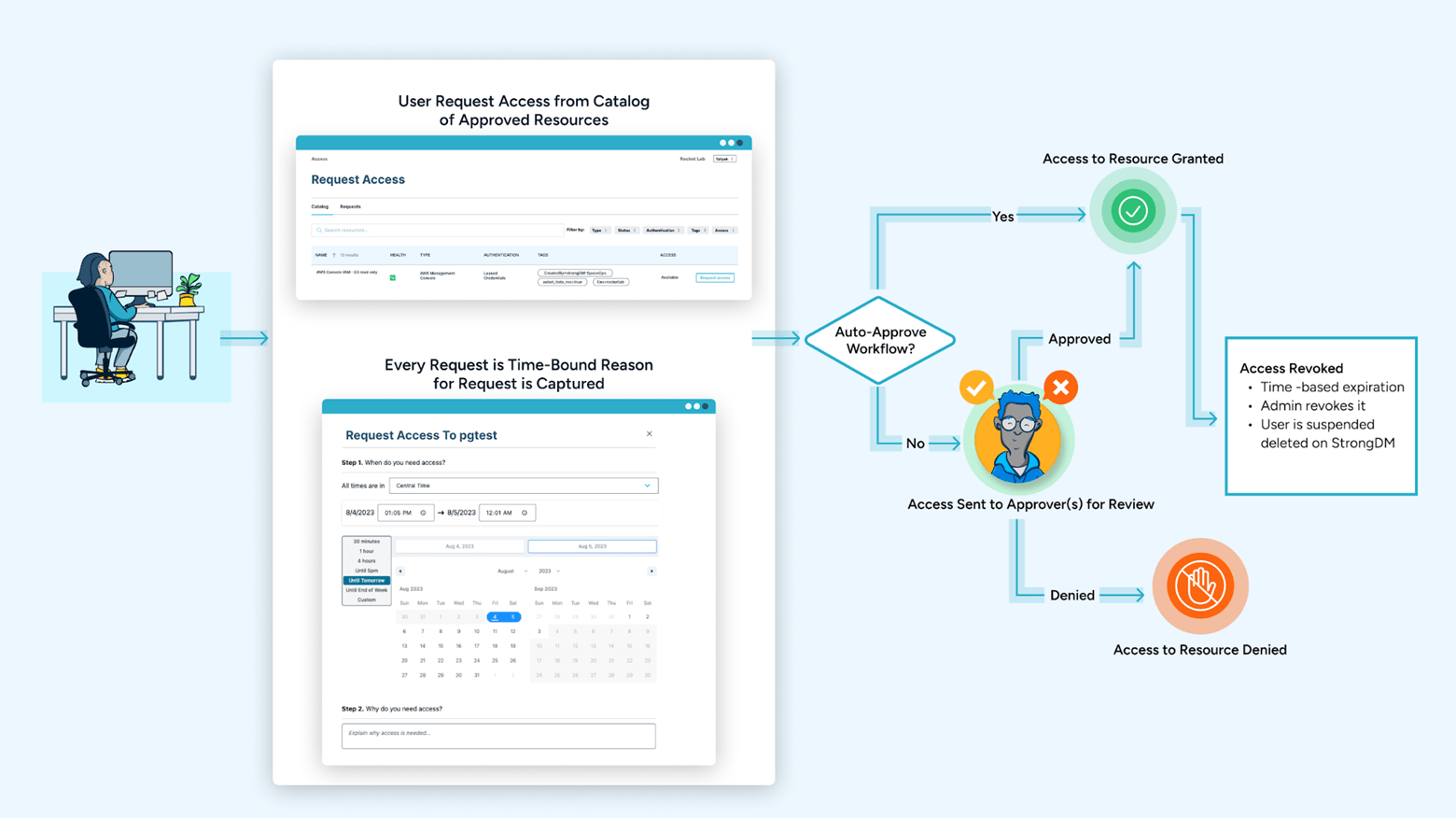
By implementing workflows that simplify access requests, approvals, and revocations, you can ensure that access is only active when necessary and automatically expires. This approach renders standing credentials obsolete, thwarting the potential use of such credentials by malicious actors and simultaneously reducing your overall threat surface.
Access requests are not limited to specific platforms and can be seamlessly integrated into common tools within your stack or facilitated through ChatOps and service desks. As an illustration, the integration of StrongDM Access Workflows with Slack allows your team to initiate and authorize workflows directly within the Slack interface. This integration minimizes context switching, enabling your team to utilize their everyday tools while ensuring secure access.
Continuous Zero Trust Authorization
At the risk of oversimplification, legacy PAM tools are “one and done.” Authorize with a yes or no at session start, and then the job is done. You can be a sophisticated hacker involved with Cozy Bear, or a teenager in Temecula; going after an environment governed by legacy PAM is precisely what you want.
The alternative approach is one that is continuous. The StrongDM platform abides by the concept of Continuous Zero Trust AuthZ, which is the real-time monitoring of access and operations throughout your infrastructure. It includes the capacity to implement contextual access policies instantly.
Real-time, instant, and actionable…that’s tough for an attacker to overcome. Continuous Zero Trust Authz is continuously monitoring for risks and promptly enforcing policies when a potential risk is identified: It uses the following to achieve this:
- Deep Visibility: Gaining insight into the ongoing access and operations within your infrastructure, considering the contextual details surrounding these actions.
- Flexible Access Controls: Implementing access controls that can factor in various contextual elements in authentication decisions, such as devices, roles, attributes, and more.
- Distributed Policies: Enforcing policies in real time across your network, irrespective of the system, tool, or location where an activity is occurring.
With Continuous Zero Trust AuthZ, the StrongDM platform elevates access control measures that ensure that the right individuals have the appropriate access to your critical assets. The platform achieves this with the StrongDM Device Trust feature which enhances an organization security stance by leveraging device posture data sourced from leading endpoint security providers such as CrowdStrike or SentinelOne.
This feature guarantees that access requests to vital components of your infrastructure, spanning databases, clouds, servers, clusters, and web applications, are not granted automatically. Instead, access is explicitly permitted following a thorough assessment of the user's device security. The approach adds an additional layer of protection to the target systems.
Audit Logging For Rapid Remediation
There’s a helplessness that happens when you recognize you’re under attack, but you don’t know the extent of the damage, where it’s happening, or how to address it. In many attacks, an alert isi run up the flagpole, and a lot of frantic scurrying goes on, but to no avail. Russian hackers are exfiltrating massive amounts of valuable information and all you can do is watch it happen.
In the event of an information security incident, swift and comprehensive information gathering becomes imperative. The likelihood of involving external entities, such as an incident response team, adds a layer of complexity to the process.
Approaching log management and retention as mere checklist items is inadequate. Instead, the focus should be on ensuring that audit logs from all critical information systems contain detailed and substantial data. Without such richness, logs may end up being incomplete, inaccurate, or even entirely absent. This deficiency hampers the availability of historical information crucial for addressing cybersecurity questions, concerns, or incidents.
The urgency to collect log data for the incident response team becomes apparent during a security incident. Delays in this process can compromise efforts to counteract malicious activities promptly, exposing your systems to vulnerabilities. In the realm of security intelligence, time is of the essence, and there is no room for unnecessary delays.
Utilizing StrongDM's report library allows you to precisely track user activities, including who is performing actions, the timing of these activities, and the locations where they are executed. This feature proves to be a significant time-saver during audit processes, ensuring a streamlined experience without unnecessary stress. Furthermore, it empowers you to conduct internal audit checks more frequently, enabling the early detection of security issues and, ultimately, facilitating the completion of tasks well before the 5pm deadline.
The new security is continuous security
The gatekeeper model is dead…or it should be. Attacks are increasing and irrespective of their level of sophistication, IT stacks have to operate in anticipation of breach at any and all times. An attack can come from anywhere. The model for security has to be aligned with the real-time, JIT, and continuous nature of attacks.
Want to see StrongDM in action? Book a demo.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like




