Unauthorized access—the unauthorized entry or use of an organization's systems, networks, or data by individuals without permission—is a common way for bad actors to exfiltrate data, inject malicious code, and take advantage of all types of breaches, and can have severe consequences for an enterprise and its customers.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
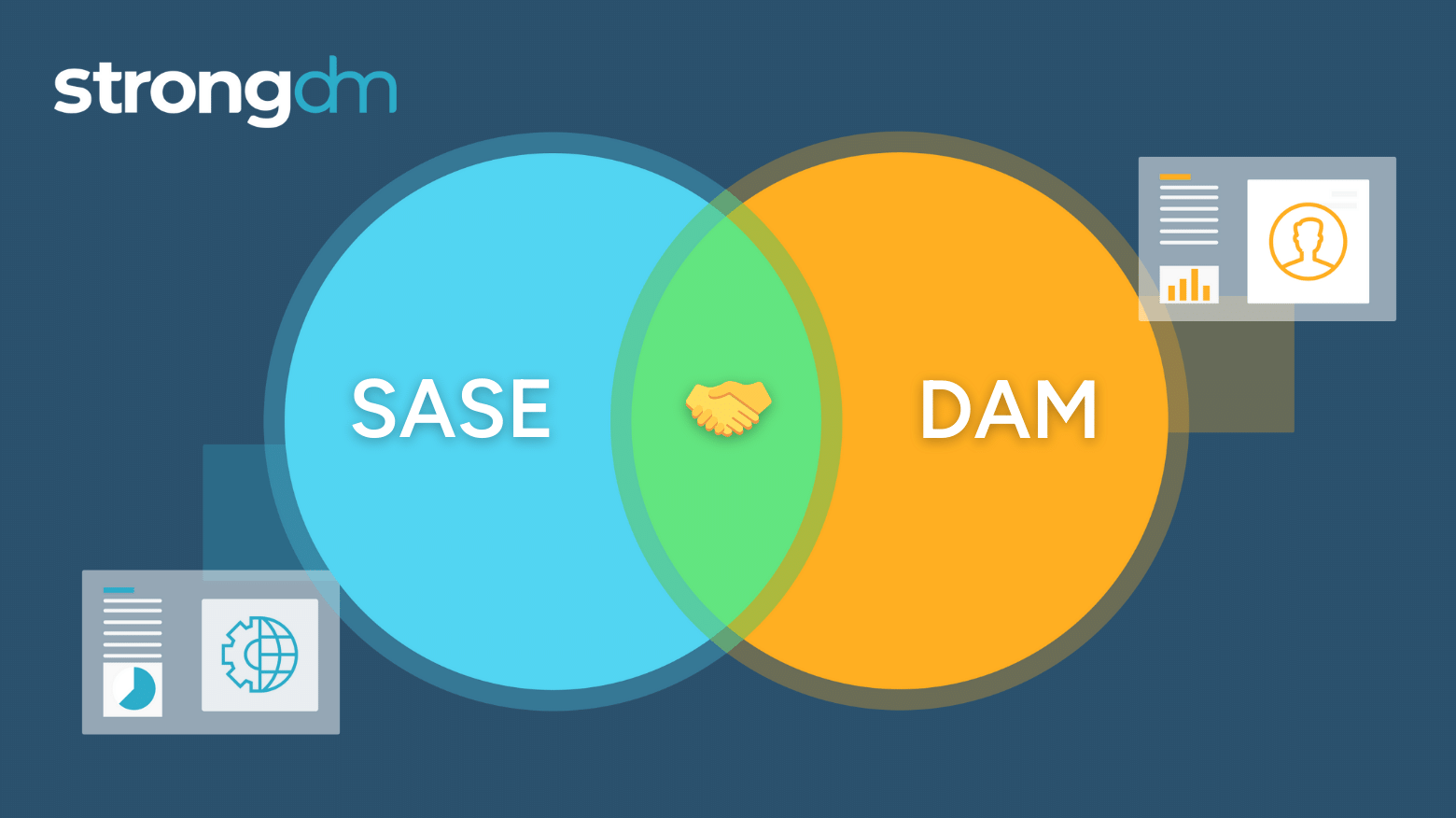
While SASE excels in providing broad network security coverage and solves broad issues for regular enterprise users, it is not equipped to address the specific requirements of privileged users who wield extensive administrator or superuser privileges. Dynamic Access Management (DAM) addresses the specific needs of privileged users by providing granular control over their access grants and sessions in real time.

Cozy Bear specializes in targeting governments, diplomatic entities, non-governmental organizations (NGOs), and IT service providers, primarily in the U.S. and Europe. These state-sponsored groups aim to clandestinely gather strategic and sensitive information for Russia, maintaining prolonged access without raising suspicions.
The CSA CCM is a cybersecurity control framework specifically designed for cloud computing. It outlines a comprehensive set of best practices and security controls across 17 domains that are designed to ensure that cloud environments are secure and resilient against an ever expanding threat landscape. The CCM framework is structured to provide clarity and actionable guidance for the implementation of security measures in a prescriptive and adaptable way for recognized compliance standards and
We are thrilled to announce an exciting new addition to the StrongDM Dynamic Access Management (DAM) platform: Continuous Zero Trust Authorization. This powerful capability can help organizations leap forward in the Zero Trust journey by enabling continuous, contextual, and granular authorization and control over resources and data
We are thrilled to announce a new feature to our StrongDM® Dynamic Access Management (DAM) platform: Device Trust. This feature amplifies your organization's security posture by employing device posture data from endpoint security leaders CrowdStrike or SentinelOne.
The AWS Well-Architected Framework has been a staple for many years for AWS practitioners of all sorts, including cloud architects and platform engineers. It’s a blueprint for architectural and design best practices that will lay the foundation for resilience, operational efficiency, and security on the AWS Cloud.

I'm continuously shocked by how poorly the PAM industry has treated customers to date. Shame on CyberArk, Delinea, and all the rest of you for persisting with such predatory models. The business model is "squeeze the blood out of them, then squeeze harder." The deployment model is "you'll never ...
Historically, finding an infrastructure access management solution that is secure while still being easy to use has been extremely difficult. Too often, ease of use and complexity end up at odds. StrongDM addresses this challenge–and does so by integrating with your existing identity-based security initiatives. This blog details how StrongDM enables organizations to level up their access management approach to meet the requirements of Dynamic Access Management (DAM), bolster security, and

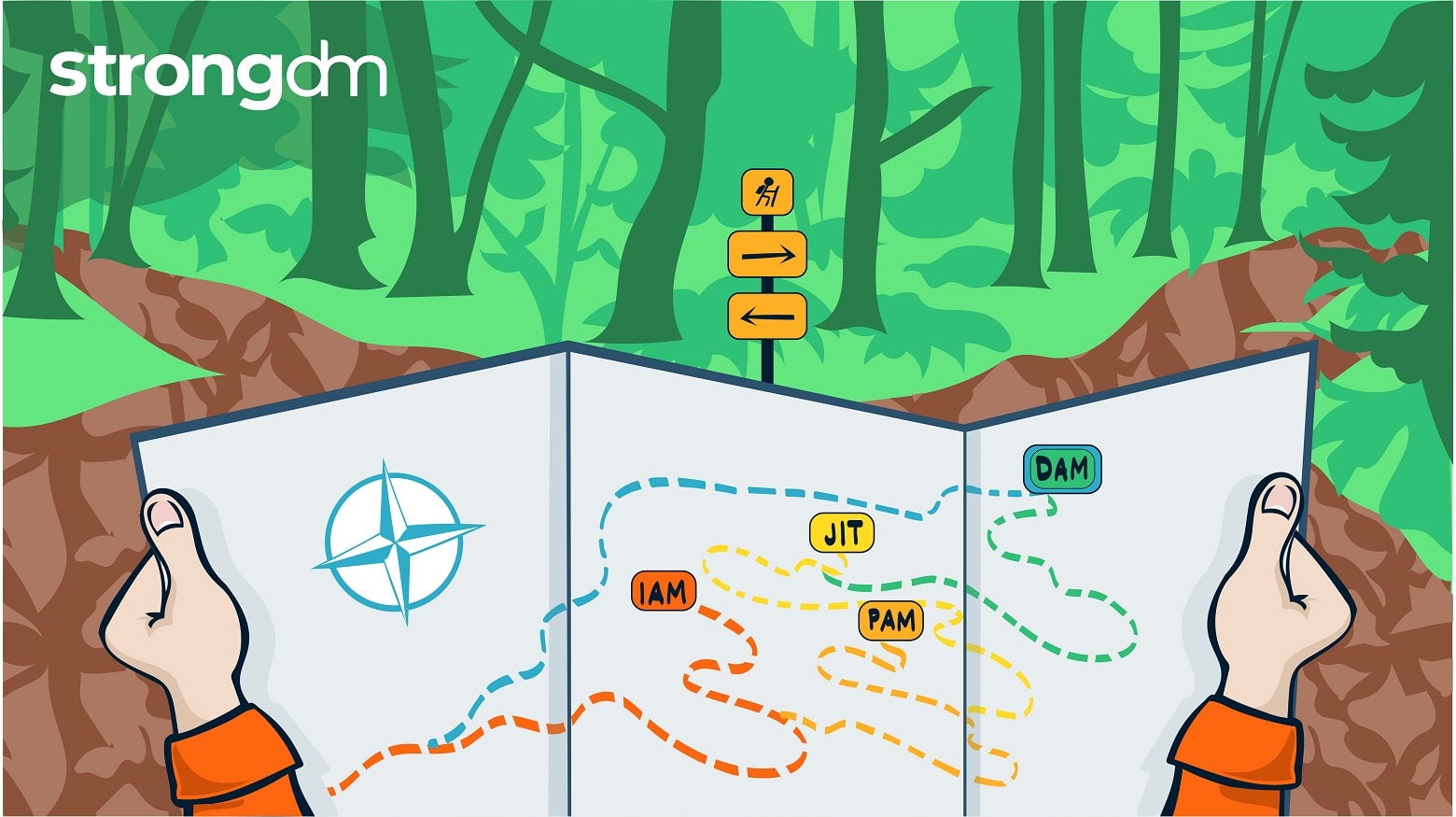
Standing Credentials. They’re a problem that seems to persist despite the latest security and access innovations. They’re also one of the main reasons that achieving zero trust is so hard–and enough of a problem that two strategic security initiatives have come to the forefront: Just-in-Time (JIT) access and Zero Standing Privileges (ZSP).
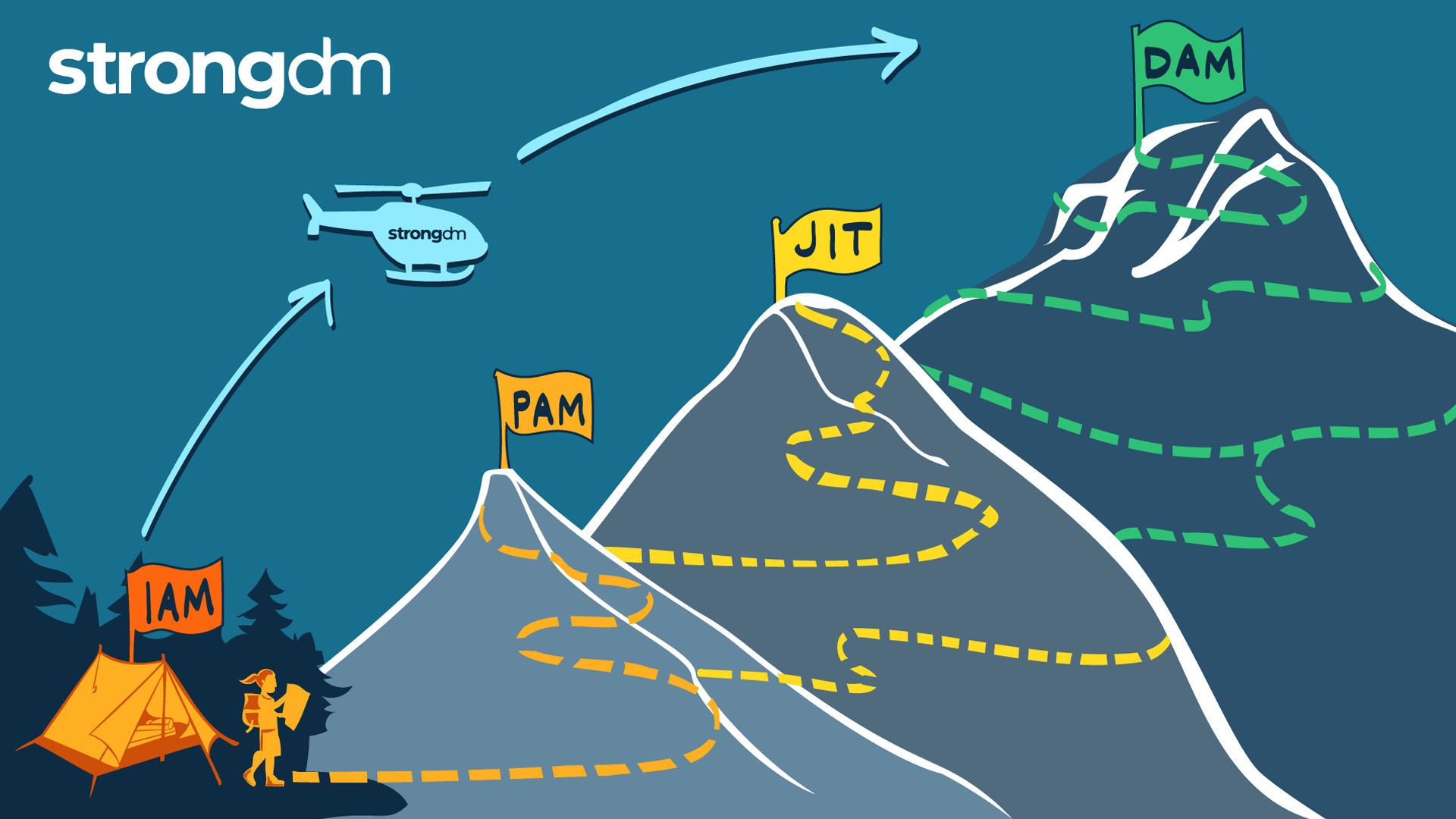
This article is your map for taking the work you’ve done with identity and your identity provider (IdP) and using it as your launchpad for access management. Shifting from identity-based access to a more dynamic access approach is necessary for organizations looking to modernize their access management and better protect sensitive resources at scale and in the cloud.

