_optimized-3.png?width=780&height=438&name=6143adde8367e353c043f707_strongdm-blog-19-(1)_optimized-3.png)
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
It’s a nightmare scenario. You work in a regulated market, like financial services or healthcare. There’s a breach. You know the question is coming, but can you confidently answer it?
“Who at the company could have seen those social security numbers?” What about its follow-up question: “Who actually did see that number?” In other words, who theoretically had access to that information, but also, who actually accessed it?
Often, employees will have access they may not need for their job (over provisioning), and risk is increased because your breach surface just got that much bigger. But that’s the nightmare scenario.
What about the day-to-day activities? The ones where someone in marketing requests access to a production customer database—do you know if that person really needs access to it?
A critical part of embracing zero trust and implementing privileged access management (PAM) is ensuring that each employee’s access to technical tools is as close as possible to what’s needed for their specific role. But creating unique roles for every individual can be expensive, time-consuming, and difficult to do.
For example, data scientists may need access to sensitive data, but because of the complexity associated with access management, many companies simply provide that access to the entire engineering department—even though 80% of the department doesn’t need that access. Suddenly, you have audit and security issues as well, especially if you ever have to determine how an infrastructure breach occurred.
The good news is that there’s a way to avoid the pitfalls of providing too much or too little access—and it all starts with role and access discovery.
Why Access Management Is Hard
Imagine you’re building a house, but instead of having a floor plan or starting with the foundation, you just build it as you go, adding room after room. Over time, you’ll likely end up with a nice house, but not necessarily a functional home (real life example: the Winchester Mystery House in San Jose).
Access can fall into the same trap. Over time, your organization will add new people, new teams, new roles, and new systems. And before you know it, you have no source of truth for who has access to which systems, much less who needs access to them. This inevitably leads to over- and under-provisioning, not to mention that it's now extremely difficult to audit what is happening in each system.
It usually takes a major financial event, like an initial public offering, or a compliance event, such as achieving SOC 2 compliance, to drive these types of projects. But for any team that doesn’t have those compelling events, you’ll likely be forced to deal with the accumulated frustration of multiple teams who just want the access they need.
Enter Role & Access Discovery
To put it simply, if you start without a plan for infrastructure access, you're going to regret it—and yet, many companies are inclined to skip this step. The result is a hodgepodge of access across multiple roles and systems that becomes impossible to manage. Organizations need to shift their mindsets and behavior to proactively think about who needs access to what, document it, and standardize it. That’s where Role and Access Discovery comes in.
Role and access discovery is a collaborative process that defines:
- The structure of the company
- The structure of the teams
- Which roles need access to which systems
- How long is that access needed
The task of role and access discovery and planning often gets assigned to technical staff, like the IT team or infrastructure team. And as discussed above, organizations that don’t take the time to think about their end goals or plan access upfront may end up haphazardly providing too little or too much access to individual employees.
It's critical for those planning access to consider the duration for which access is necessary based on the role an individual plays within the organization.
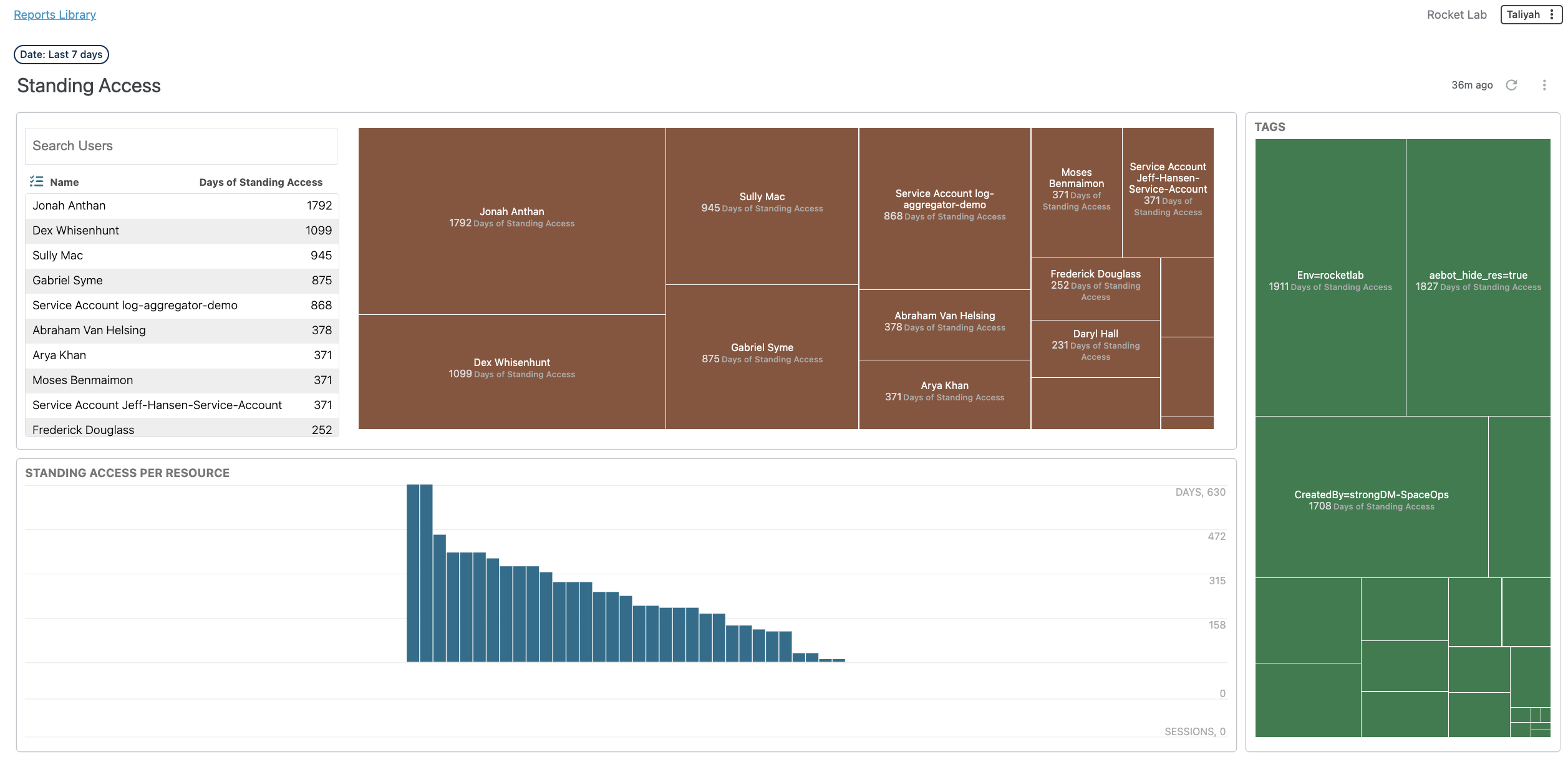
Standing privileges offer users the ability to access resources from any location at any time without time limitations or additional approvals needed for privileged actions. This level of convenience, though appealing, can pose significant security risks. If these credentials fall into the wrong hands, the potential for harm is considerable. Administrator credentials in particular often grant broad access across many systems and may include the power to modify user permissions extensively.
In contrast, Just-in-Time (JIT) Access presents a more secure alternative. It allows for the provisioning of temporary or single-use access rights that expire once their purpose is fulfilled. This method drastically minimizes the risks associated with standing privileges by ensuring access is granted only when necessary, and without exposing actual credentials to users.
💡Make it easy: Just-in-Time Access works best when it is easy for the end user to request and receive access. It should also be auditing to map the end to end chain of events, who is requesting access, why they are requesting it, and for how long. Play the video below to see how easy StrongDM makes Just-in-Time access and try it for yourself.
Adopting automated JIT access mechanisms provides a balanced solution, mitigating the risks of privilege misuse while avoiding operational impediments. This approach not only enhances security by reducing the organization's exposure to potential threats but also streamlines processes for administrators and minimizes inconvenience for all users.
Starting the Access Conversation
Getting a clear picture of how resources are actually utilized can enhance your security posture and streamline Just-in-Time (JIT) workflows, especially for resources that aren't used all that often.
Even if you have a list of names of employees and systems, tracking and controlling access needs to be granular. That means collaborating across teams—IT, DevOps, HR, Security—to determine how roles should be categorized and how access should be managed for each role.
Document all internal audits of role-based access. And repeat this plan at a consistent cadence, at least every year, if not quarterly or more, based on your needs.
To get the most out of your analysis, consider incorporating these crucial steps:
- Audit who has access to what resources and why.
- Review utilization of users, resources, and access grants.
- Identify vulnerable resources by reviewing standing access grants.
- View access requests and temporary access grants across your entire infrastructure.
💡Make it easy: Understand the secutity risk profile of all standing access grants. Make decisons on how should continue to have access, and where access can be revoked without introducing friction. Try it for yourself.
By closely examining who has access to various resources and when, you'll be able to make decisions based on solid evidence. This approach allows you to tailor access rights perfectly, ensuring team members have the access they need, precisely when they need it.
Getting Started
Curious about how to get started? We have a few resources to help you down the path:
- Download the Role & Access Discovery Workbook - an interactive tool that will help drive the process forward
- Check out our webinar series on Getting Started with Access Management. The first session is focused on Role and Access Discovery—you can register here.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
Justin McCarthy, Co-founder / CTO, originally developed empathy for Operations as a founding and pager-carrying member of many operations and data teams. As an Executive, he has led Engineering and Product in high-throughput and high-stakes e-Commerce, financial, and AI products. Justin is the original author of StrongDM's core protocol-aware proxy technology. To contact Justin, visit him on Twitter.
You May Also Like