StrongDM introduces Leash, an open-source project delivering real-time policy enforcement for agentic AI. Gain visibility, control, and safety over autonomous workloads with unified access and runtime security.


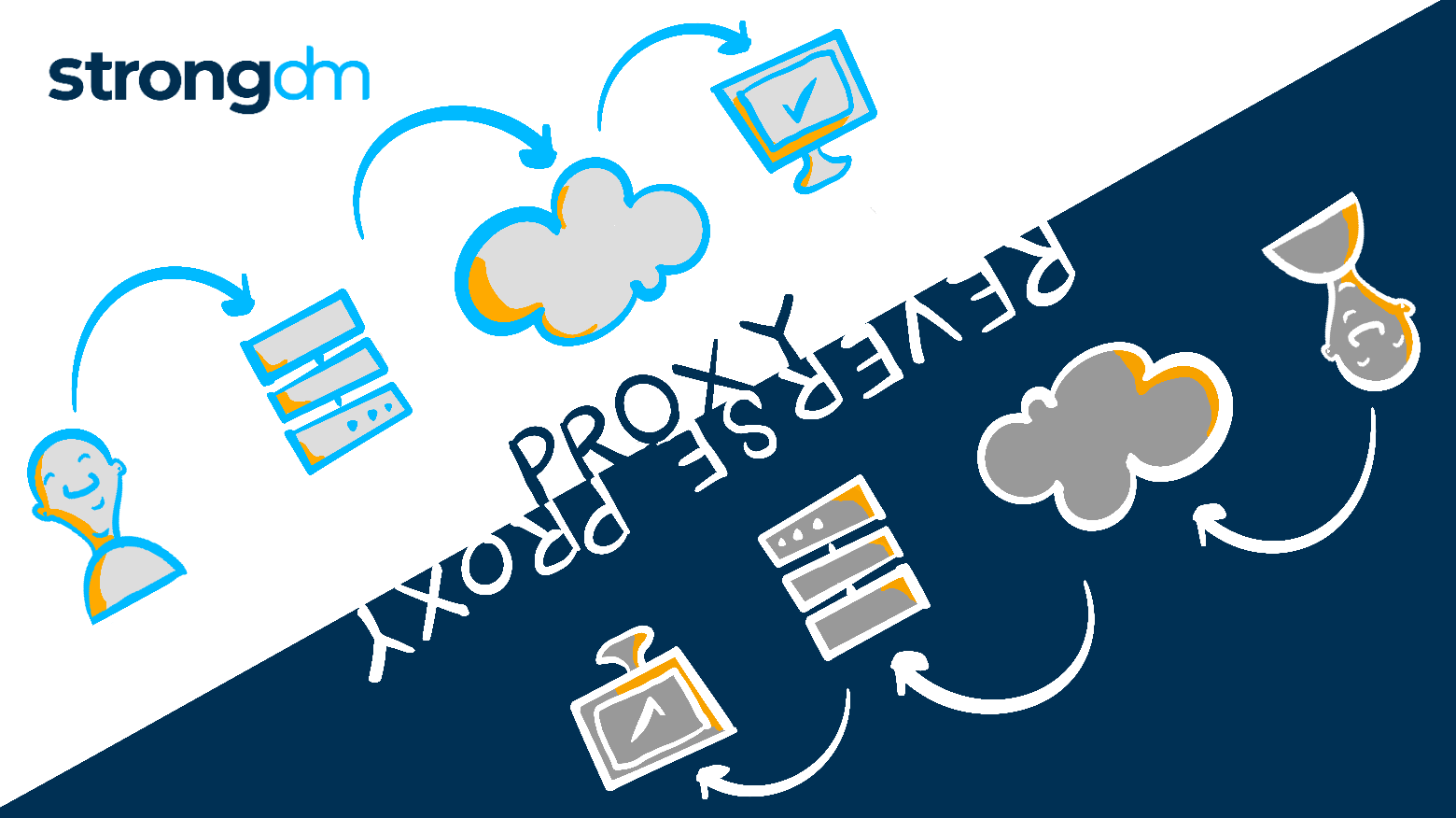
Co-founder / CTO, originally developed empathy for Operations as a founding and pager-carrying member of many operations and data teams. As an Executive, he has led Engineering and Product in high-throughput and high-stakes e-Commerce, financial, and AI products. Justin is the original author of StrongDM's core protocol-aware proxy technology. To contact Justin, visit him on Twitter.
StrongDM has been featured in Forbes, The New Stack, VentureBeat, DevOps.com, TechCrunch, and Fortune.








_optimized-3.png)