Written by
Maile McCarthyLast updated on:
September 6, 2024Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
The flexibility of the modern cloud has made access needs more complicated, with more employees requiring access to a company’s critical systems. In fact, our survey found that 93% of technical staff have access to sensitive infrastructure such as servers, clusters, databases, and cloud APIs. But in many organizations, access management has not kept pace with innovation.
Consider these neat-and-tidy old metaphors for network access: the bouncer barring the door, the moat-and-castle, bank vault, keys to the kingdom…. These days, the reality on the ground is much messier. The rise of democratized access to data, serverless computing, and ephemeral infrastructure has forced organizations to stitch together a hodgepodge of IAM products, authentication tools, and custom scripts.
The result? A squadron of competing bouncers wading through multiple moats, trying to restrict access to all of the treasures in your metaphorical kingdom — a recipe for chaos if you’re trying to operate a business.
Innovation is Pushing Access Beyond Human Scale
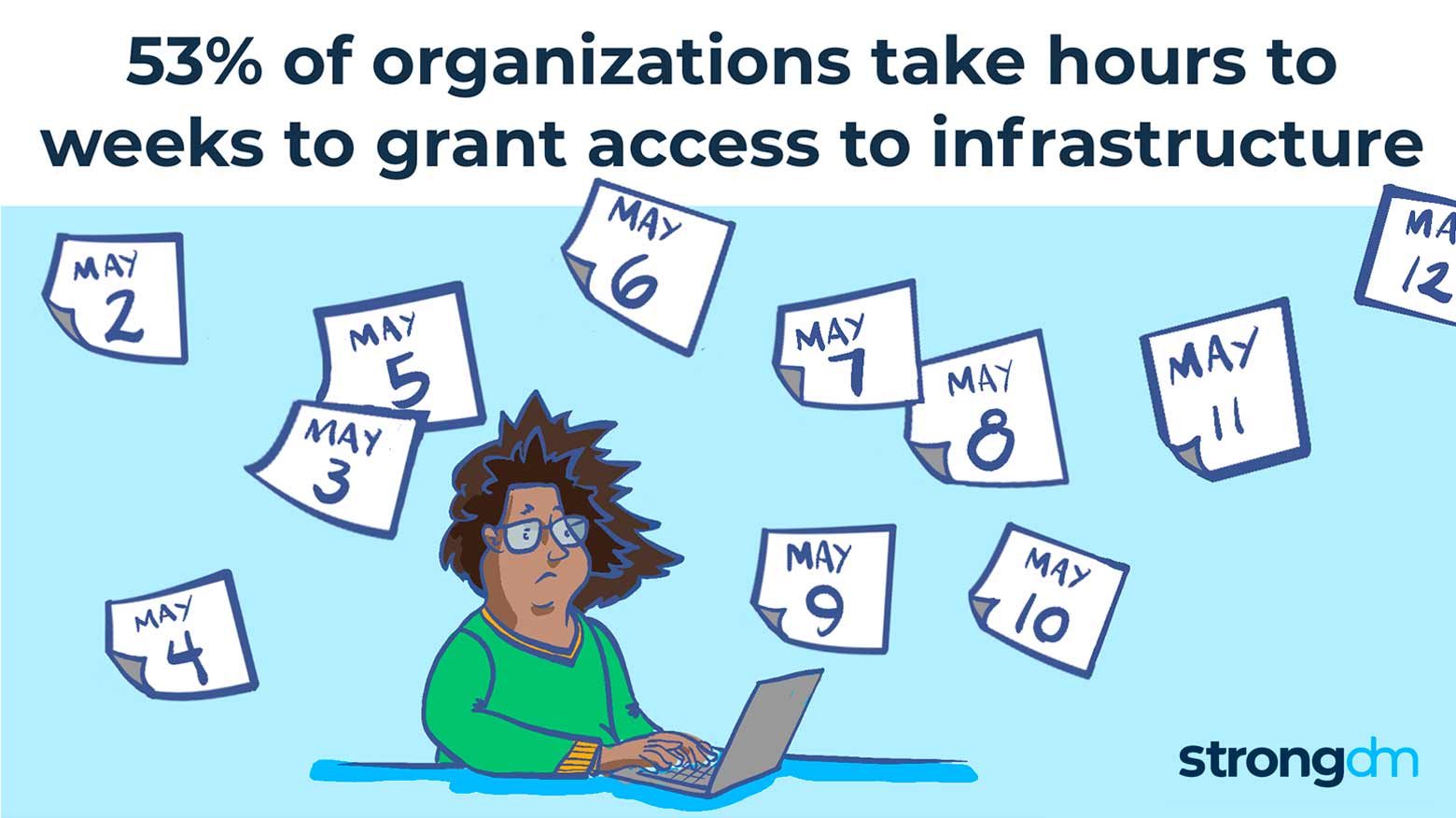
These access issues prevent developers from meeting business demands. Eighty percent of our survey respondents named access management as a critical initiative over the next 12 months, and for good reason. Methods of access management have not kept pace with growth.
Of the organizations in our cohort, nearly all have technical staff with access to sensitive infrastructure. Or, perhaps a better way to put this — these organizations have staff who need access to sensitive infrastructure. Unfortunately, they’re running into bottlenecks and administrative overhead when they try to get it.
Of the organizations we surveyed:
- 53% take hours to weeks to grant access to infrastructure.
- 88% require two or more people to grant and approve access.
- 25% require four or more!
These slow-downs lead to business disruption and increase the likelihood of work-arounds that impact security. And the problem isn’t going away. It’ll only get worse.
Chaotic Access Puts Your Business at Risk

Despite the risks, credential sharing is still a common practice.
Among the people we surveyed:
- 65% use team or shared logins.
- 45% use one-off permissions.
- 42% use shared SSH keys.
Employees share logins for many reasons. Sharing one account among multiple users may reduce friction and make it easier to collaborate with colleagues. And organizations may attempt to save money by buying fewer seats rather than acquiring individual accounts for every user.
But these benefits come with a downside. Password-sharing carries significant risk for organizations. This practice increases the odds of sensitive company information being leaked, makes accounts more vulnerable to phishing attempts, and amplifies the harm those attacks may cause by making it easier for bad actors to access other parts of your network.
Additionally, shared logins make evidence gathering impossible. In our survey, 41% of participants named evidence gathering for compliance as a top challenge. It’s hard to establish who is doing what when employees share passwords.
It’s Time For Access You Can Actually Use
Our survey found that organizations face access challenges across the entire stack, especially for these systems:
- 60% cloud providers
- 57% databases
- 57% data centers and servers
But with a lack of shared language across platforms — with private and public clouds, data centers, virtual machines, and even SaaS applications in the mix — security and engineering may find themselves working at cross-purposes.
Access causes friction when users have to jump through hoops, asking: What buttons am I going to click? What passwords do I need to remember? How many tools are we going to use? Ideally, teams would standardize access across all systems, but when you get down to individual IT teams and development teams, most users want to stick with what’s comfortable.
That’s where StrongDM comes in. Our Zero Trust PAM platform makes it easier for engineers to adopt security best-practices in their day-to-day life by unifying databases, servers, containers, and more on a single control plane. Admins abstract the layer of who has access to what – no more need for shared logins. And simplified workflows let users gain access in minutes rather than hours, days, or weeks. We make access easy, so you can focus on getting things done.
Is your infrastructure access overdue for innovation? Check out the full report, 2022: The Year of Access. Then schedule a free demo of StrongDM to see how our Zero Trust PAM platform can help you upgrade access management today.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Maile McCarthy, Contributing Writer and Illustrator, has a passion for helping people bring their ideas to life through web and book illustration, writing, and animation. In recent years, her work has focused on researching the context and differentiation of technical products and relaying that understanding through appealing and vibrant language and images. She holds a B.A. in Philosophy from the University of California, Berkeley. To contact Maile, visit her on LinkedIn.
You May Also Like