
Written by
StrongDM TeamLast updated on:
September 29, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Cloudflare Access is a Zero Trust Network Access (ZTNA) SaaS application that works with identity providers and endpoint protection platforms to enforce access policies for corporate applications, private IP spaces, and hostnames. It aims to prevent lateral movement and reduce VPN reliance. However, if you're looking to enable fast, secure access to your stack - with complete audit trails - Cloudflare Access might not be the best solution for your requirements. This blog post will cover a few Cloudflare Access alternatives and the pros and cons of each.
Cloudflare Access Overview
Brief product summary
Cloudflare Access is a Zero Trust-based access control solution for SaaS and self-hosted applications (cloud, hybrid, and on-prem). It accelerates remote access and reduces reliance on VPNs via Cloudflare's globally distributed, DDoS-resistant edge network. It connects users with or without a client, enables identity federation across several identity providers, enforces device-aware access, and logs user activity across protected applications.
Use cases
- Secure remote workforces.
- Deliver Zero trust network access.
- VPN replacement.
- Secure SaaS access (CASB).
- Threat protection.
- Manage third-party access.
Pluses
- Routes requests faster with optimized, intelligence-driven routing across Cloudflare's Anycast network.
- Combines ZTNA, Secure Web Gateway, & Remote Browser Isolation into one control plane.
- Single-pass inspection verifies, filters, isolates, and inspects traffic quickly and consistently across the globe because every Cloudflare service is deployed on every datacenter in over 200 locations worldwide.
Minuses
- Requires agents on each resource, which can create scalability challenges in more complex environments..
- While Cloudflare's globally distributed network speeds up requests, it lacks fine-grained access control for cloud accounts like AWS, GCP, or Azure.
- Only offers just-in-time access for SSH, limiting its usefulness for teams managing a wider variety of resources.
- Only provides access logs for databases, SSH, RDP, Kubernetes, and web (no granular activity logs or replays).
- No support for customer-owned encryption keys.
1. StrongDM
Brief product summary
StrongDM is a control plane to manage and monitor access to databases, servers, and Kubernetes. Their zero trust model means instead of distributing access across a combination of VPN, individual database credentials, and SSH keys, StrongDM unifies user management in your existing SSO (Google, Onelogin, Duo, Okta, SAML, etc...) and keeps the underlying credentials hidden. Neither credentials nor keys are accessible by end users. Because StrongDM deconstructs every protocol, it also logs all database queries, complete SSH and RDP sessions, and kubectl activity.
Use cases
- Fine-grained authorization policies and Zero Standing Privileges (ZSP) simplify access management in hybrid and cloud-native environments
- Faster onboarding- no need to provision database credentials, SSH keys, VPN passwords for each new hire.
- Secure off-boarding- suspend SSO access once to revoke all database and server access.
- Automatically adopt security best practices- least privilege, just-in-time access, ephemeral permissions, audit trail.
- Comprehensive logging and reporting- log every permission change, database query, ssh & kubectl command.
- Vendor privileged access management-connect third-party vendors to resources with project-based access that automatically expires.
- Security and compliance teams-simplify HIPAA, SOC 2, SOX, ISO 27001 compliance certification.
- Modern Cloud PAM solution-built to support a variety of cloud networks, including public, private, multi-cloud, and hybrid.
Pluses
- Easy deployment - self-healing mesh network of proxies.
- No change to workflow- use any SQL client, CLI, or desktop BI tool.
- Standardize logs across any database type, Linux or Windows server, and Kubernetes.
- Graphical client for Windows and macOS.
- See and replay all activity with session recordings.
- Manage via a user-friendly web browser interface.
- Simple, straightforward pricing.
- SAML SSO integration available.
Minuses
- Requires continual access to StrongDM API for access to managed resources.
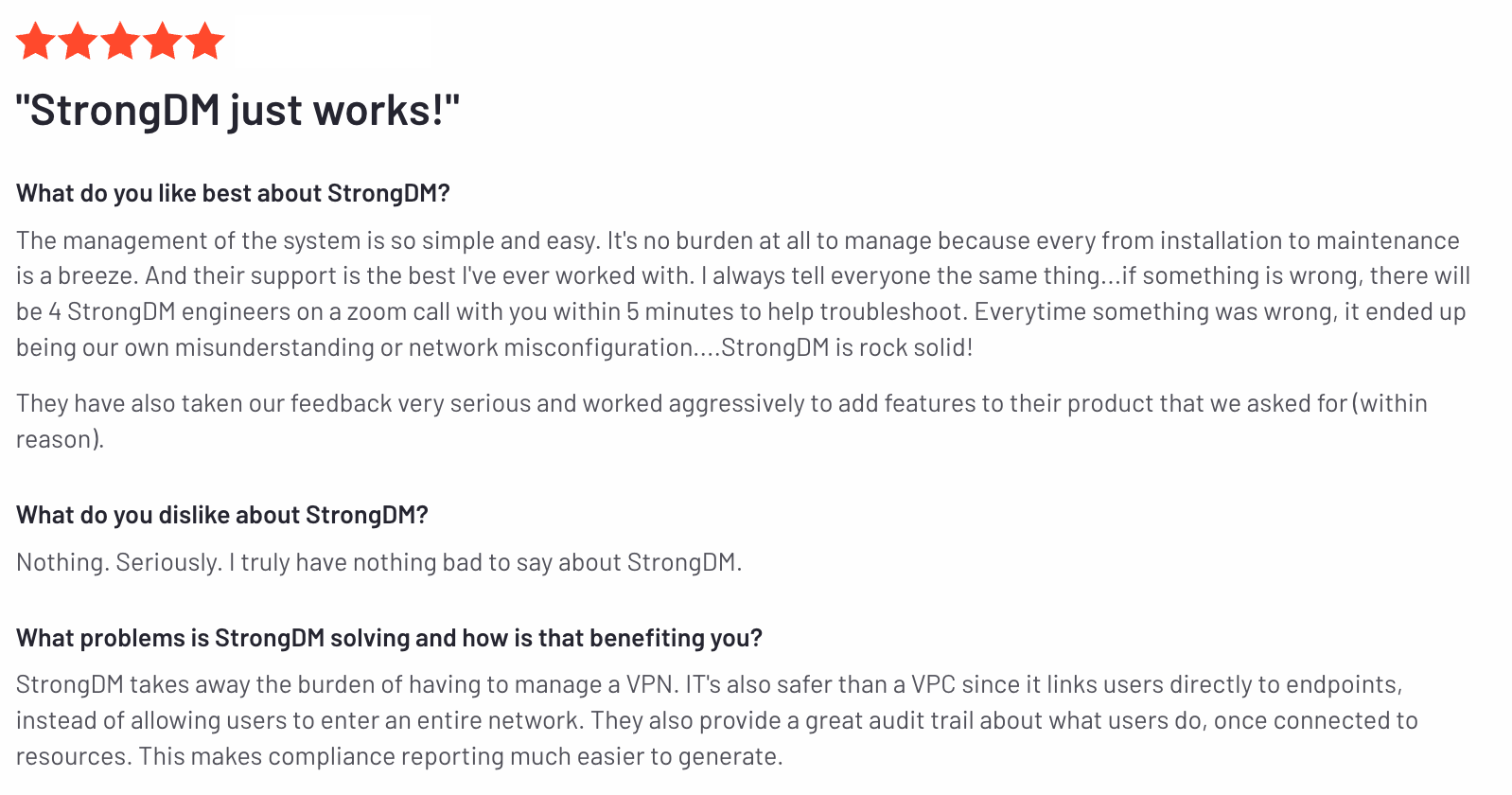
StrongDM’s G2 Reviews
- 4.8 / 5 stars
Read all of StrongDM’s G2 reviews here.
Pricing Information
StrongDM offers simple pricing, including support for all resource types.
Users have the option to sign up for a free 14-day trial.
2. Pomerium
Brief product summary
Pomerium is an "identity-aware proxy" that aims to disrupt the VPN industry. Pomerium works on just about any device, providing remote access management solutions for individuals to enterprise-level companies. Pomerium works as a SASE solution that allows users to manage the authentication and authorization of any internal or third-party application. Essentially, Pomerium adds SSO capabilities to just about any application. However, if you're looking for a more robust way to manage access to databases and Kubernetes clusters, Pomerium might not be the best solution for your needs.
Use cases
- Simplifies workflows for DevOps teams.
- Free end-users from having to use a VPN.
- SASE management to support IT.
- Centralizes access and authentication for applications.
Pluses
- Eliminates need for VPN.
- Cloud or on-prem options available.
- Can add SSO to any application.
- Centralized authentication and authorization.
- Remote access from any location.
Minuses
- Lacks rich customization.
- Not optimized for database or Kubernetes access.
- Lacks comprehensive logging and auditing capabilities that security teams need for compliance or incident response.
- Minimum purchase of 50 users.
- Non-comprehensive list of available integrations.
3. Tailscale
Brief product summary
Tailscale is a zero-configuration virtual private cloud that builds secure networks for WireGuard-encrypted traffic. Tailscale replaces traditional VPNs with a coordination node that acts as a control plane to manage keys and identities. This allows you to create a secure network between cloud resources without the need for firewall configuration changes.
Tailscale is open-source software that scales from single users to enterprise environments in a way that is secure and easy to implement. It integrates with your existing identity provider, making it easy to enforce multi-factor authentication and off-board users who no longer need access.
Use cases
- Connect personal computing environments.
- Create secure point-to-point connections.
- Facilitate remote access from any physical location.
- Establish and enforce security access policies.
- Manage large-scale deployments.
Pluses
- Easy to configure and use.
- Provides audit-compliant logging.
- Integrates with your existing identity provider.
- Works with teams of any size.
- Protects your credentials with automatic key rotation.
Minuses
- Requires some networking expertise.
- RBAC is only available at higher-tier pricing.
- Okta integration is only available at higher-tier pricing.
- SAML SSO integration is only available at higher-tier pricing.
- While Tailscale simplifies secure point-to-point connections, its limited RBAC features and higher-tier pricing for advanced integrations make it less suitable for enterprises needing detailed access control.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
StrongDM Team, Universal Privileged Access Authorization (UPAA), the StrongDM team is building and delivering a Zero Trust Privileged Access Management (PAM), which delivers unparalleled precision in dynamic privileged action control for any type of infrastructure. The frustration-free access stops unsanctioned actions while ensuring continuous compliance.
You May Also Like



