
Written by
John MartinezLast updated on:
November 25, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Microsoft Azure Key Vault is a cryptographic and secrets management solution for storing encryption keys, certificates, and passwords. While known for its interface simplicity and robust security, users should look to Azure Key Vault alternatives if they prioritize employee onboarding automation or need quick and easy implementation. This article evaluates Azure Key Vault competitors regarding security features, pricing, and usability to identify the best alternative options.
Azure Key Vault Overview
Brief product summary
Azure Key Vault is one of Microsoft's many computing and security management products. It's run on the Azure cloud, which allows organizations to maintain cloud security compliance with a wide range of regulatory guidelines and requirements. While primarily used for safeguarding cryptographic and API keys, Azure Key Vault can also enable enterprises to securely manage user passwords, transport layer security/secure sockets layer (TLS/SSL) digital certificates, and access tokens.
Use cases
- Securing keys, access credentials, and tokens used for secure access and verification to cloud applications and online services.
- Automating workflows for key and certificate lifecycle management, renewals, key administration, and credential provisioning to help scale cloud resources.
- Managing keys and secrets stored in hardware security modules (HSMs) to meet Federal Information Processing Standards (FIPS) United States government requirements for NIST compliance.
Pros
- Intuitive graphical unit interface (GUI) while navigating and operating the password, certificate, and key management tools.
- Easy integration process with other Azure tools to boost connectivity.
- Reliable service regarding system uptime, secrets security, and data integrity.
Cons
- Often requires third-party integrations to get key management capabilities typically built into most secrets management tools.
- Can have slow processing times for API responses, key uploads and rotations, and certificate changes.
1. StrongDM
Brief product summary
StrongDM is a centralized control system for identity and access management (IAM) that gives administrators the ability to set granular permissions and obtain end-to-end visibility on servers, applications, clouds, and clusters.
While it's a complete Zero Trust PAM platform, StrongDM is one of the best Azure Key Vault alternatives for credentials and secrets management. Through connectivity with popular secrets management tools, it allows centralized storage and provisioning of user passwords, secure shell (SSH) keys, and other sensitive credential data.
Use cases
- Streamlining employee and vendor onboarding processes through automated provisioning and on-demand least privilege, temporary, and just-in-time access control.
- Centralizing visibility and secrets management by integrating security tools and network resources into one interface.
- Auditing access, privileges, and security controls, for compliance purposes, through logging and reporting infrastructure activity.
Pros
- Straightforward pricing that uses a set, per-user, per-month model.
- Fills in product gaps of Azure Key Vault and other security tools by offering flexible integration options and robust security management features.
- Lets teams automate many access management processes and standardize reporting and logging activities across numerous databases or servers.
- Quick and easy deployment and fast connection with IAM and secrets management tools.
Cons
- Access to managed resources requires continuous access to the StrongDM API.
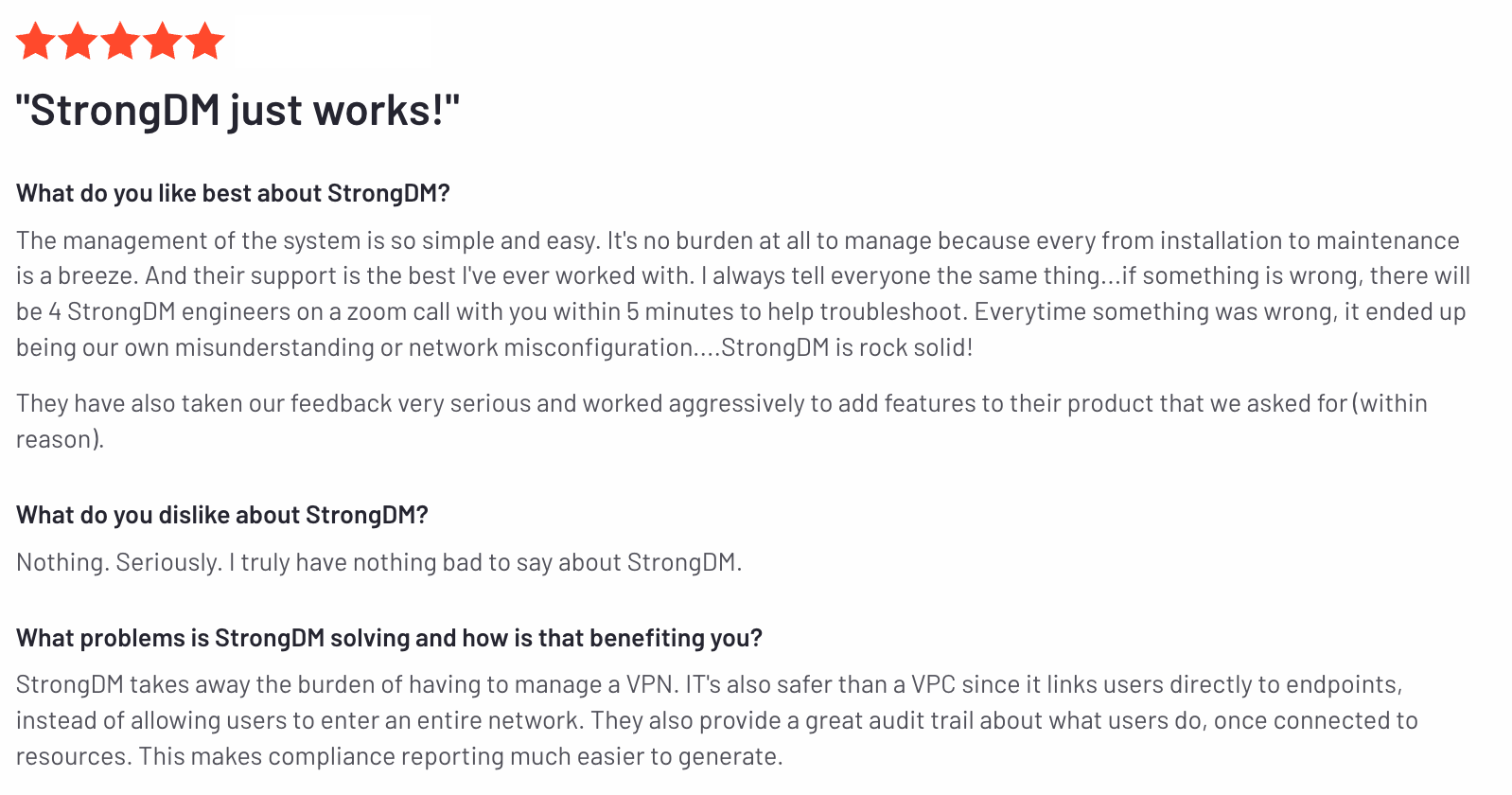
StrongDM’s G2 Reviews
- 4.8 / 5 stars
Read all of StrongDM’s G2 reviews here.
Pricing Information
StrongDM offers simple pricing, including support for all resource types.
Users have the option to sign up for a free 14-day trial.
2. AWS Secrets Manager
Brief product summary
AWS Secrets Manager helps oversee lifecycles and the management of database credentials, API keys, and tokens. It stands out for its overall product intuitiveness and cost scalability, which allows organizations to grow smoothly as the capacity for credential storage and API calls increases. Some of the most prominent features include secrets data storage and encryption, robust secrets-access security controls, automatic rotation for compliance, and simplified replication capabilities.
Use cases
- Securing and monitoring secrets data, activity, and logs in a single platform for security management and auditing purposes.
- Managing IAM permissions for sensitive secrets data, meeting compliance and organizational governance requirements.
- Automating lifecycle processes such as secret rotation and replication while streamlining credential exchanges over AWS services.
Pros
- Lets teams provision access privileges around established IAM policies and consistently audit those privileges.
- Scalable, pay-as-you-go pricing for businesses with growing resource needs.
- Does not require code deployments to automatically rotate secrets.
- Simplifies compliance management with an audit trail on secrets storage and activity.
Cons
- Requires a learning curve for users new to the AWS ecosystem; support isn't ideal unless you enroll in the enterprise support plan.
3. HashiCorp Vault
Brief product summary
The Vault by HashiCorp is a total solution that combines security, storage, and access control for numerous secrets, including passwords, tokens, certificates, and keys. Its dynamic, on-demand secret generation, identity-based authentication, and multi-system capabilities enable organizations to stay secure, particularly in today's modern IT environment. Vault users can store, generate, and access credentials across various resources, like applications, databases, and infrastructure systems.
Use cases
- Automating secrets lifecycle management, public key infrastructure (PKI) workflows, and X.509 certificate generation.
- Securing Kubernetes deployments using granular secrets management within the clusters and technology stack.
- Managing keys, secrets, and sensitive data in a central system to enable secure access to applications, databases, infrastructure systems, and endpoints.
Pros
- Flexibility and customization in terms of available APIs, programming languages, data and secret types, IT resource connections, and access methods.
- Built for a modern-day infrastructure through the use of dynamic credential generation, identity-based tokens, and integration with today's popular DevOps and security tools.
- Great for DevOps teams securely managing secrets for Kubernetes deployments.
Cons
- The complex setup process for product deployment and connecting integrations requires a lot of work to get up and running.
- The pricing structure is complex.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like



