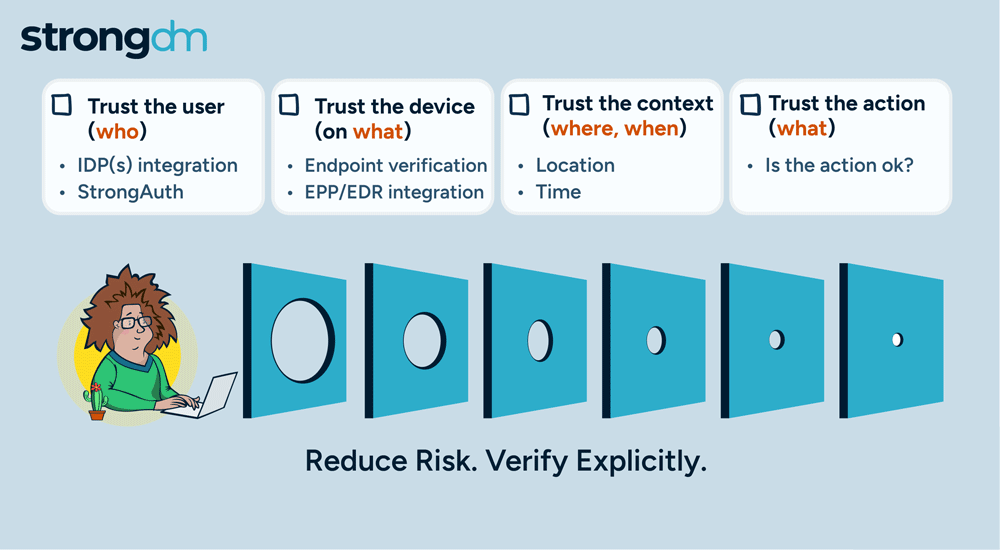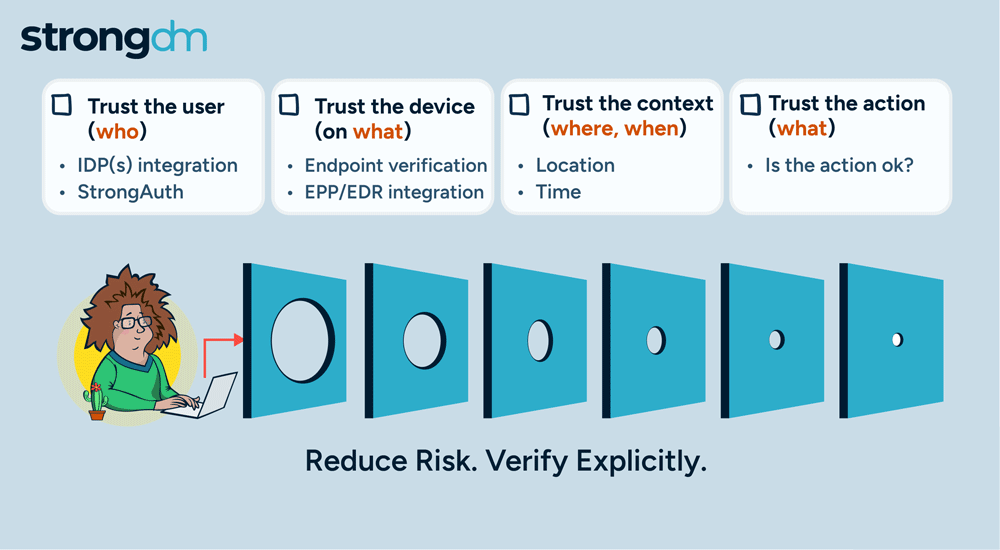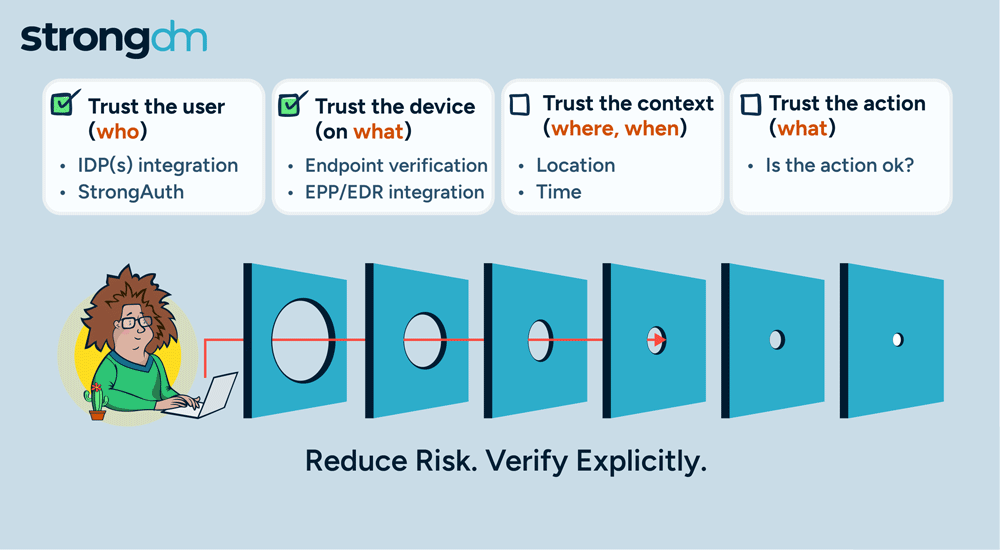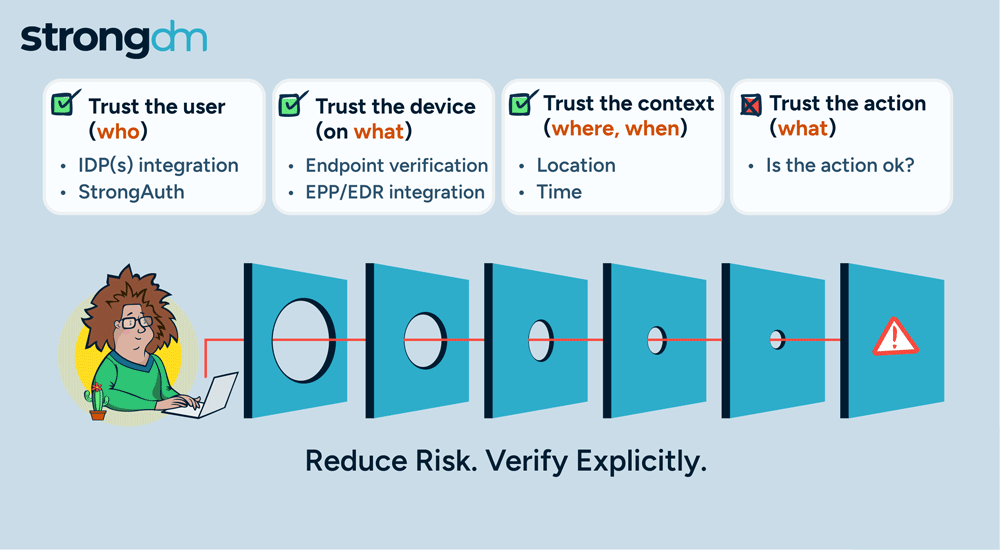
Kubernetes is a popular tool for managing synchronized groups, or clusters, of computers. Users employ it to configure and deploy applications in parallel across clusters on your networks. The kubectl command line tool in Kubernetes lets you send instructions to and receive information from your clusters. This kubectl cheat sheet is a quick guide to getting started with kubectl, including installation, configuration, key commands, and efficiency tips.