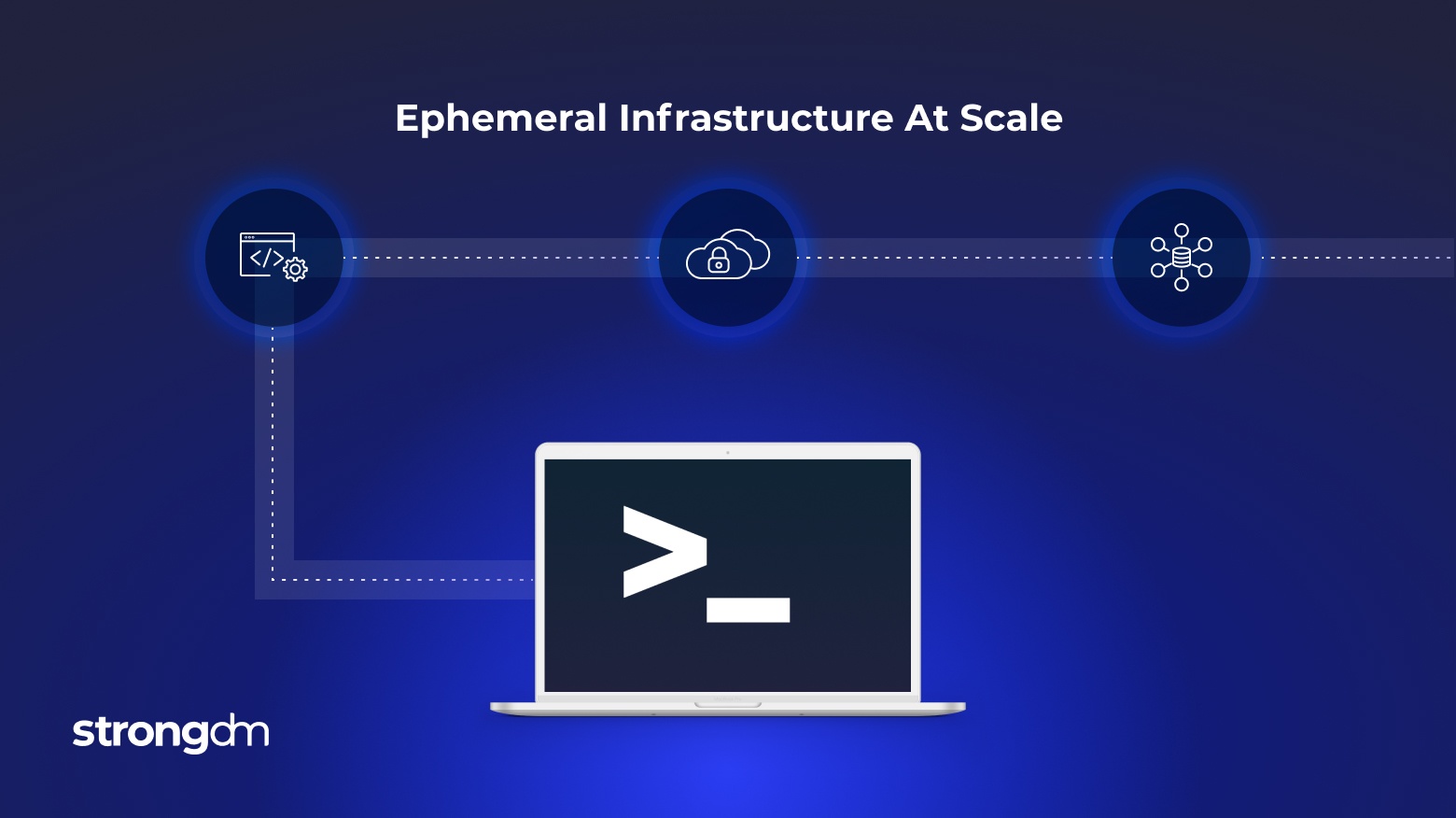
Managing a static fleet of strongDM servers is dead simple. You create the server in the strongDM console, place the public key file on the box, and it’s done! This scales really well for small deployments, but as your fleet grows, the burden of manual tasks grows with it.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

Offboarding technical employees can be a complex and arduous process with a lot of moving parts. The key to successful offboarding is to have a clear understanding of what needs to be done, who does it, and how to monitor for any shenanigans from former employees.

There are a number of ways to automate user provisioning but the real challenge lies in keeping track of those credentials.

As your organization pursues your SOC 2 certification, organization is critical. You will be busy actively managing dozens of ongoing daily tasks, which can bury you in minutiae. But at the same time, you need to keep your high-level compliance goals in focus in order to successfully move your certification over the finish line.

In this post, we will help you get started with a hierarchy to follow, as well as a summary of each individual SOC 2 policy.

A software development lifecycle (SDLC) policy helps your company not suffer a similar fate by ensuring software goes through a testing process, is built as securely as possible, and that all development work is compliant as it relates to any regulatory guidelines and business needs.Here are some primary topics your software development lifecycle policy and software development methodology should cover

In this policy, you will define the controls, monitoring, and removal of physical access to your company’s facilities.

BYOD lets employees use their own smartphones, tablets, or laptops to access company resources and perform work-related tasks, allowing them to work from anywhere. This practice offers advantages like increased productivity and company savings on hardware costs. Employees are often more proficient with their own devices, which can mean a more comfortable work environment and result in higher job satisfaction.

Chris Becker is an SRE at Betterment. Previously, he did similar work on Warby Parker's Infrastructure team. At Betterment, he earned the label APT (advanced persistent threat) thanks to consistently tripping alarms with his peculiar scripts and commands. In this talk, he discusses how Betterment's approach to server access controls evolved as the team grew exponentially. With more people and keys to manage, the SRE team needed to find ways to automate more and reduce the maintenance overhead.

SOC 2 compliance, like so many things related to IT and security, is chock full of terms and acronyms to learn. If you are just getting started with SOC 2, it’s helpful to get familiar with this alphabet soup ahead of time so you can move your compliance efforts forward with confidence. Below is a SOC 2 terminology glossary to get you started:
This article will point you to the core concepts within a security incident response policy (SIRP) so that you understand the purpose of this policy, challenges, and tools to consider when writing your own.
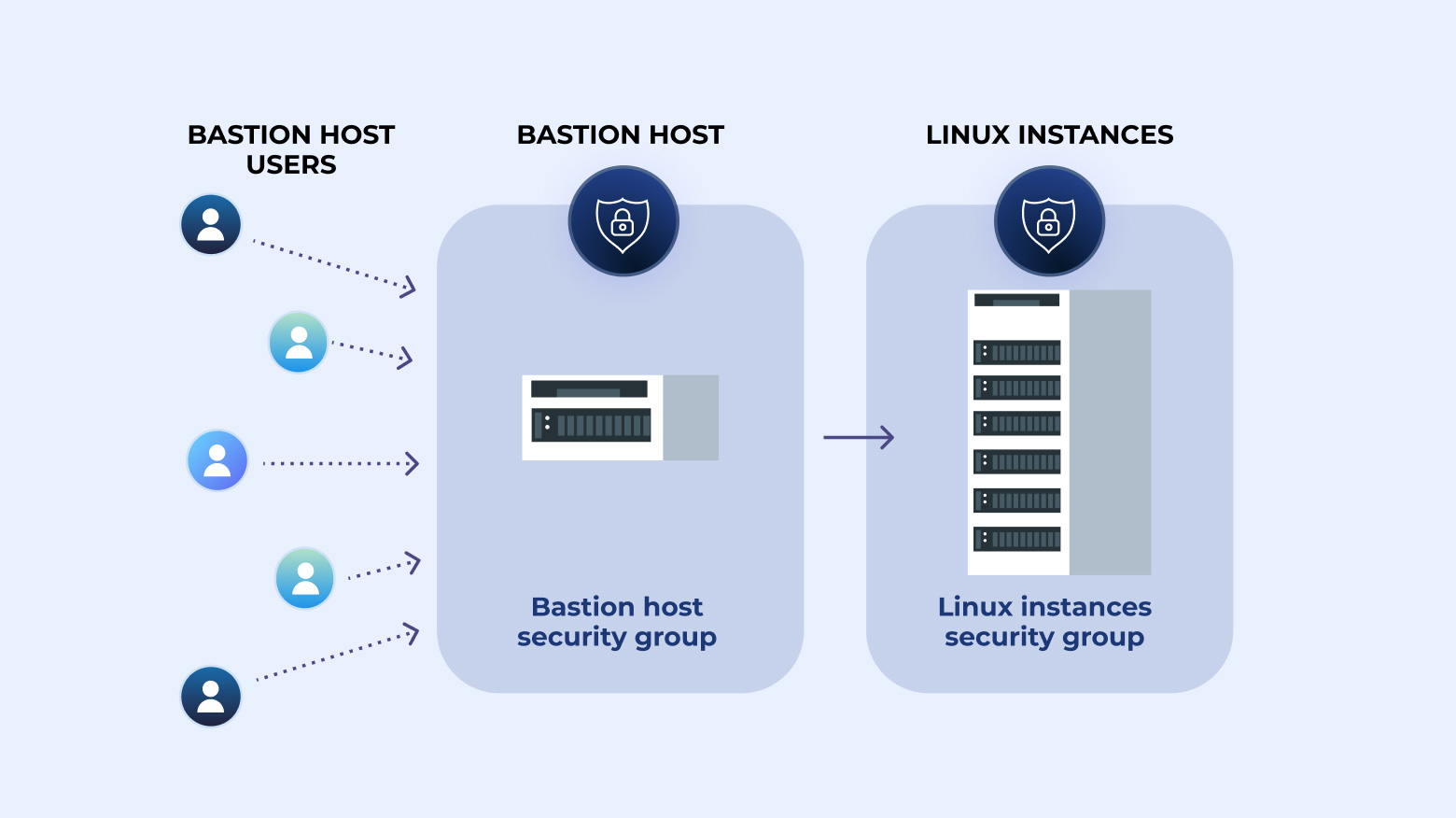
Step-by-step instructions on how to create a bastion host plus how to create an audit trail by logging SSH commands.

This week we are joined by Daniel Leslie at Namely who shares his take on the human side of security, and what security at scale looks like for his team. Max, Justin, and Daniel discuss the 3 core things to good company-wide security: psychological safety, vulnerability, and purpose. You have to address these things in a comprehensive manner.

Data center security refers to the protection of data centers against threats such as cyber-attacks, natural disasters, and human error. The number of data centers has increased significantly over the last decade, and so has the amount of security-related disasters. In 2022, the global data center ...