At Token Security our goal is to teach the core curriculum for modern DevSecOps. Each week we will deep dive with an expert so you walk away with practical advice to apply to your team today. No fluff, no buzzwords. This week Jeff Burkhart, Senior Engineering Director at Zymergen talks code reviews, code review fatigue, and what to do when agile becomes tedious.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
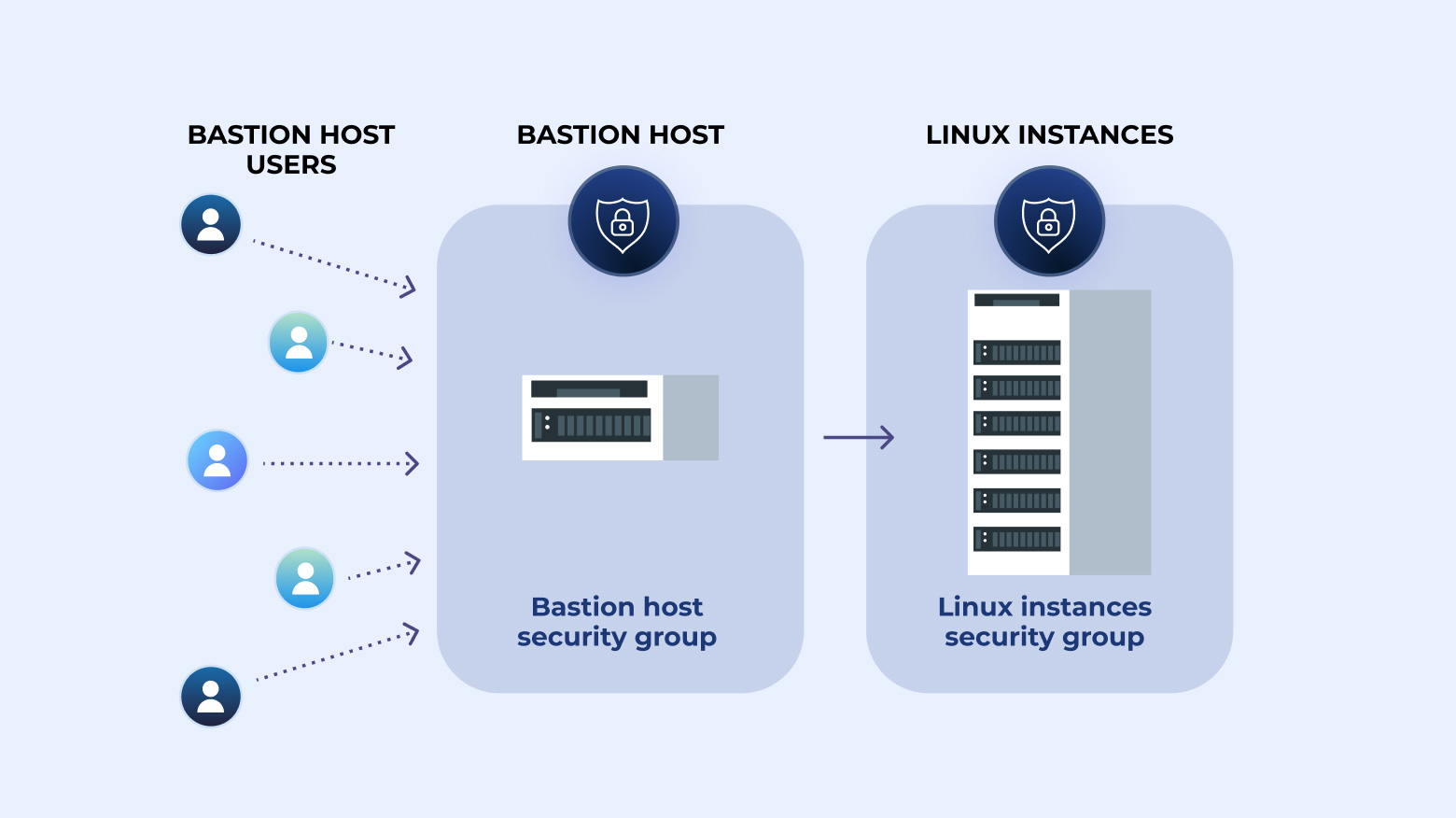
Step-by-step instructions on how to create a bastion host plus how to create an audit trail by logging SSH commands.
This episode Max Saltonstall sits down in Manhattan with Quiessence Phillips, Deputy CISO and Head of Threat Management, City of New York and Colin Ahern, Deputy CISO, City of New York.

Passwords are one of the most common targets for hackers, so it’s imperative that your company enforces a strong password policy. This policy will not only define the requirements of the password itself but the procedure your organization will use to select and securely manage passwords.
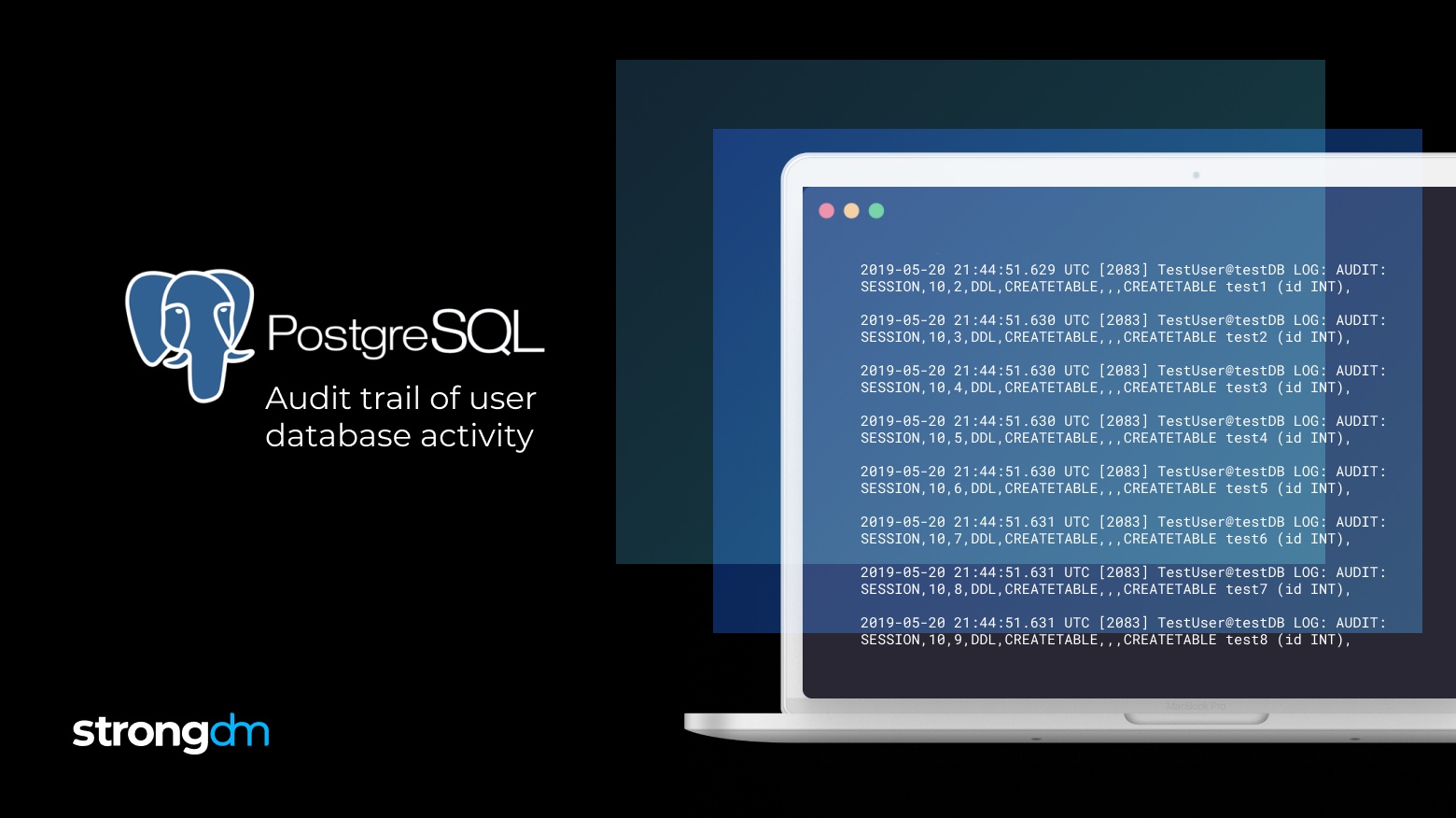
This is the first step to create an audit trail of PostgreSQL logs. Postgres can also output logs to any log destination in CSV by modifying the configuration.


