Discover why traditional secrets management isn't enough. StrongDM Managed Secrets offers vault-agnostic, Zero Trust security with secretless access, dynamic policy enforcement, automated rotation, and unified audits—perfect for complex enterprise environments.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
Security breaches make headlines, while compliance audits keep teams on edge. The pressure to protect data and meet regulatory requirements is mounting—and often, the lines between security and compliance get blurred. Are they the same thing? Are they working in tandem—or pulling in different directions? This post breaks it down: what security and compliance are, how they intersect, where they differ, and most importantly, how your organization can align the two effectively.

As teams grow and roles shift, it’s easy for permissions to get out of sync. That’s where user access reviews come in—they ensure every employee, vendor, or service account has exactly the access they need, and nothing more.Regular reviews reduce risk, prevent privilege creep, and help meet compliance requirements like SOX, ISO 27001, and HIPAA. But manual reviews? They’re slow, messy, and often incomplete.This guide breaks down the essentials of access reviews—what they are, why they matter,
Secrets management is the practice of securely storing, accessing, and controlling digital authentication credentials such as passwords, API keys, certificates, and tokens used by applications and systems. It ensures that sensitive information is protected from unauthorized access, while supporting automation, compliance, and security across modern infrastructure.
Legacy security models can’t protect modern financial systems. Continuous Authorization ensures real-time, risk-based access control for true Zero Trust. Learn how to secure your cloud and hybrid environments today.

This guide breaks down the top cloud database solutions reshaping how organizations store, manage, and scale data. From relational databases to NoSQL options, we’ll cover what matters most when choosing the right solution for your needs. By the end, you’ll understand how modern cloud databases drive scalability and performance—and which one is the best fit for your organization.

Both StrongDM and CyberArk are privileged access management solutions to provide secure access to backend infrastructure. While there are many similarities between the two solutions, there are also some key differences.
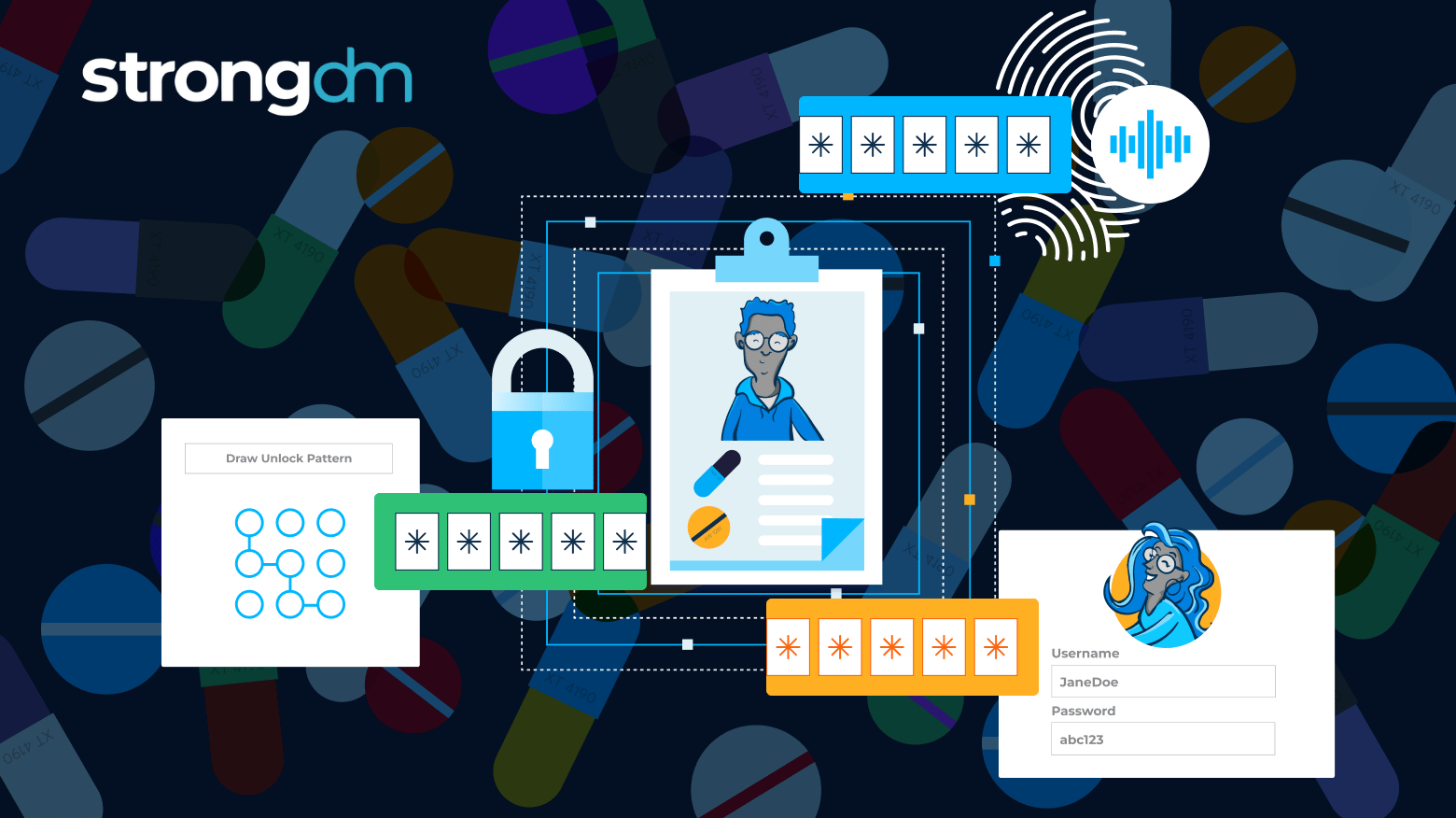
The HIPAA Multi-Factor Authentication (MFA) requirement is a security measure that requires users to verify their identity using at least two different factors—such as something they know (a password), something they have (a smartphone or token), or something they are (a fingerprint)—to access systems containing electronic Protected Health Information (ePHI). This additional layer of security is designed to protect sensitive healthcare data from unauthorized access, even if one credential is
I’ll spare you the “I drink your milkshake” tropes, but we all face a sobering reality: there will be breaches in 2025. Breaches aren’t a question of “if” anymore—they’re a question of “when” and “how bad.” It’s a foregone conclusion, like taxes or the 37th season of Grey’s Anatomy. But here’s the good news: knowing the inevitability of breaches gives us the perfect opportunity to prepare, if we have the will – and strategy – oh, and tools – to do it. And no, I’m not talking about the “build a
Managing access to critical infrastructure is a challenge for many organizations. Legacy tools often struggle to keep up, creating inefficiencies, security gaps, and frustration. StrongDM offers a modern solution that simplifies access management, strengthens security, and improves workflows. In this post, we’ll explore 13 real-world examples of how StrongDM helps teams solve access challenges and achieve their goals.

Network Level Authentication (NLA) is a security feature of Microsoft’s Remote Desktop Protocol (RDP) that requires users to authenticate before establishing a remote session. By enforcing this pre-authentication step, NLA reduces the risk of unauthorized access, conserves server resources, and protects against attacks like credential interception and denial of service. While effective in securing RDP sessions, NLA is limited to a single protocol, lacks flexibility, and can add complexity in

Enterprises seek ways to effectively address the needs of dynamic, always-evolving cloud infrastructures, and StrongDM has developed a platform that is designed with built-in capabilities to support continuous compliance in AWS environments.
![IP Whitelisting: Meaning, Alternatives & More [2026 Guide]](https://discover.strongdm.com/hubfs/ip-whitelisting.jpg)
IP whitelisting is a security strategy that restricts access to a network/system to a specified list of trusted IP addresses. This approach ensures that only individuals using the approved addresses can access certain resources.