Let’s face it. If you work with any type of technology, you know that all software, hardware, and networking gear can fail in weird and unexpected ways. That’s why it’s critical that your technology stack has no single point of failure in your environment. At StrongDM, that means having options in a “break glass” scenario. We firmly believe that this is a requirement for the responsible operation of modern technology. So here’s how we tackle it.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

The Federal Financial Institutions Examination Council (FFIEC) places significant emphasis on user security controls and the mitigation of potential risks posed by privileged users. To comply with FFIEC guidelines and safeguard critical systems, strong access management measures are crucial.
There is no shortage of complex and nuanced topics in the field of IT. After 16 years in the industry, access management continues to be one of the most sensitive and controversial aspects of the job. But it’s not the technology that makes it difficult. It’s the people.

Organizations must meet comprehensive cyber insurance requirements to qualify for coverage. This article defines seven key cybersecurity insurance requirements. Adhering to these requirements will ensure you’ve covered your bases in case of a claim.

We constantly hear about the gender gap in technology. Whether it’s the shortage of female founders and CEOs, claims of discrimination, or the comparatively small number of women in computer science majors, it seems that the issue has become a regular feature story in the news cycle. Disagreement over how to respond abounds on social media, in editorials, and not infrequently within tech companies themselves.

We constantly hear about the gender gap in technology. Whether it’s the shortage of female founders and CEOs, claims of discrimination, or the comparatively small number of women in computer science majors, it seems that the issue has become a regular feature story in the news cycle. Disagreement over how to respond abounds on social media, in editorials, and not infrequently within tech companies themselves.
Networking decisions can be challenging, and no one wants to make a costly mistake. The information in this article will help you understand how SD-WAN and VPN compare, so you can decide which option fits your organization best. You can find a networking solution that provides your employees with a secure internet connection while meeting your business needs and budget.

Cloud computing isn’t a trend, it’s how businesses grow. In 2022, most enterprises said they use cloud services, and more than half say they plan to spend even more on cloud applications and infrastructure in 2023. Cloud scalability offers flexibility at a reasonable price, making it an important business tool. In this article we’ll discuss what scalability is in cloud computing, the benefits of cloud computing scalability, and discuss ways businesses use scalability.
At any given moment, your network may be under attack. Are you prepared? Broken API authentication can expose your data and let hackers in. A data breach compromises an organization as well as its customers, destroying trust and losing customers. Don’t worry, though. The API security best practices in this article help you protect your network from malicious attacks.

A continuous integration, continuous delivery pipeline—or CI/CD pipeline—is a process workflow companies use to streamline and automate software development. A CI/CD pipeline automatically builds and tests code changes to detect bugs before the new code is merged and deployed.

Cloud native security solutions can help organizations like yours protect your cloud resources, no matter when you transitioned to the cloud. Here’s everything you need to know about integrating cloud native security.

Today there are numerous technologies and solutions to help organizations create an active onboarding experience for employees. But what do the employee onboarding statistics say about the process?
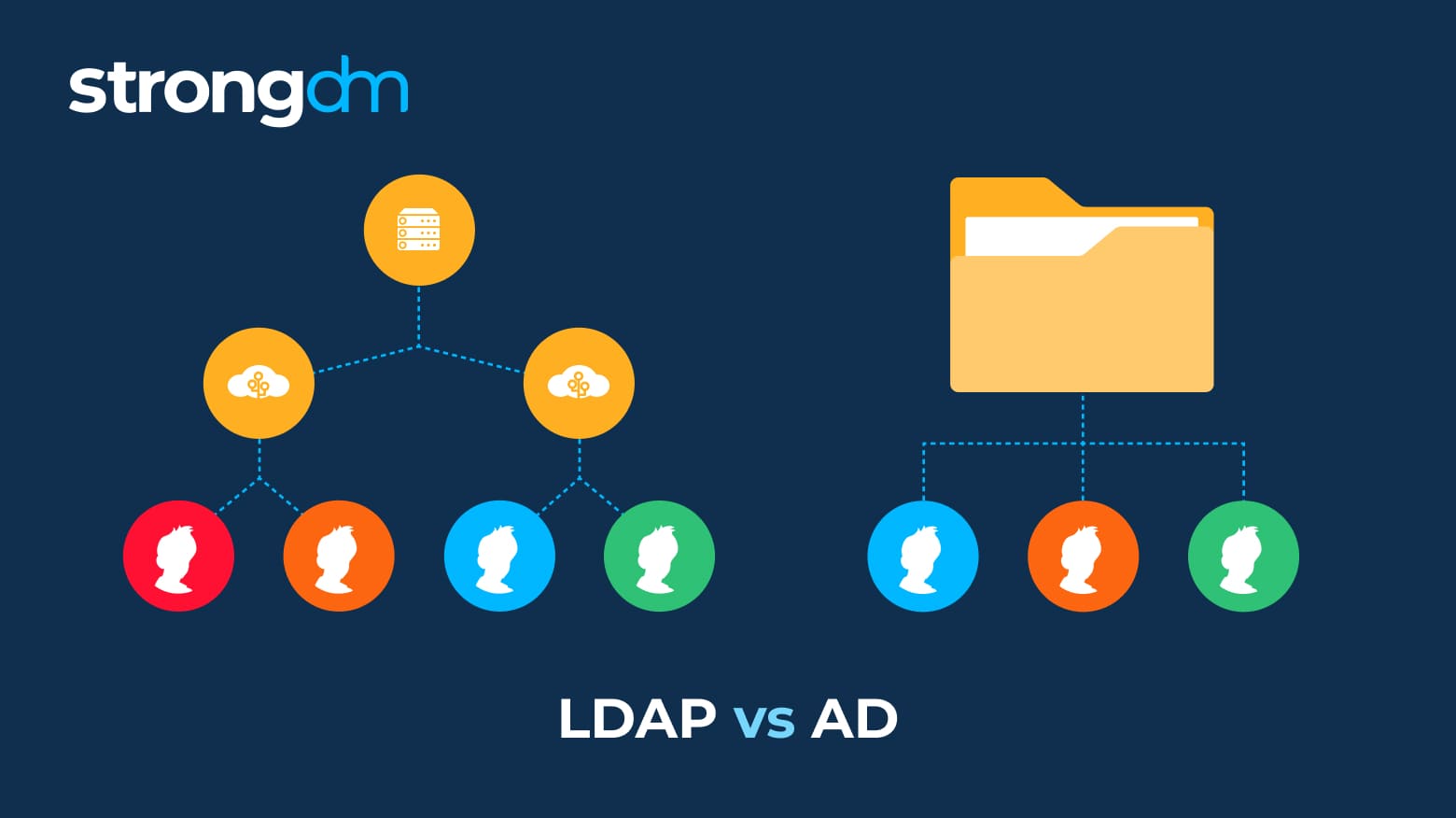
Struggling to understand the difference between Active Directory and LDAP? Don't worry, we’ll make it simple. These are just two among many methods that can provide secure user authentication and authorization. The information in this article will help you decide if LDAP or Active Directory is right for your organization. Robust security and a seamless user experience are attainable, and you can have both!

In this article, we’ll take a deep dive into attack vectors. You’ll learn what they are, the most common types, how they’re used, and why hackers continually use them to exploit vulnerabilities. By the end of this article, you'll have a thorough understanding of the fifteen most common types of attack vectors and what you can do to prevent your organization from falling victim to them.