Zero Trust Data Protection isn't just the best way to safeguard your data — given today's advanced threat landscape, it's the only way. Assuming inherent trust just because an access request is inside your network is just asking for a breach. By implementing the latest tactics in authentication, network segmentation, encryption, access controls, and continuous monitoring, ZT data security takes the opposite approach.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
With so many advanced cyber attackers lurking on the threat landscape, a simple password is no longer enough to safeguard your sensitive data. There are many reasons to adopt MFA for your business. It supplements your security by requiring additional information from users upon their access requests—and it significantly reduces your risk of incurring a breach. Several multi-factor authentication methods are available, with varying strengths and weaknesses. Be sure to compare the differences
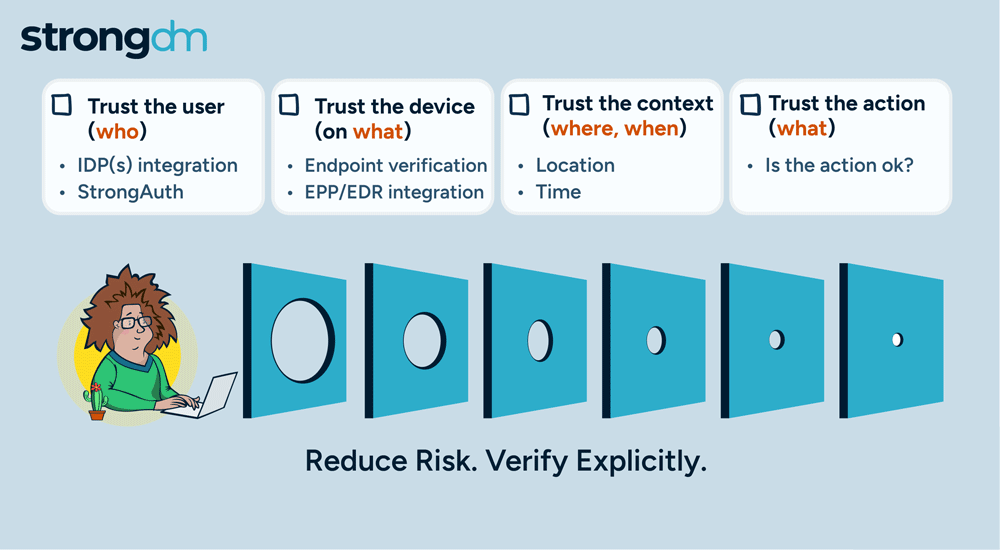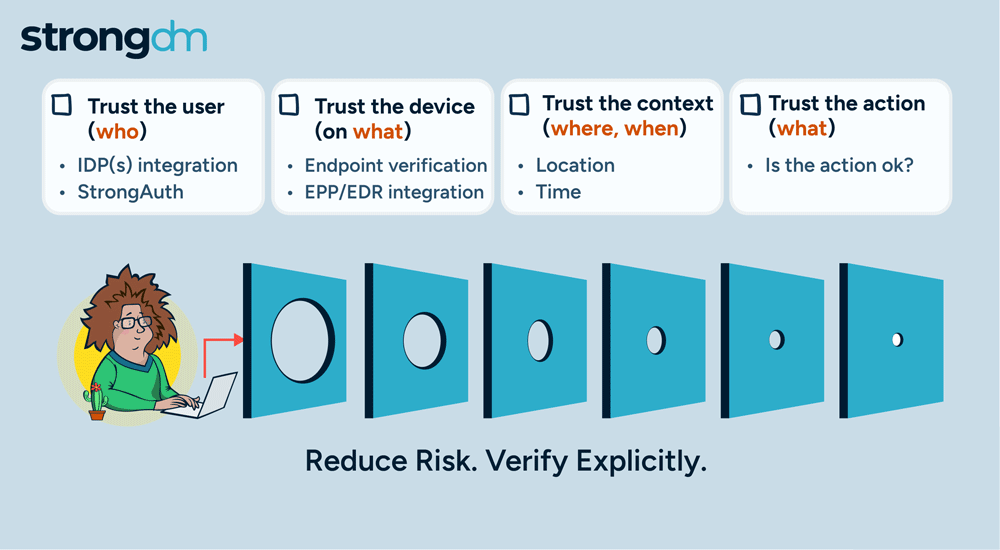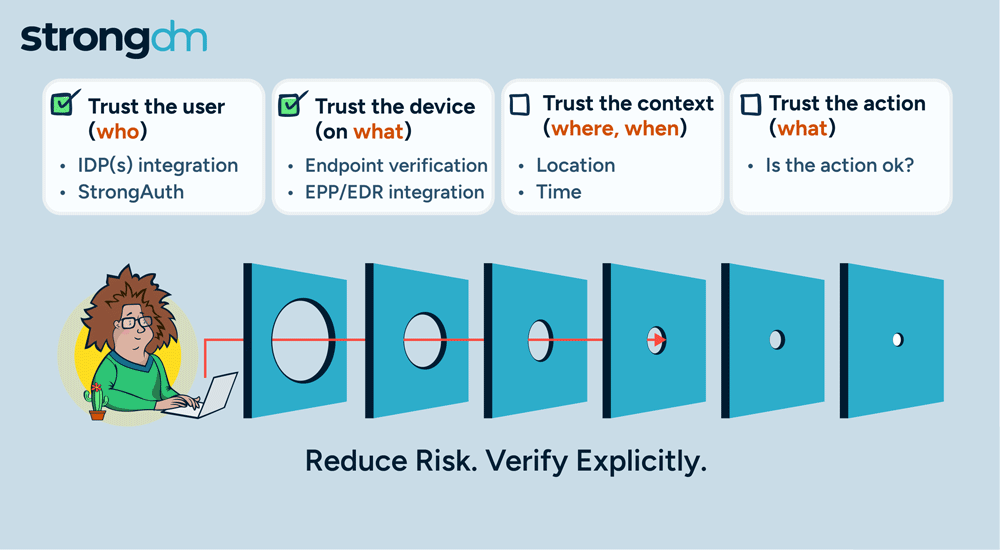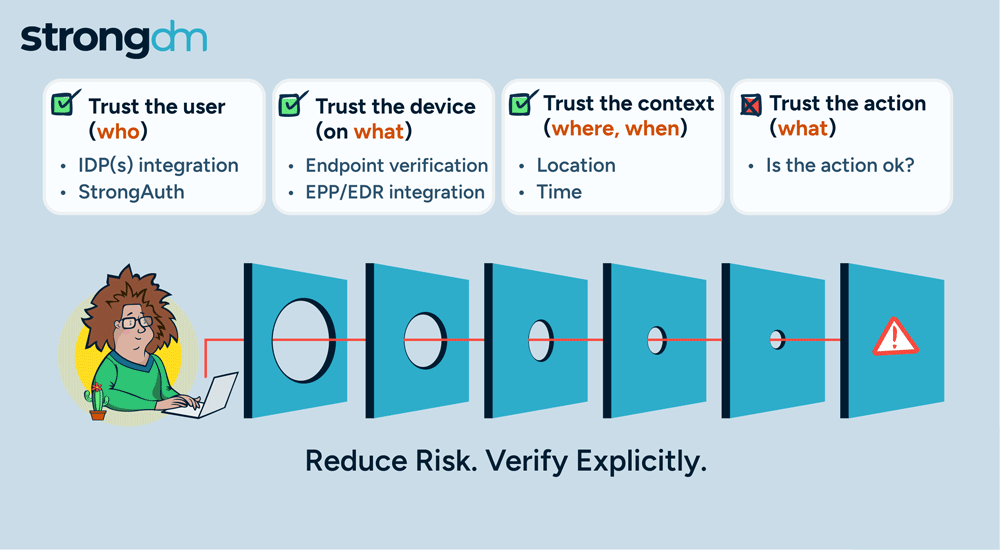
Access is no longer the primary challenge in enterprise security; it's the actions of users that are most aligned with managing risk. By focusing on how actions are authorized, StrongDM is giving customers a more effective approach to enterprise security. Our policy-based action control ensures that, in addition to access, every user action is scrutinized, delivering a higher level of security tailored to meet the complex demands of modern enterprises.

SQL injection attacks remain one of the most prevalent and dangerous threats to database security. These attacks can compromise sensitive data, disrupt operations, and cause significant financial and reputational damage. Understanding how to prevent SQL injection attacks will help you foster a security-conscious organizational culture.

Internet of Things (IoT) devices form the backbone of many modern businesses, facilitating operations, collecting valuable data, and enhancing efficiency. However, the widespread deployment of these devices creates numerous entry points for potential attackers. Without robust security measures, you risk exposing critical systems and sensitive information to malicious actors.
Traditional security measures like simple virus protection, firewalls, and web and email filtering are no longer sufficient to safeguard against the sophisticated tactics used by modern cybercriminals. This heightened complexity means you must implement advanced defense mechanisms that go beyond basic protections, ensuring a resilient and adaptive cybersecurity posture.
Get ready to secure everything and anything with MFA. Easily combine security checks such as device trust and geo-location. With StrongDM you can MFA all resources (e.g., multiple clouds, diverse databases, or critical applications, etc.) without changing your applications’ code or infrastructure.

This article investigates MFA fatigue attacks. We'll explain how they work, why they're effective, and who they typically target. We'll also provide real-life examples to help your team detect and prevent these threats. You'll leave with a clear understanding of MFA fatigue attacks and tips on how to shore up your cloud security to defend against them.
There are multiple situations where it is necessary to terminate a process – for example, when the program does not respond or freezes, when there are detected traces of the malicious work of an application, or when one process consumes far too many system resources, and this list goes on. Learning how to kill a process properly is a vital skill that can help keep your various systems healthy and functioning optimally.
Understanding the core differences between a Zero Trust architecture and a Virtual Private Network (VPN) is an important step in shaping your organization’s cybersecurity strategy. Zero Trust and VPNs offer distinct approaches to security; knowing their functionalities and security philosophies helps you understand when to select one or the other to protect your data effectively—a strategic necessity for robust cybersecurity.

Continuous compliance is the ongoing process of ensuring that an organization consistently adheres to regulatory standards and internal policies for its systems, applications, employees, partners, and engagement with stakeholders. It involves continuous monitoring, auditing, and real-time updates of both technology and human behavior to maintain compliance with government and industry standards frameworks.

This article explores essential Linux commands, ranging from navigation, file management, text manipulation, system maintenance, user management, process management and more.

In essence, legacy PAM solutions over-index on access. StrongDM uses the principles of Zero Trust to evaluate and govern every action, no matter how minor - where each command, query, or configuration change is evaluated in real-time against dynamic policies that adapt to the context of the user, the sensitivity of the action, and the prevailing threat landscape.