Fine-grained access control systems determine a user’s access rights—to infrastructure, data, or resources, for example—once past initial authentication. Unlike coarse-grained access control (CGAC), which relies on a single factor, such as role, to grant access, FGAC relies on multiple factors. For example, it may consider policies (policy-based access control, or PBAC), attributes (attribute-based access control, or RBAC), or a user’s behavior in a certain context (behavior-based access
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Policy
- Compliance
- SOC 2
- Databases
- Authentication
- Identity and Access Management
- Compare
- Team
- Engineering
- Product
- Integrations
- Kubernetes
- AWS
- Productivity
- Podcasts
- Observability
- SSH
- HIPAA
- ISO 27001
- Dynamic Access Management
- Role-Based Access Control
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
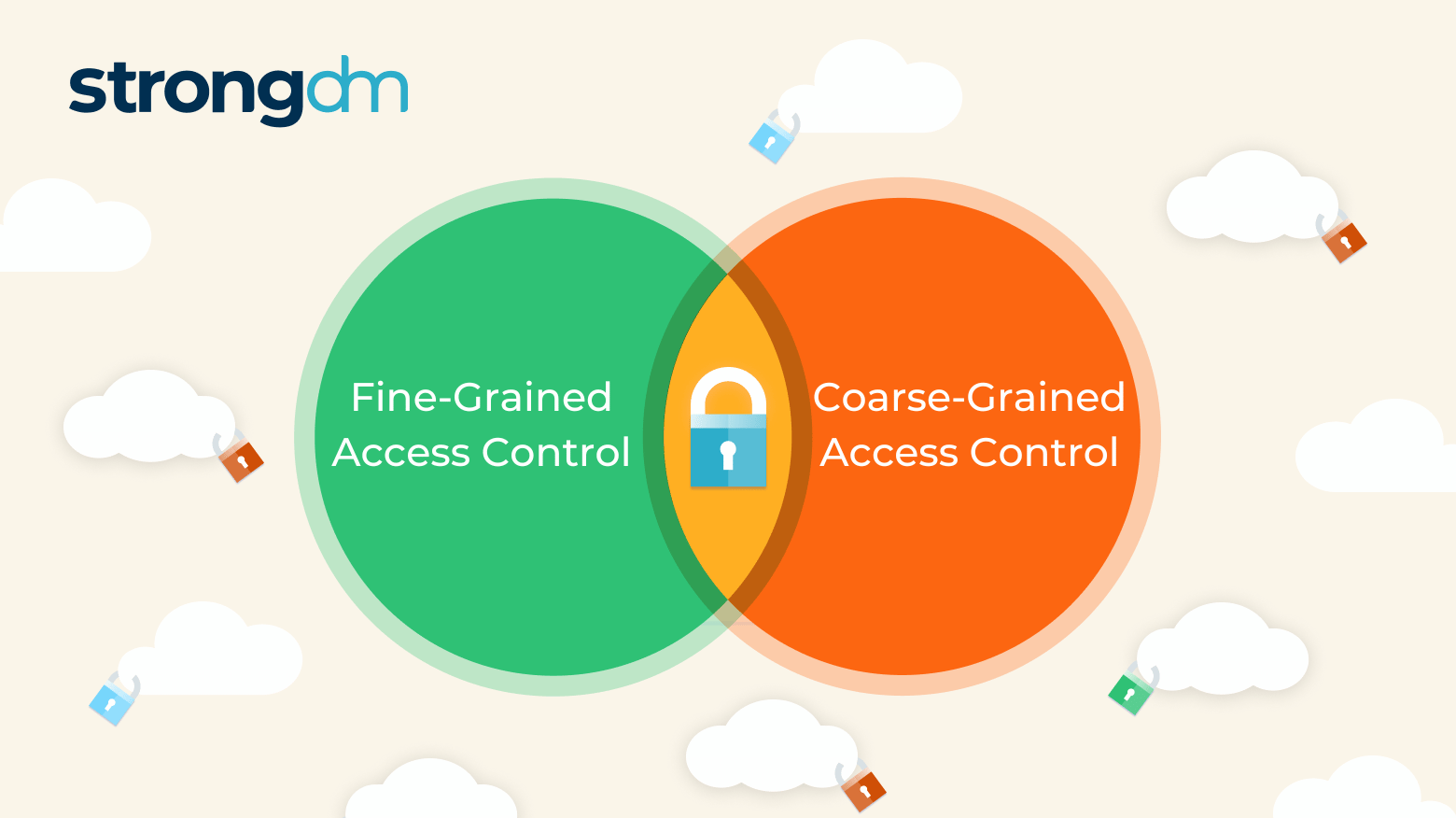
If credentials fall into the wrong hands, intruders may enter a network and launch a disastrous attack. In fact, 46% of cybersecurity incidents involve authentication credentials, according to the Verizon 2022 Data Breach Investigations Report. Organizations have two general ways to determine someone’s access rights once past initial authentication: Coarse-grained access control (CGAC), which relies on a single factor, and fine-grained access control (FGAC), which relies on multiple factors.

In this article, we will look at three important types of access control in security. You’ll learn about the different types of access control, how they work, and their pros and cons. By the end of this article, you’ll understand what type of access control will work best for your organization and meet your security needs.

Learn how Remote Identities helps you leverage SSH and k8s capabilities to capitalize on infrastructure workflow investments you’ve already made.

With the release of tighter integrations with Okta and Azure AD (or any SCIM-based directory service for that matter), you now have the ability to manage just-in-time, least-privilege access to your critical infrastructure right from your preferred identity provider (IdP), dramatically reducing the time needed to approve requests and grant access.
strongDM asked 600 DevOps pros about the state of infrastructure access today. Their response? It’s out of control. Here’s an overview of our results.
This article presents an overview of RBAC vs. ABAC, plus several additional models of access control, including PBAC, ACL, and DAC. You will learn what these methods are, how they differ from each other, and the pros and cons of each.
Here’s the scenario: On one side, you’re inundated with requests to provide access to critical infrastructure in order to enable teams to do their jobs; on the other side, you’re tasked with auditing access and ensuring that security to those systems is solid.

Discovering “who has access to what” is critical for zero trust and PAM. These six steps will get you started with Access Management.
Role & Access Discovery aims to answer “Does this person, in this role, need access to that system?” Learn why this is a critical part of access management.


